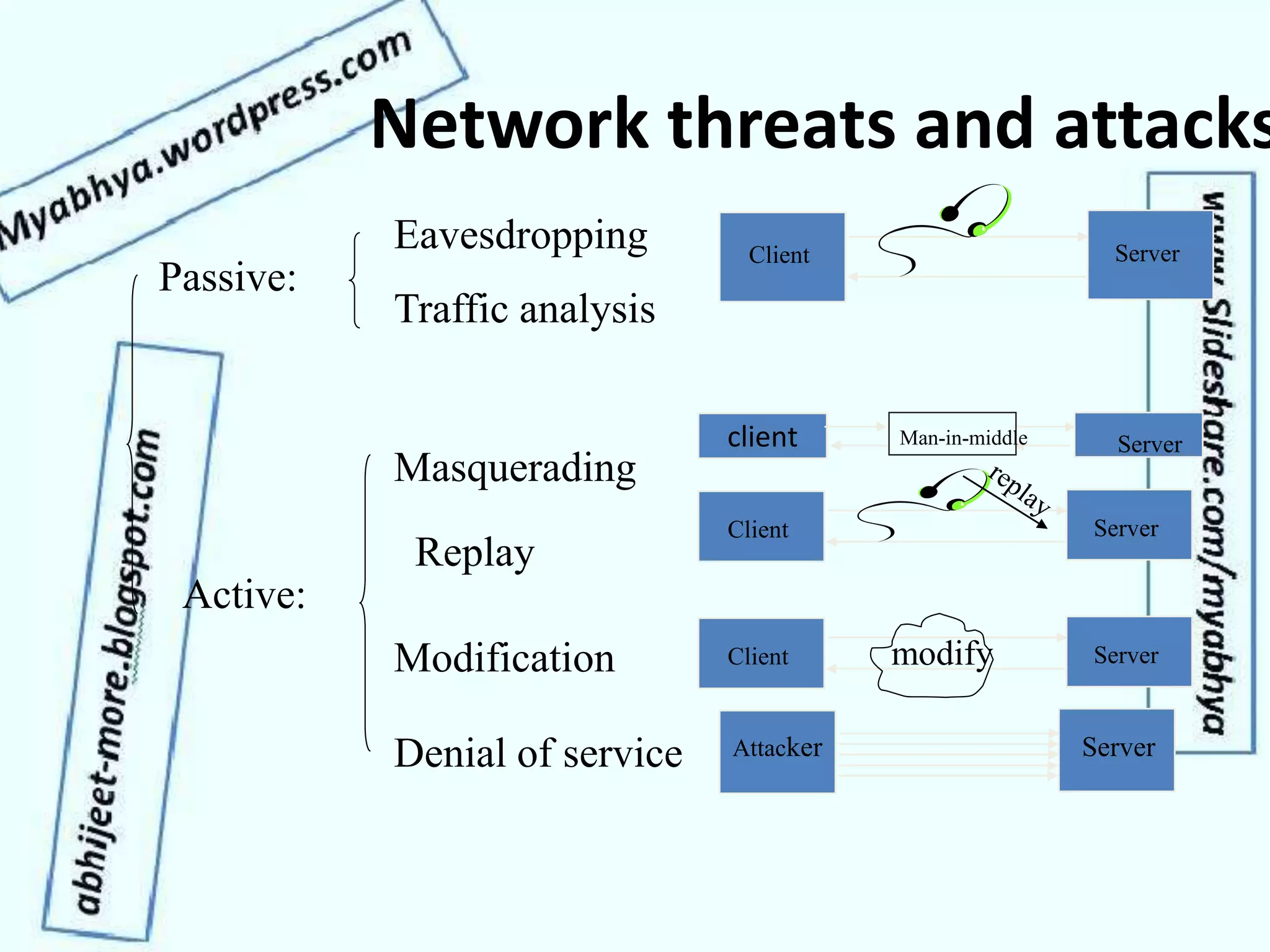
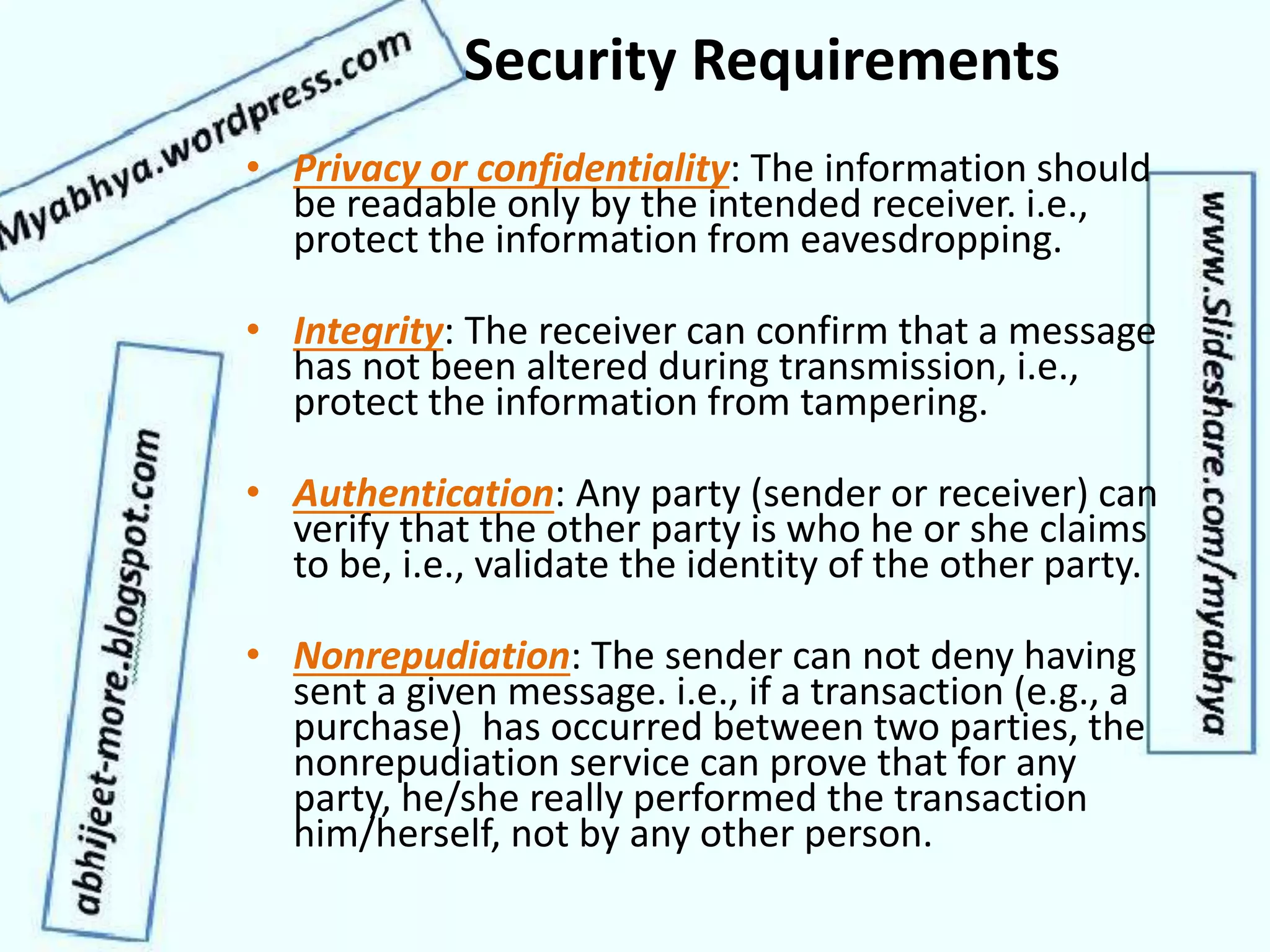
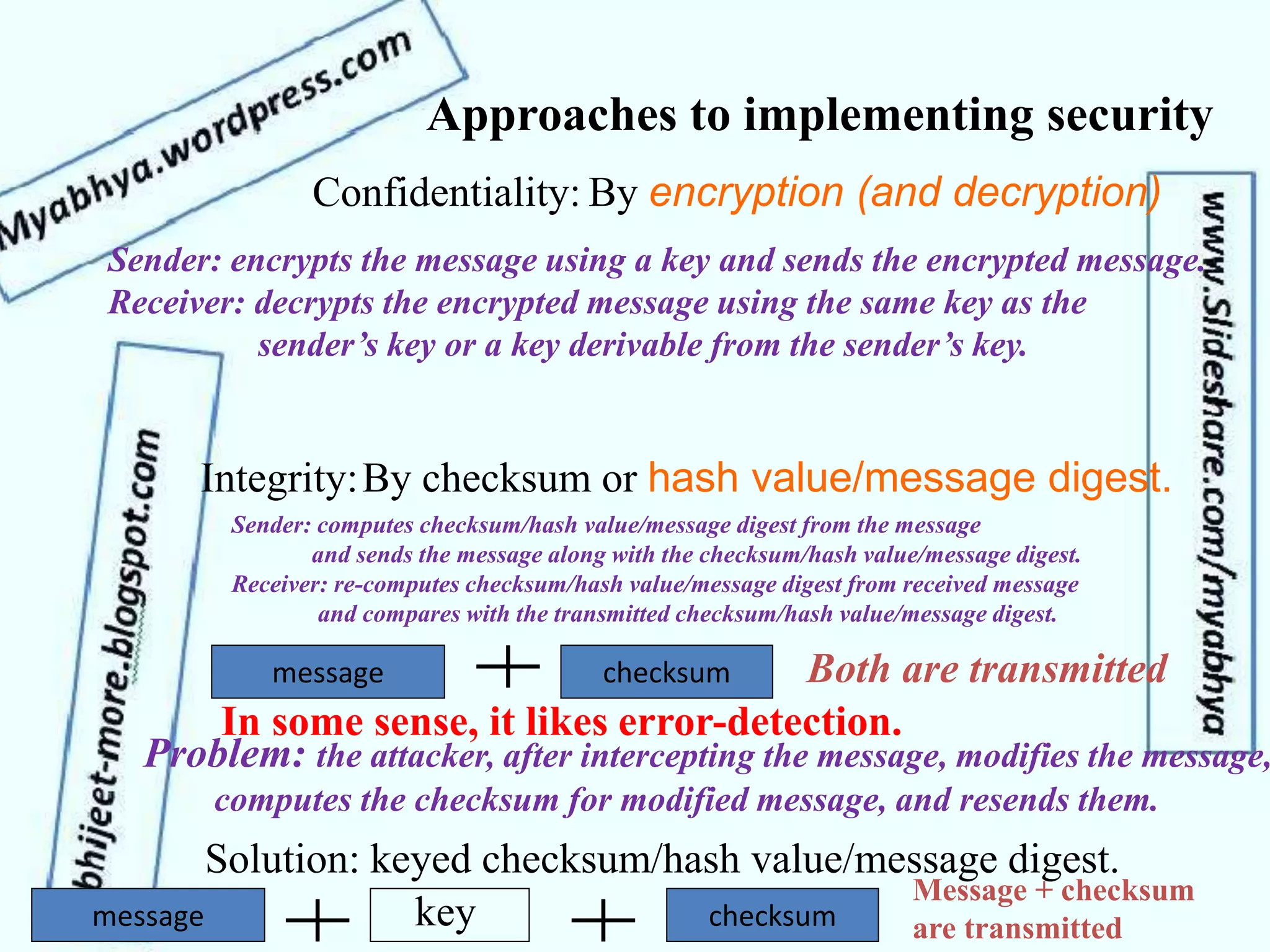
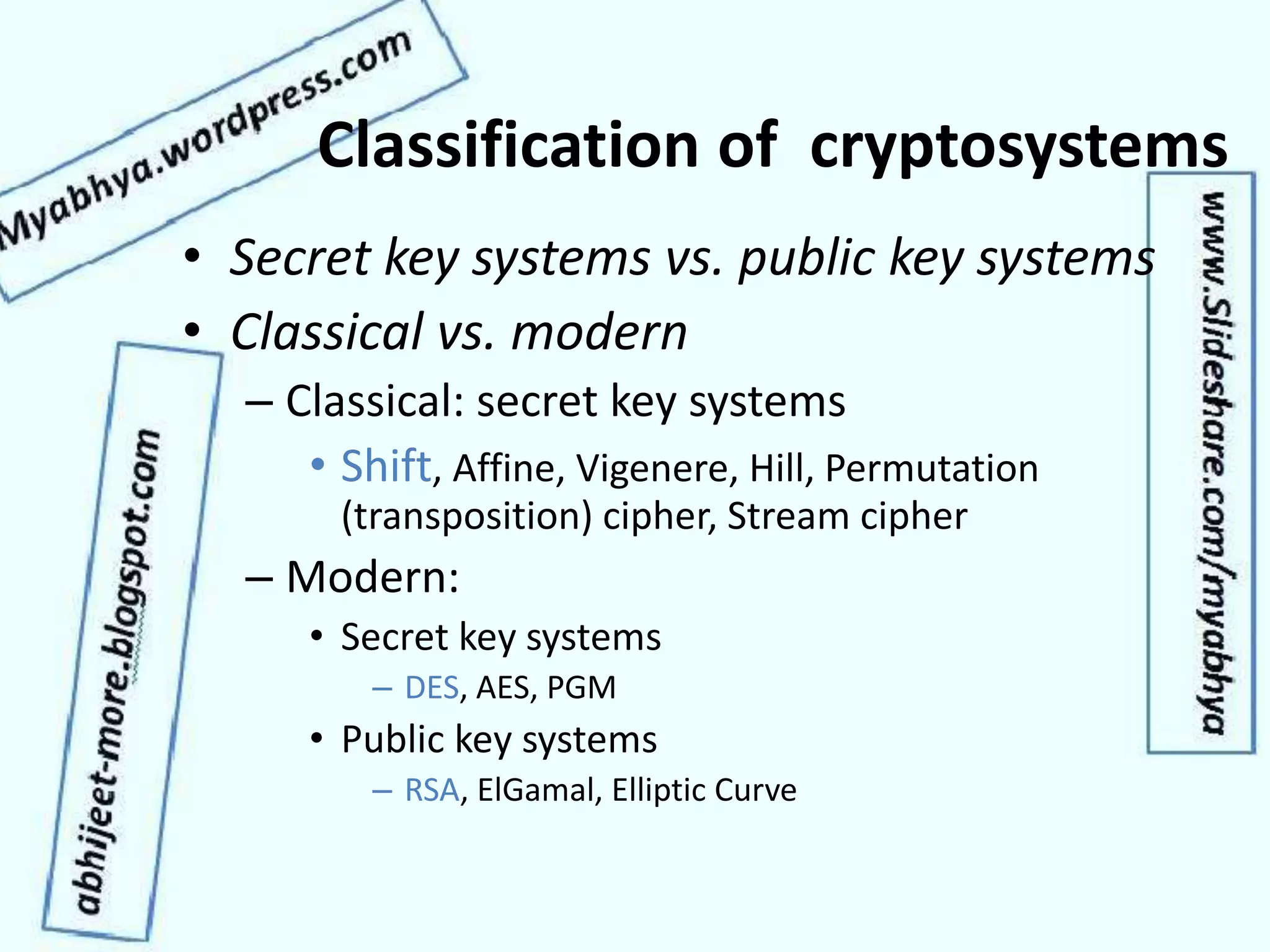
