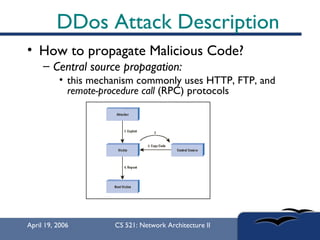
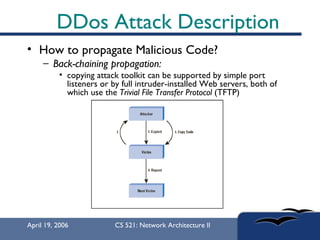
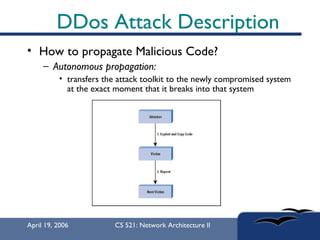
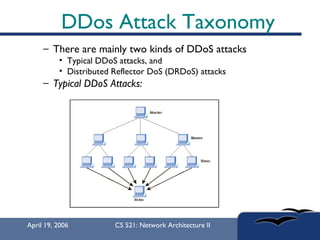
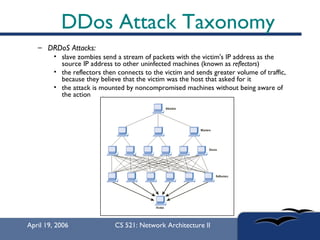
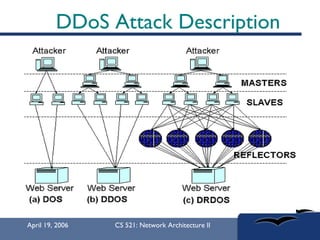
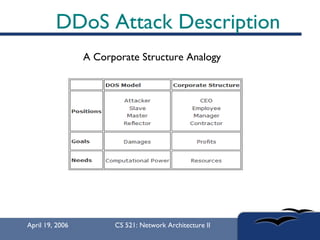
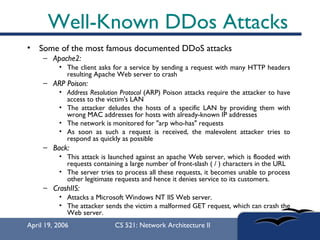
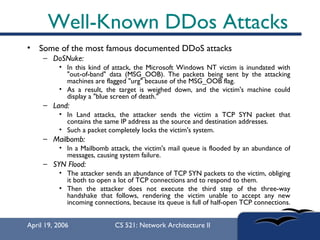
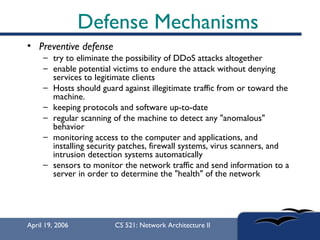
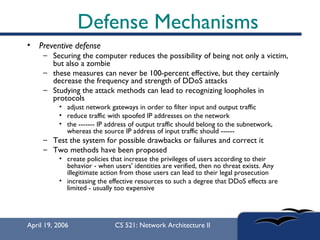
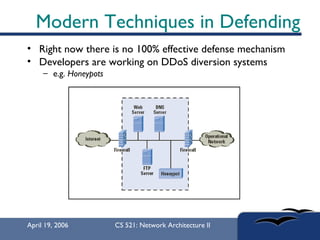
The document provides an in-depth overview of Distributed Denial of Service (DDoS) attacks, explaining their definition, methods of execution, types, and famous examples. It outlines attack mechanisms such as target resource exhaustion and exploitation of network vulnerabilities, along with defense strategies including preventive and reactive measures. The document concludes by emphasizing the ongoing challenge of defending against DDoS attacks and the need for cooperation between legitimate users and security developers.