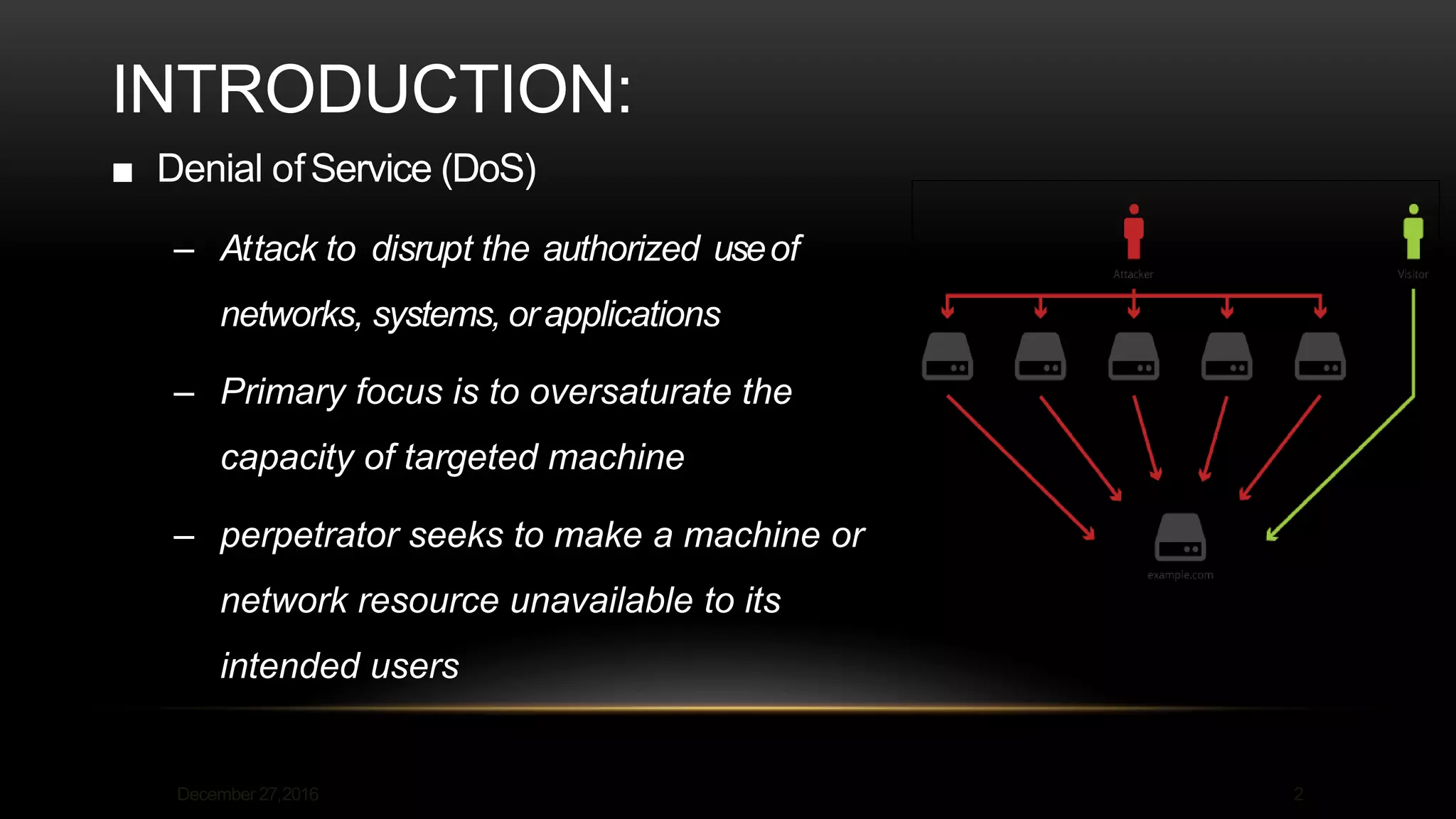
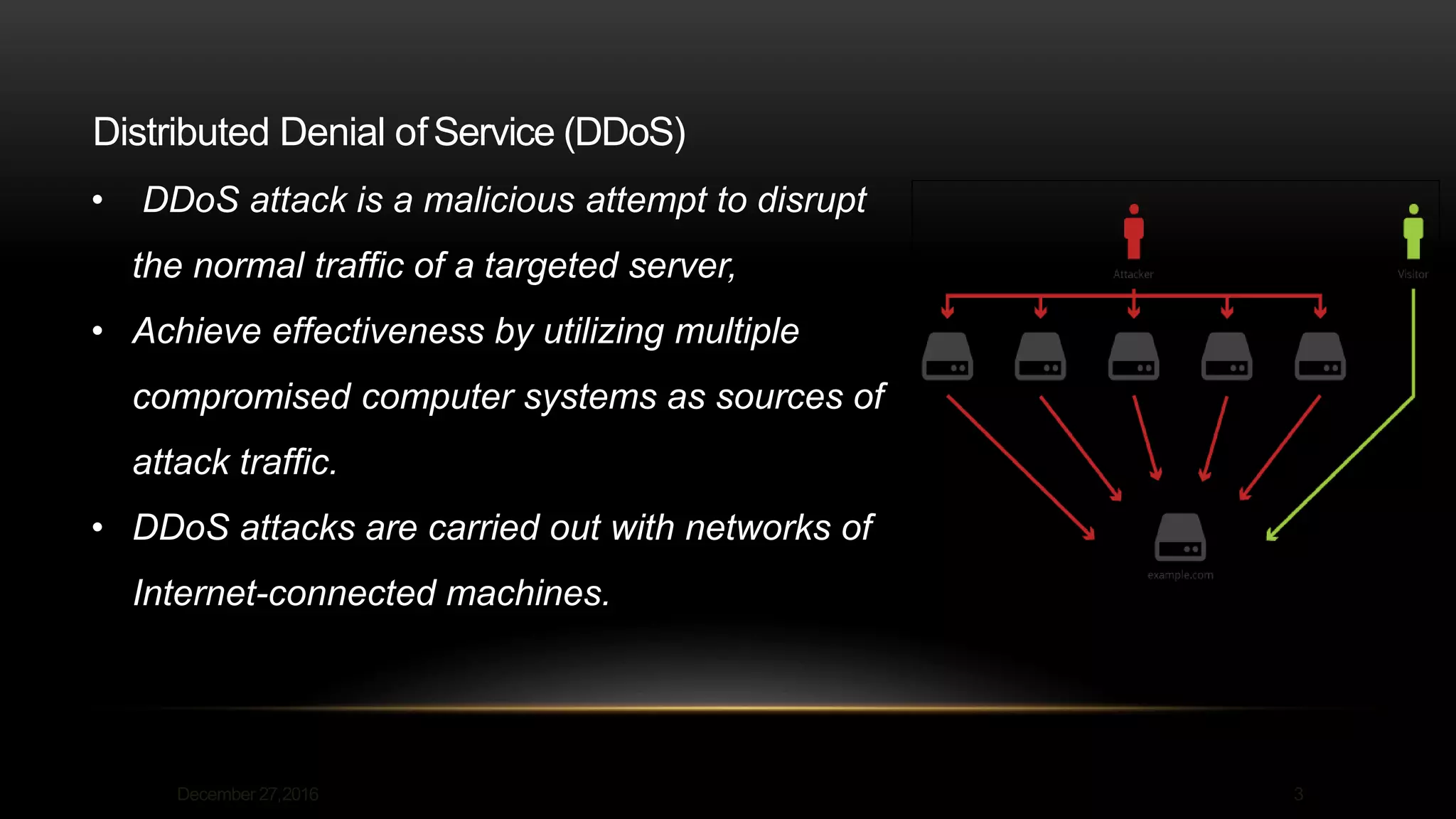
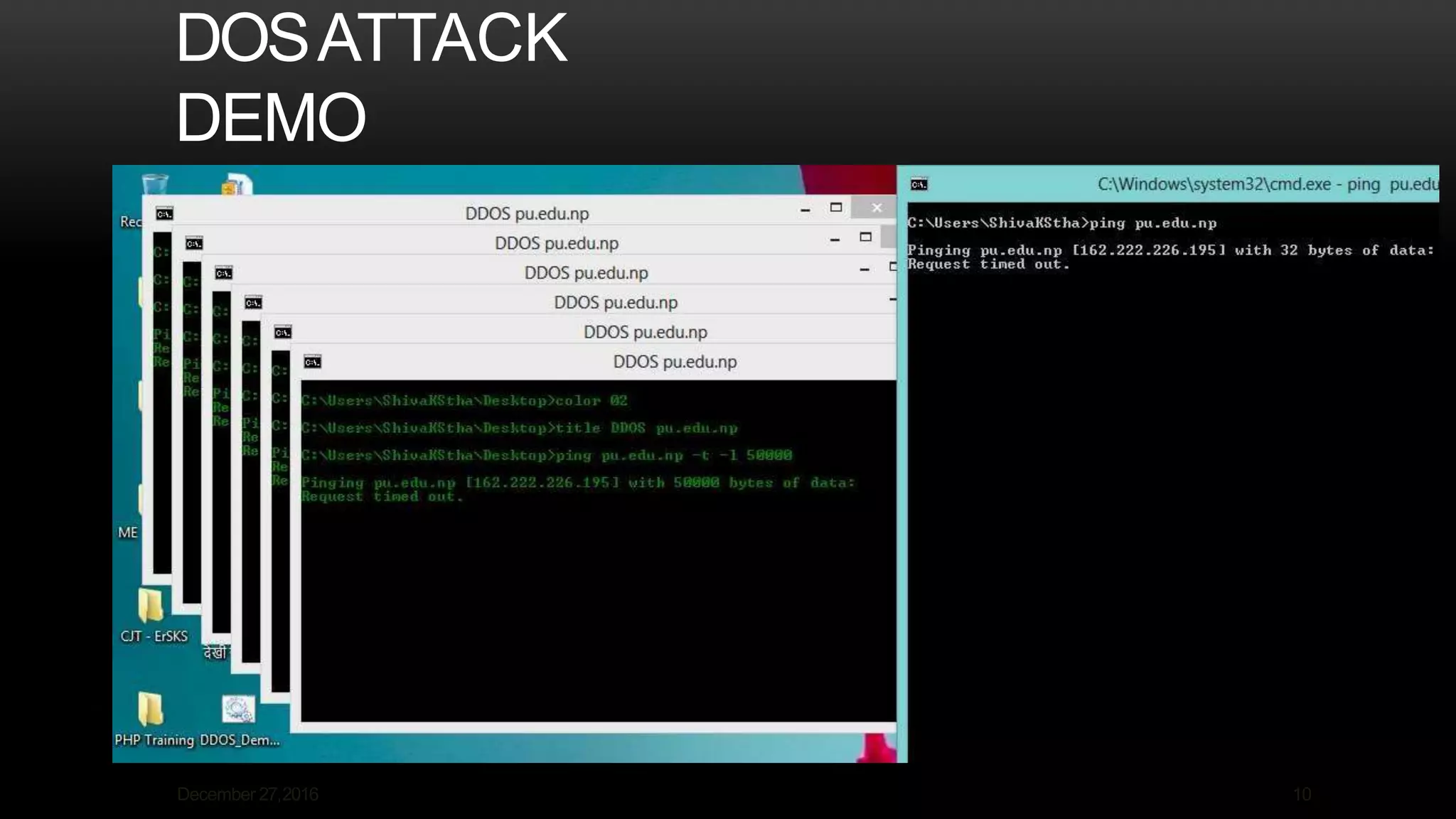
This document discusses denial of service (DoS) and distributed denial of service (DDoS) attacks. It defines DoS as an attack that seeks to oversaturate a targeted machine's capacity to disrupt authorized use, while a DDoS uses multiple compromised systems to flood the target. The document describes how DDoS attacks work by flooding the victim from many sources, making it hard to block. It lists common DoS attacks like buffer overflow and ICMP floods, and DDoS attack types like traffic floods and application attacks. The document also covers typical attacker motivations and recommendations to prevent attacks like buying more bandwidth and building redundancy.