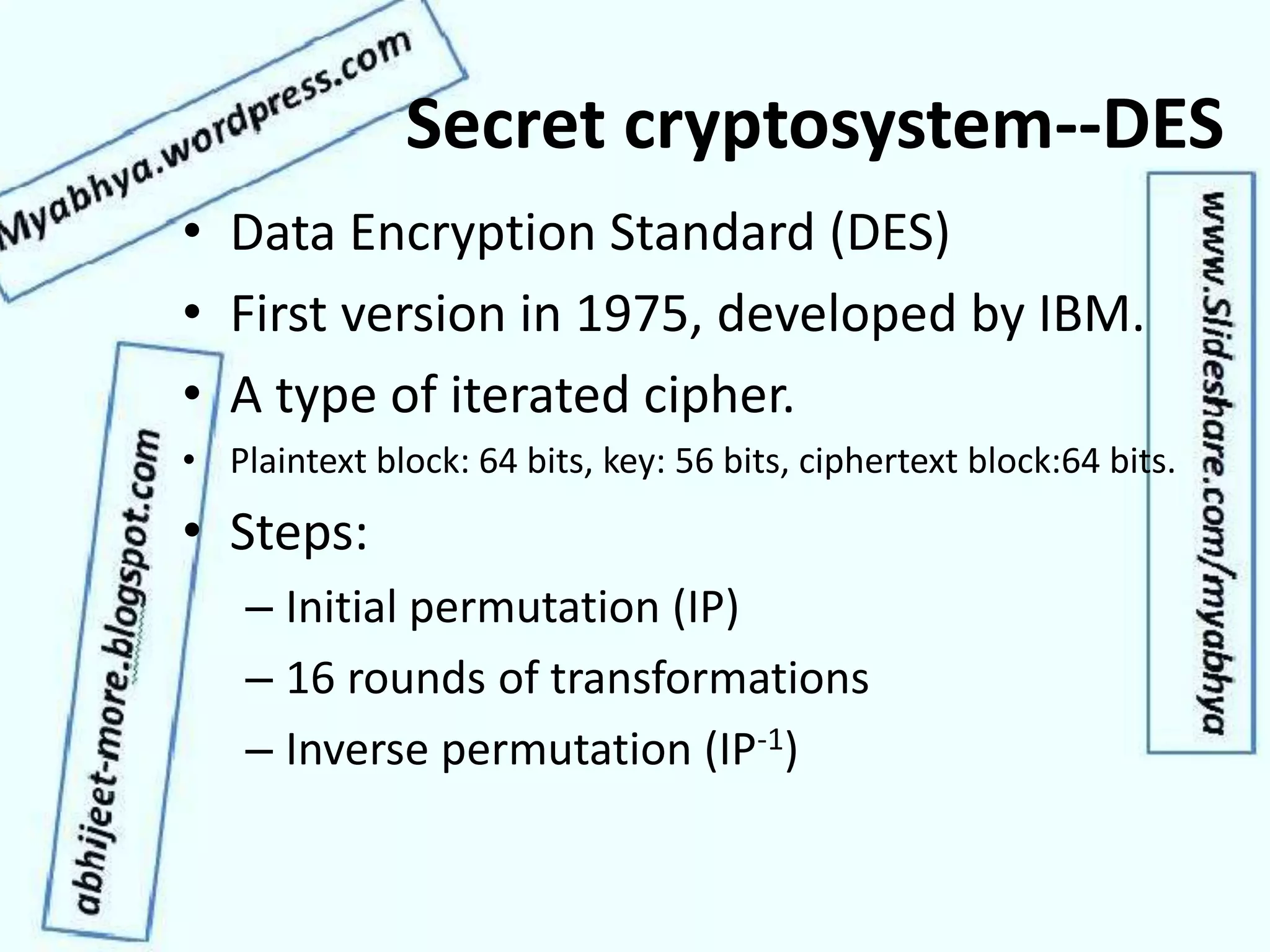
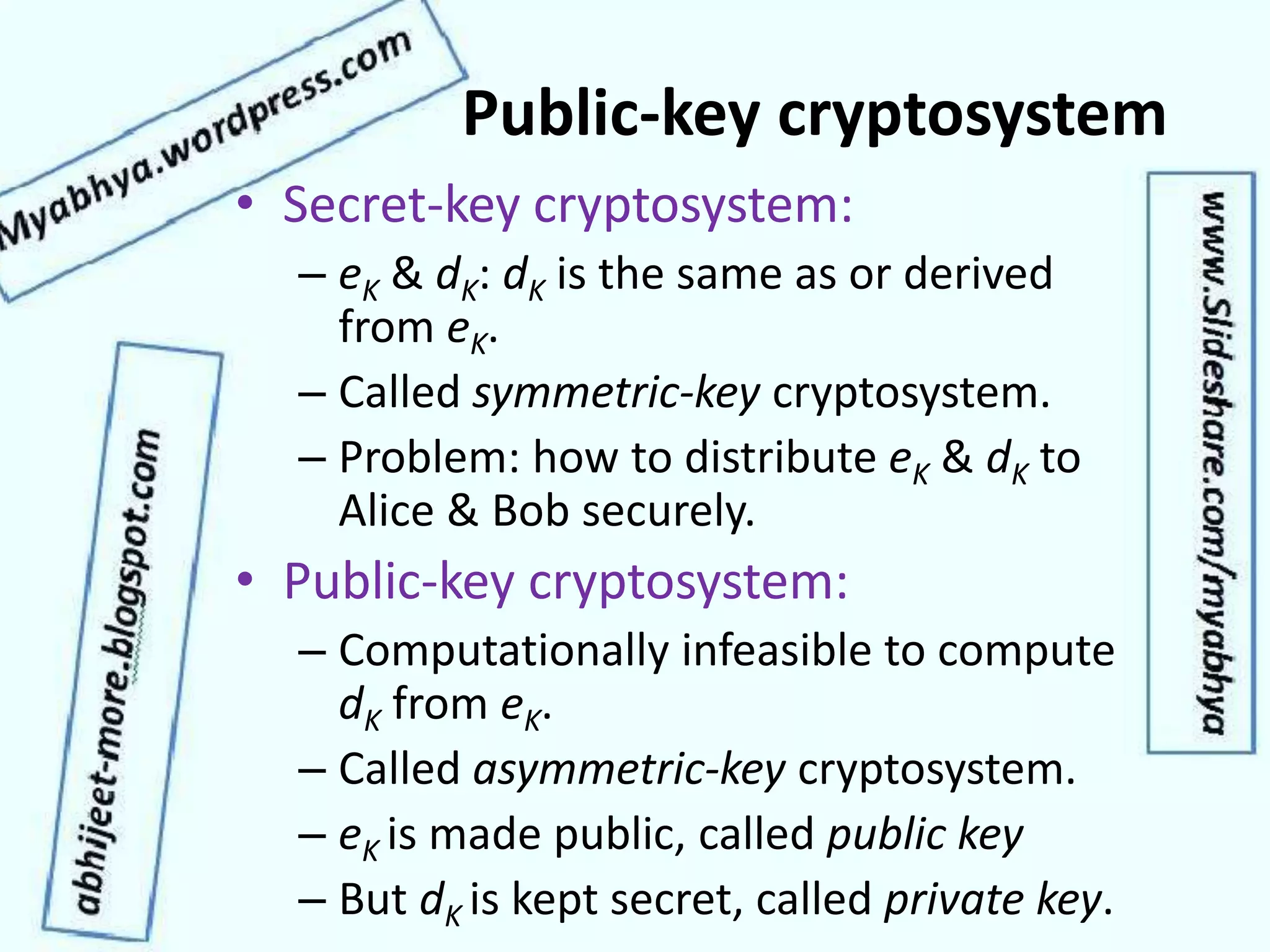
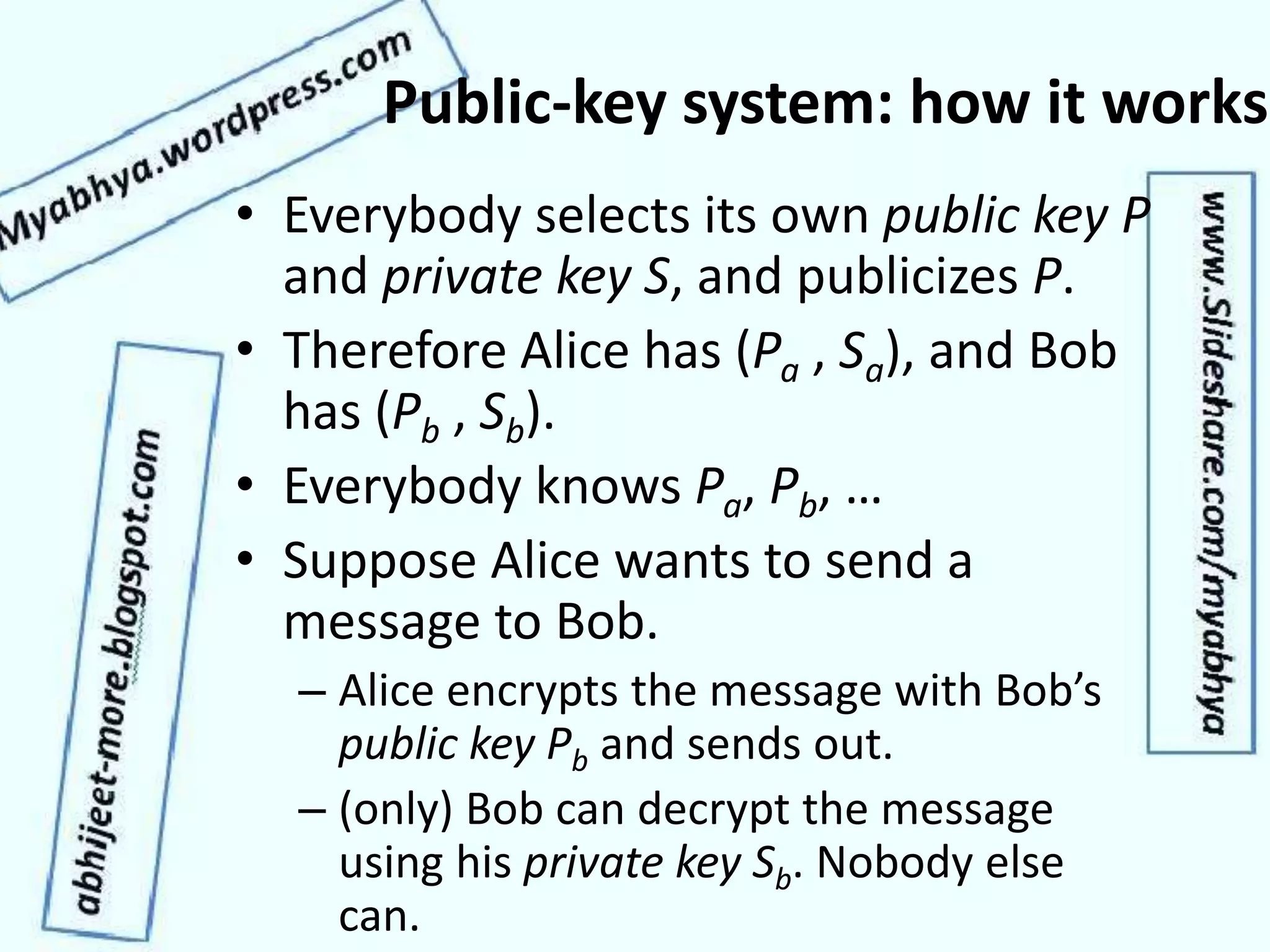
