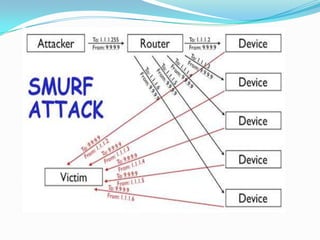
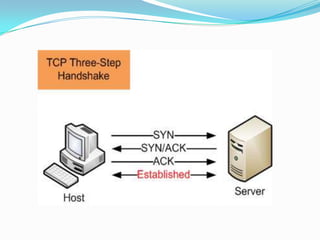
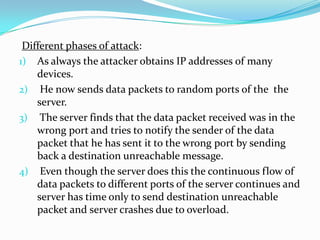
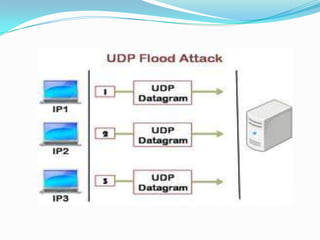
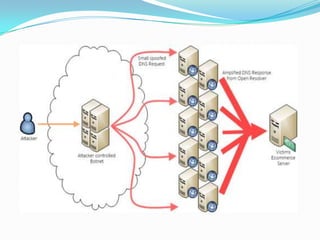
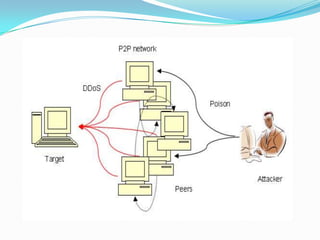
DDoS attacks target companies and institutions that provide online services. They work by overloading servers with traffic from multiple compromised systems known as "bots" or "zombies". Common DDoS attack types include SMURF, TCP SYN/ACK, UDP flood, DNS amplification, and attacks using peer-to-peer networks. Defenses include configuring routers and firewalls to filter unauthorized traffic, limiting response messages, and tracking malicious activity on peer-to-peer networks. As attack methods evolve, continued development of detection and mitigation techniques is needed.