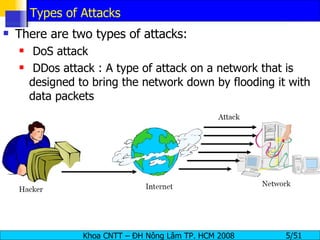
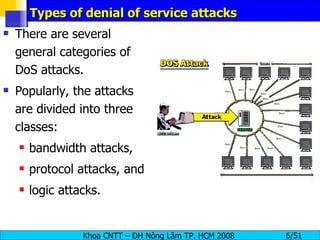
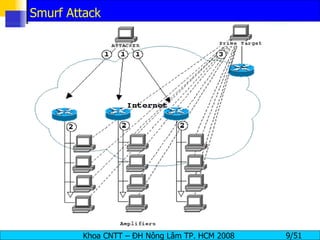
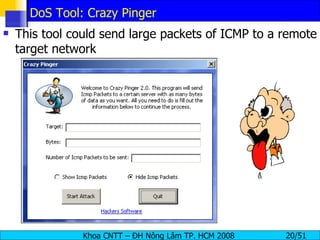
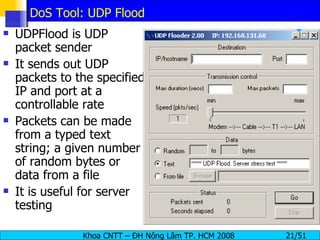
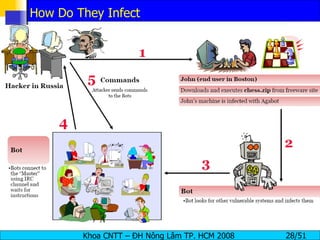
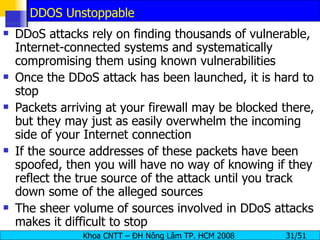
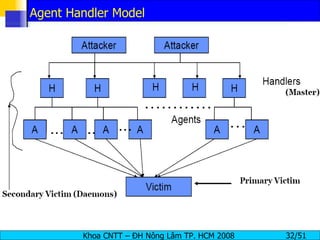
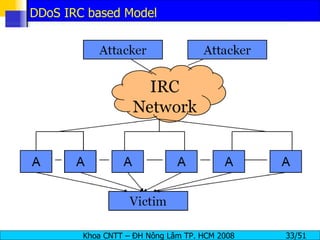
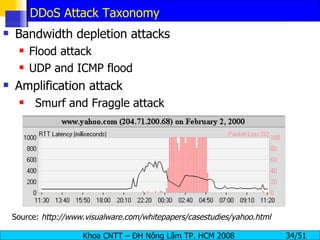
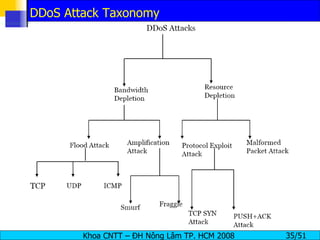
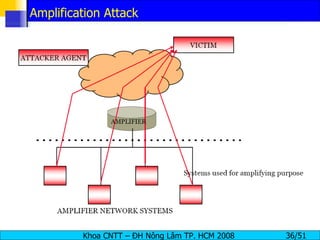
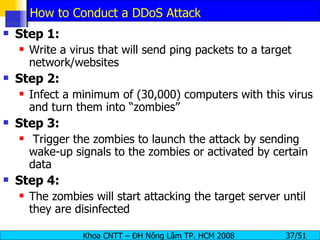
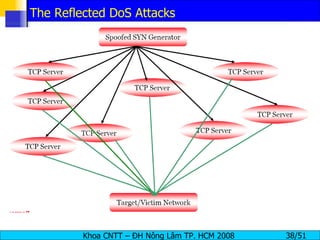
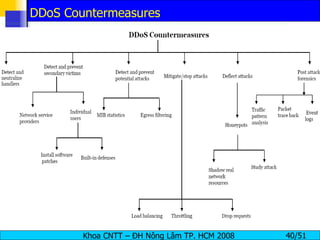
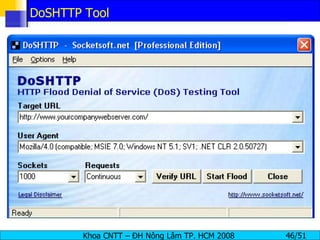
The document discusses denial of service (DoS) and distributed denial of service (DDoS) attacks. It defines DoS and DDoS attacks, describes different types of DoS attacks like SYN flooding and Smurf attacks. It also explains how botnets and tools are used to launch DDoS attacks, and discusses some common DDoS countermeasures like detection, mitigation and traceback.