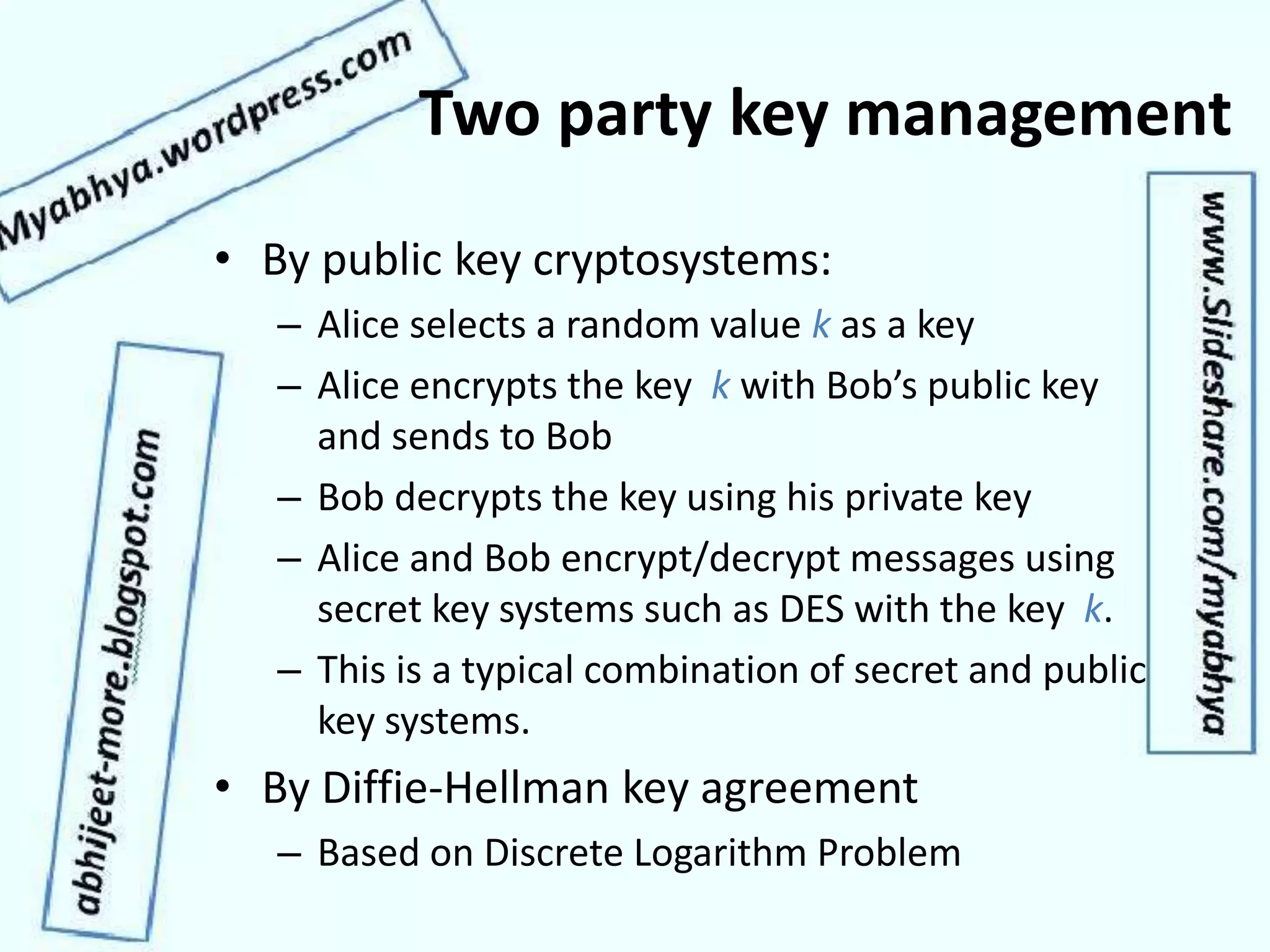
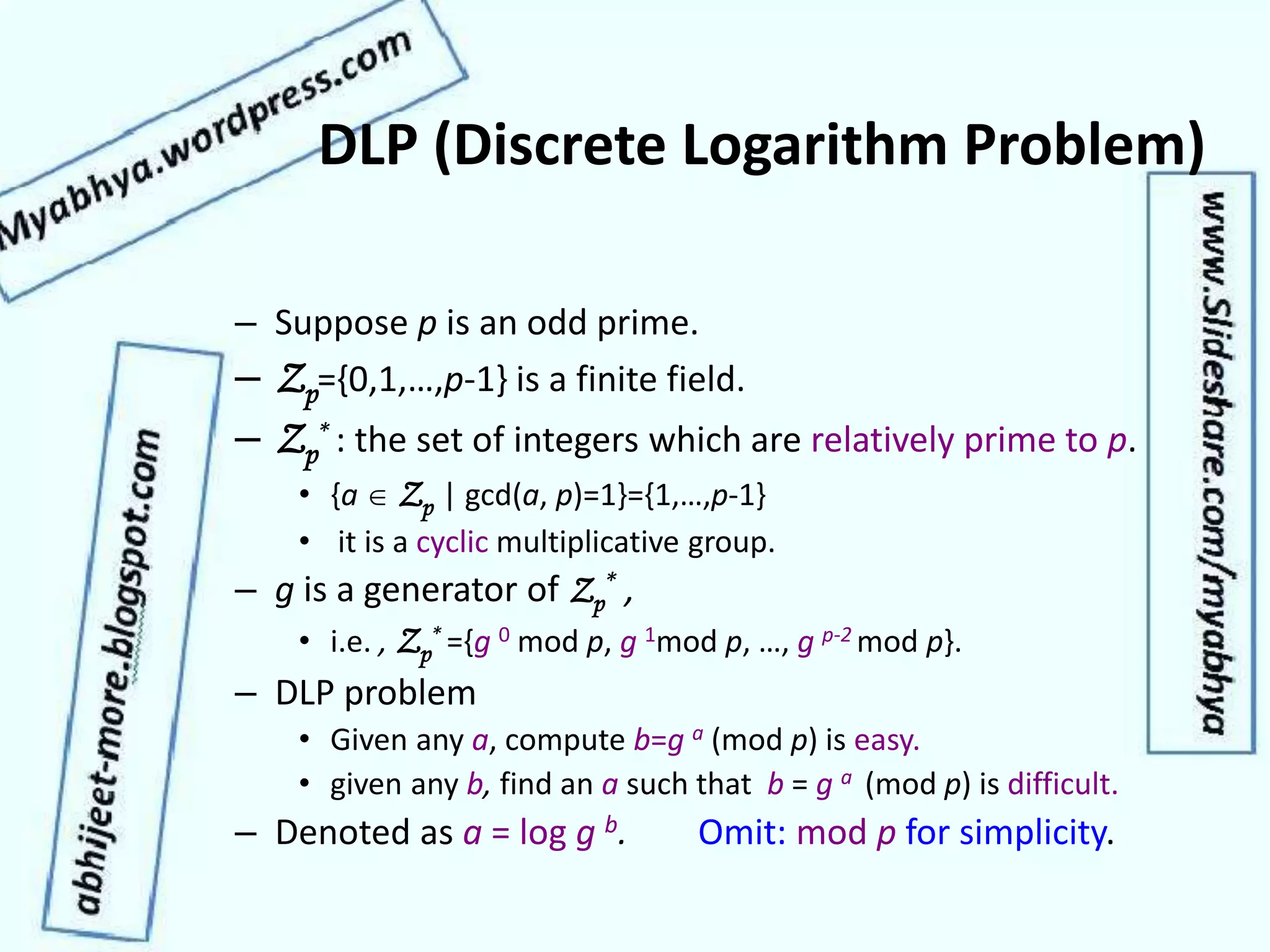
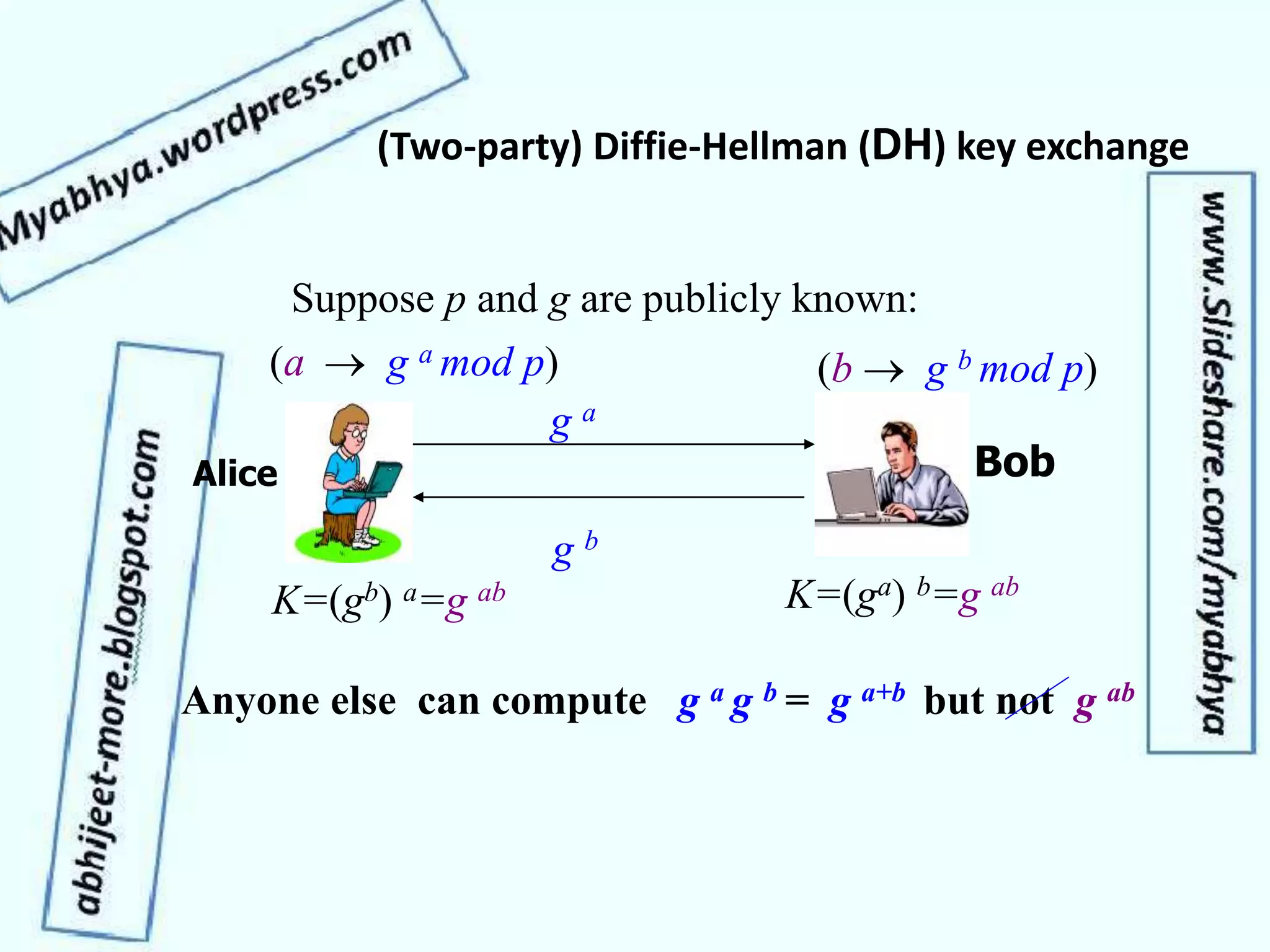
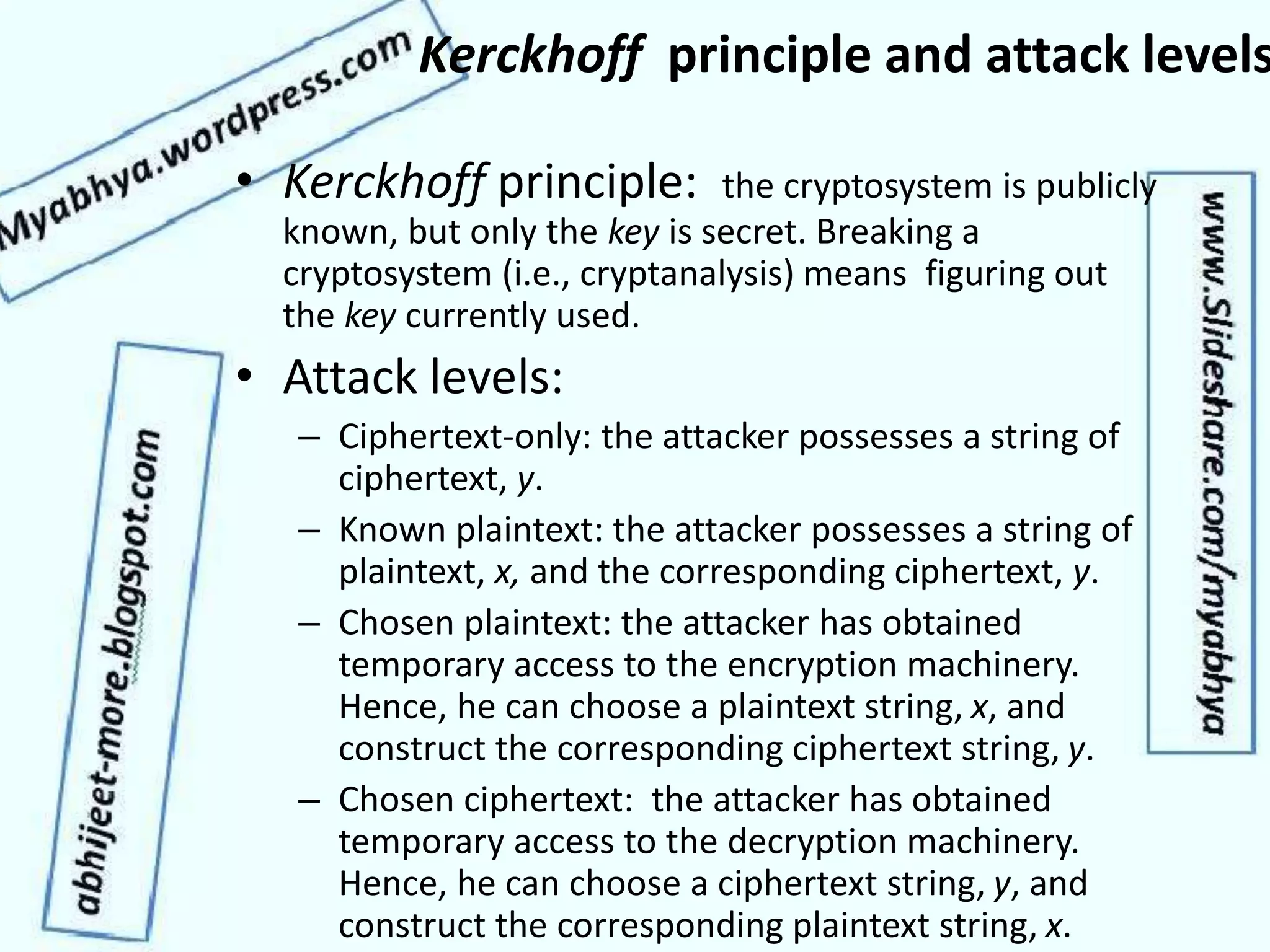
