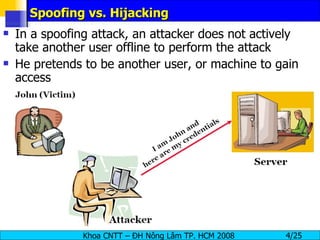
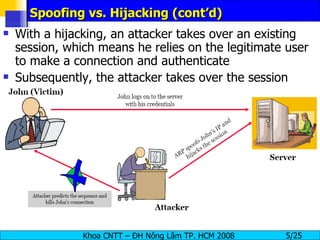
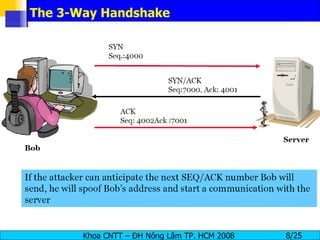
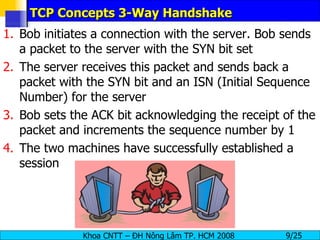
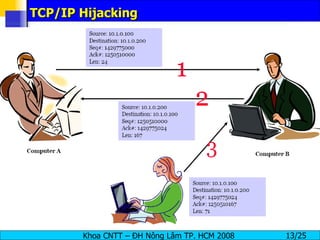
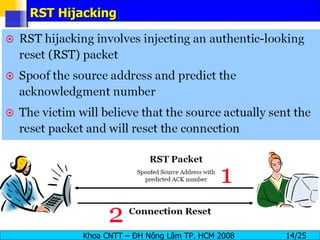
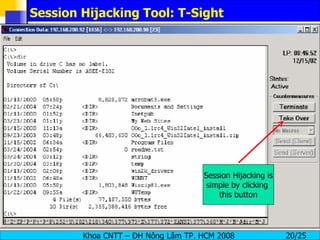
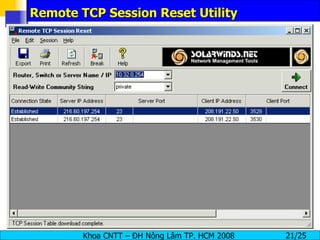
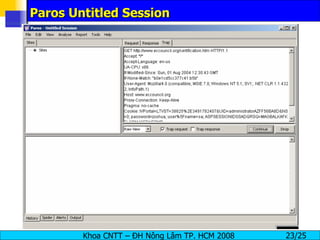
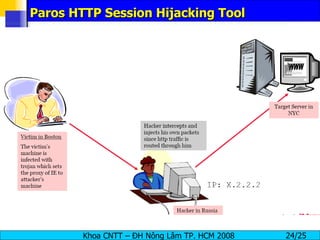
Session hijacking involves an attacker taking over an existing TCP connection between two machines by predicting sequence numbers and spoofing IP addresses. The document discusses the difference between spoofing and hijacking, the steps an attacker takes to hijack a session including predicting sequence numbers and killing the original connection, types of session hijacking techniques, and tools that can be used for session hijacking like Juggernaut, Hunt, IP Watcher, and T-Sight. It also provides countermeasures like using encryption, secure protocols, limiting connections, and educating employees.