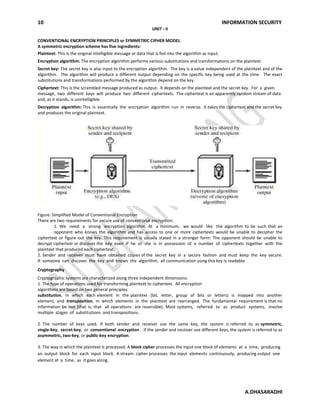
1. The document discusses the principles of symmetric encryption, including the use of a secret key, plaintext, ciphertext, encryption and decryption algorithms.
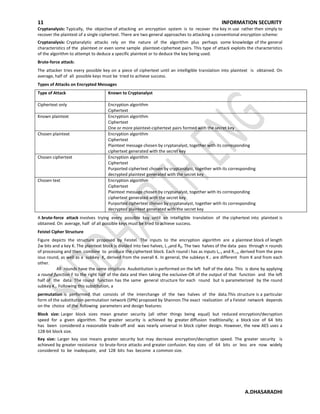
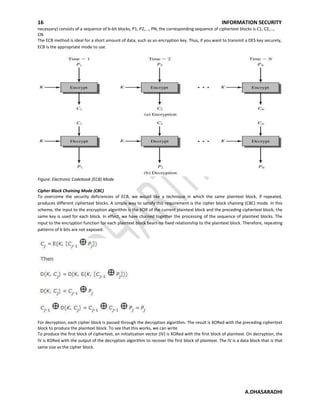
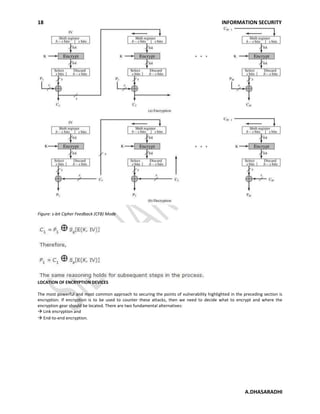
2. It describes the Feistel cipher structure, which uses rounds of processing and subkeys to encrypt plaintext blocks. Parameters like block size, key size, and number of rounds determine the security level.
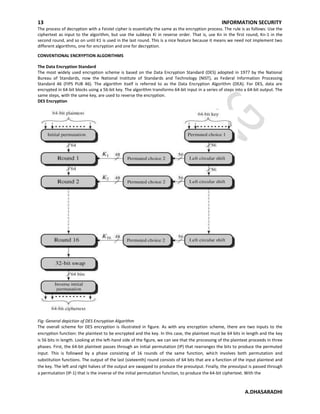
3. The Data Encryption Standard (DES) algorithm is discussed as the most widely used conventional encryption scheme. It uses a 56-bit key to encrypt 64-bit blocks via initial permutation, multiple rounds of processing, and final permutation.