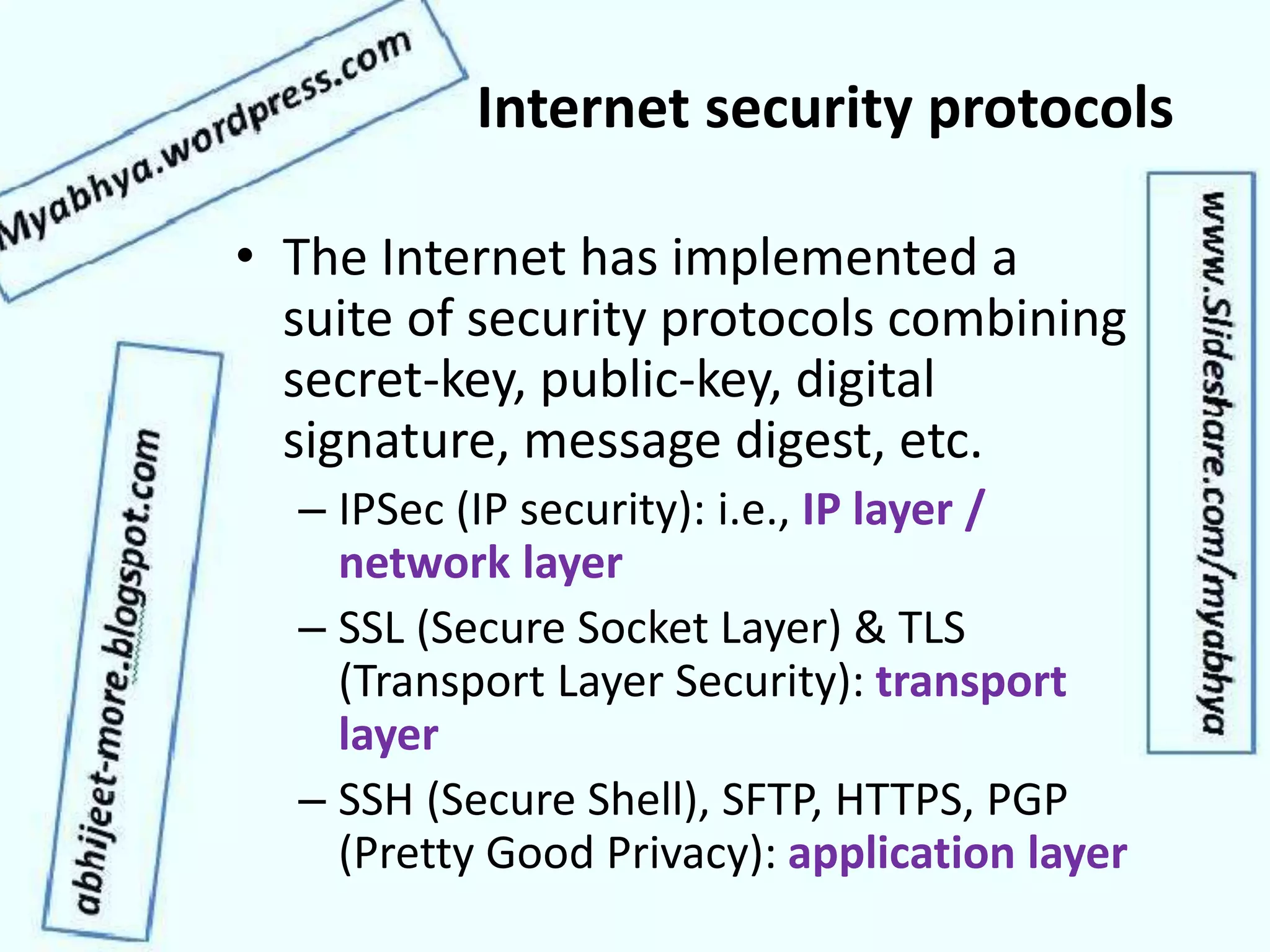
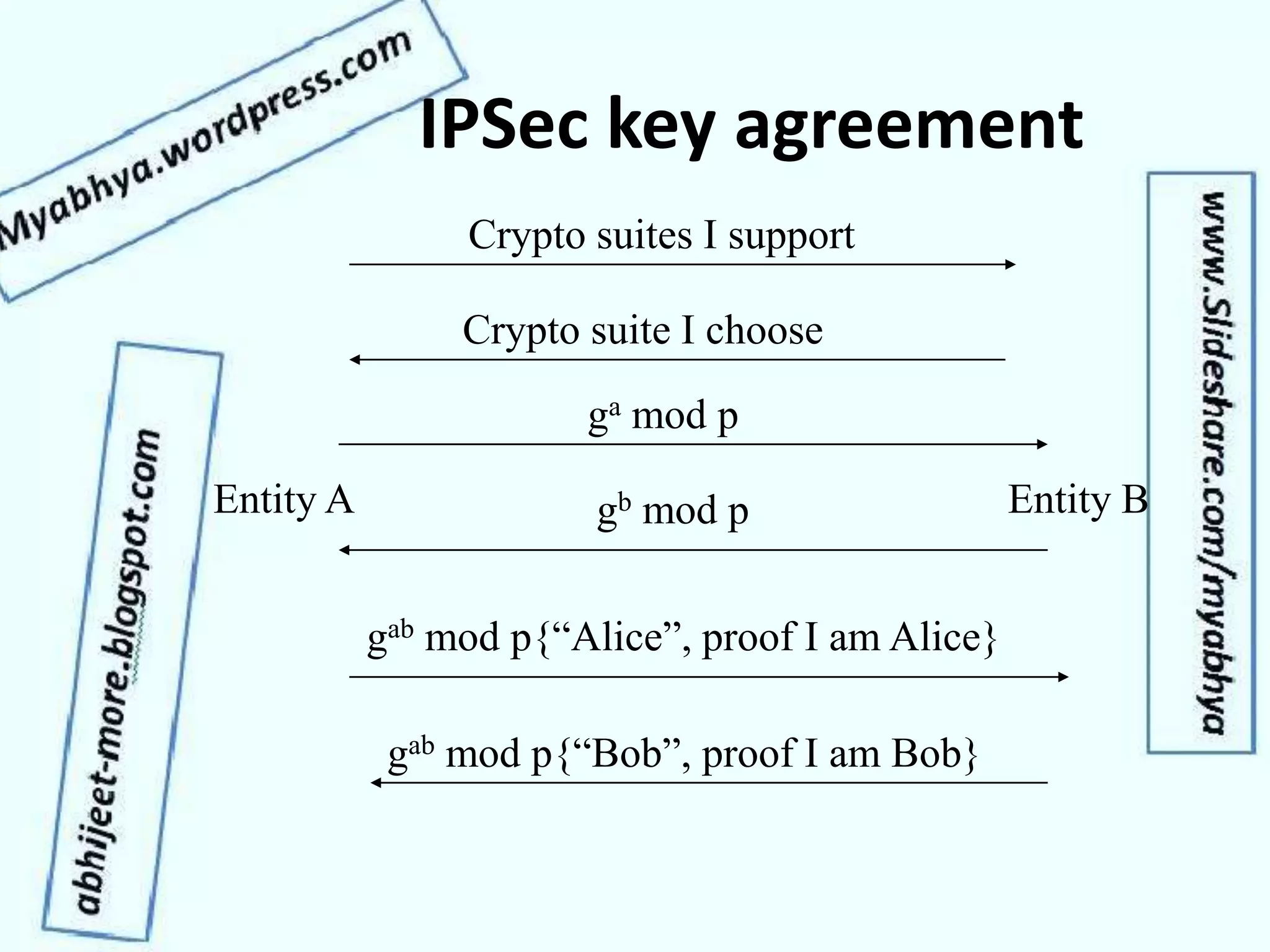
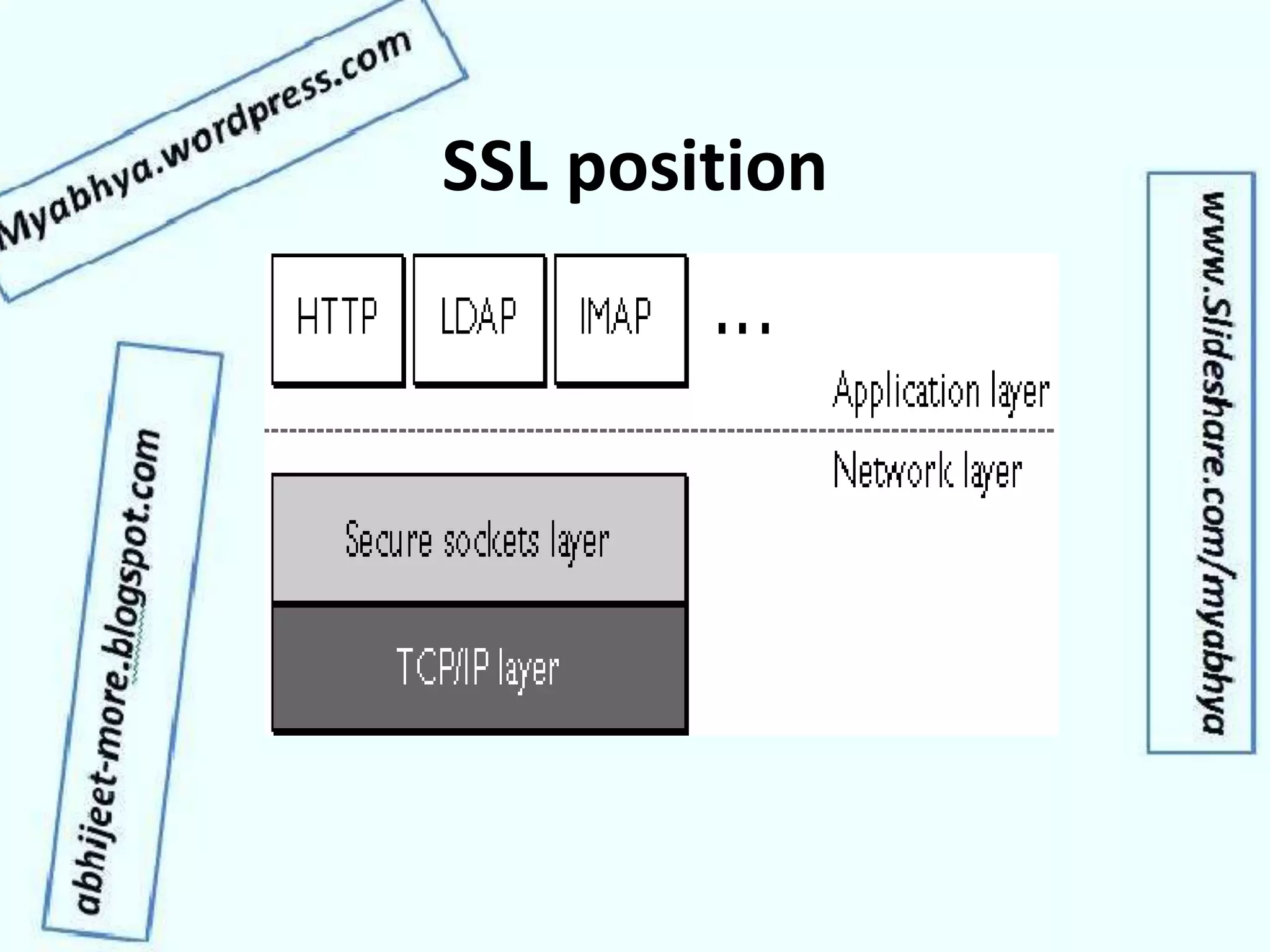
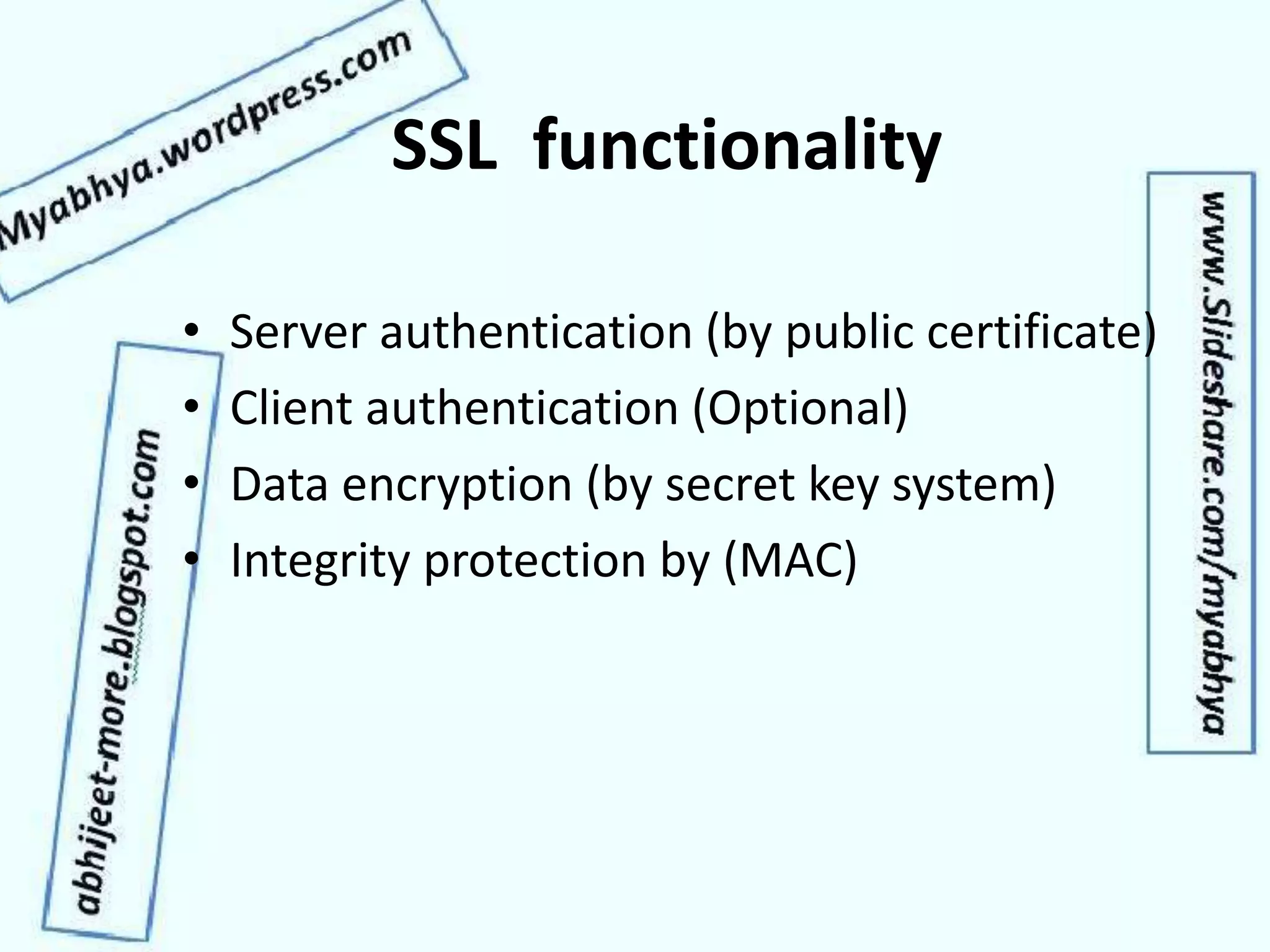
This document discusses network security and cryptography. It covers topics such as security requirements including confidentiality, integrity, authentication, and non-repudiation. It also discusses approaches to implementing these security requirements including encryption for confidentiality and digital signatures for authentication and non-repudiation. Additionally, it covers network threats and attacks, classifications of cryptosystems including classical and modern cryptosystems, key management, public key cryptography, and internet security protocols like IPSec and SSL/TLS.