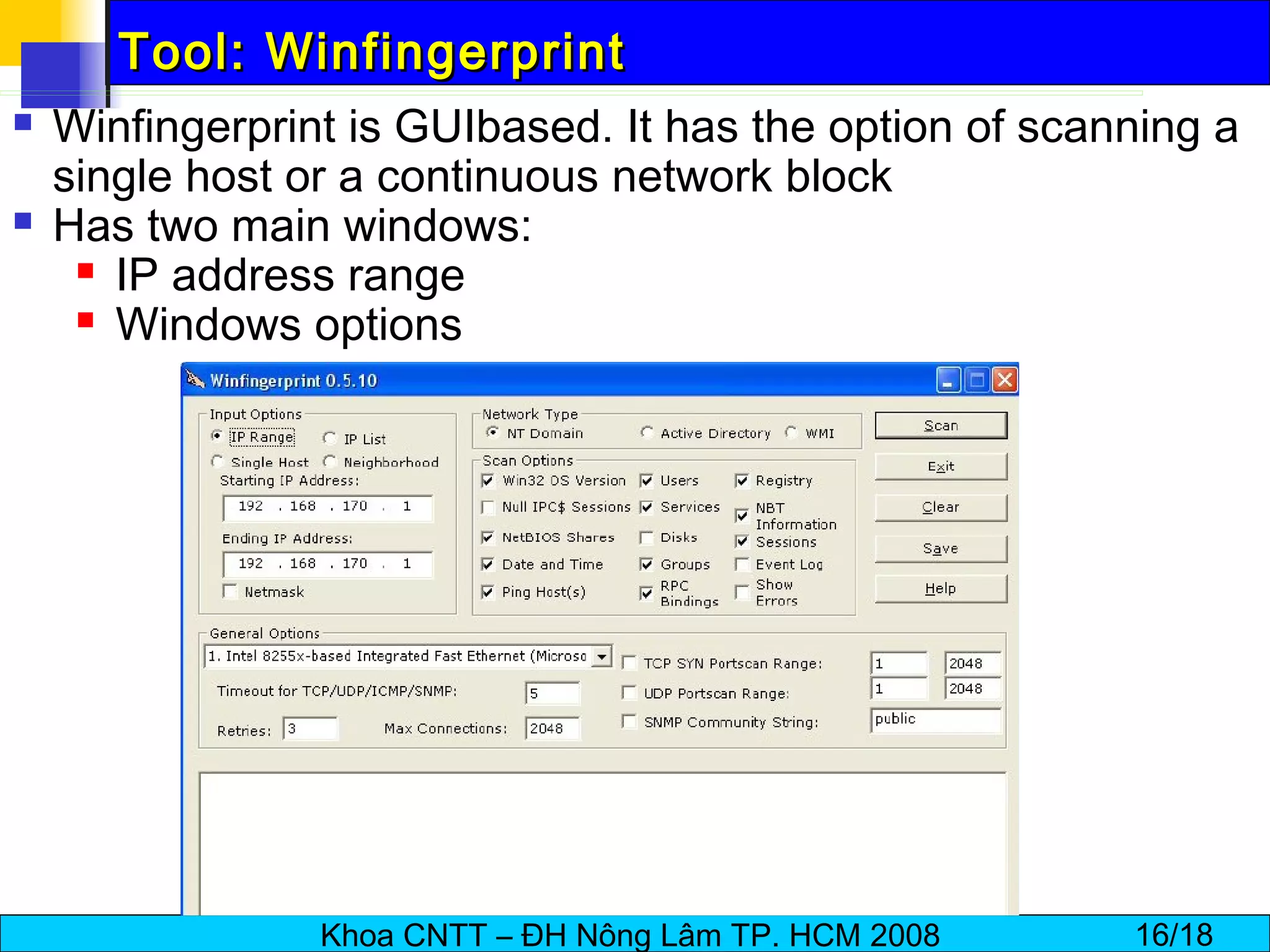
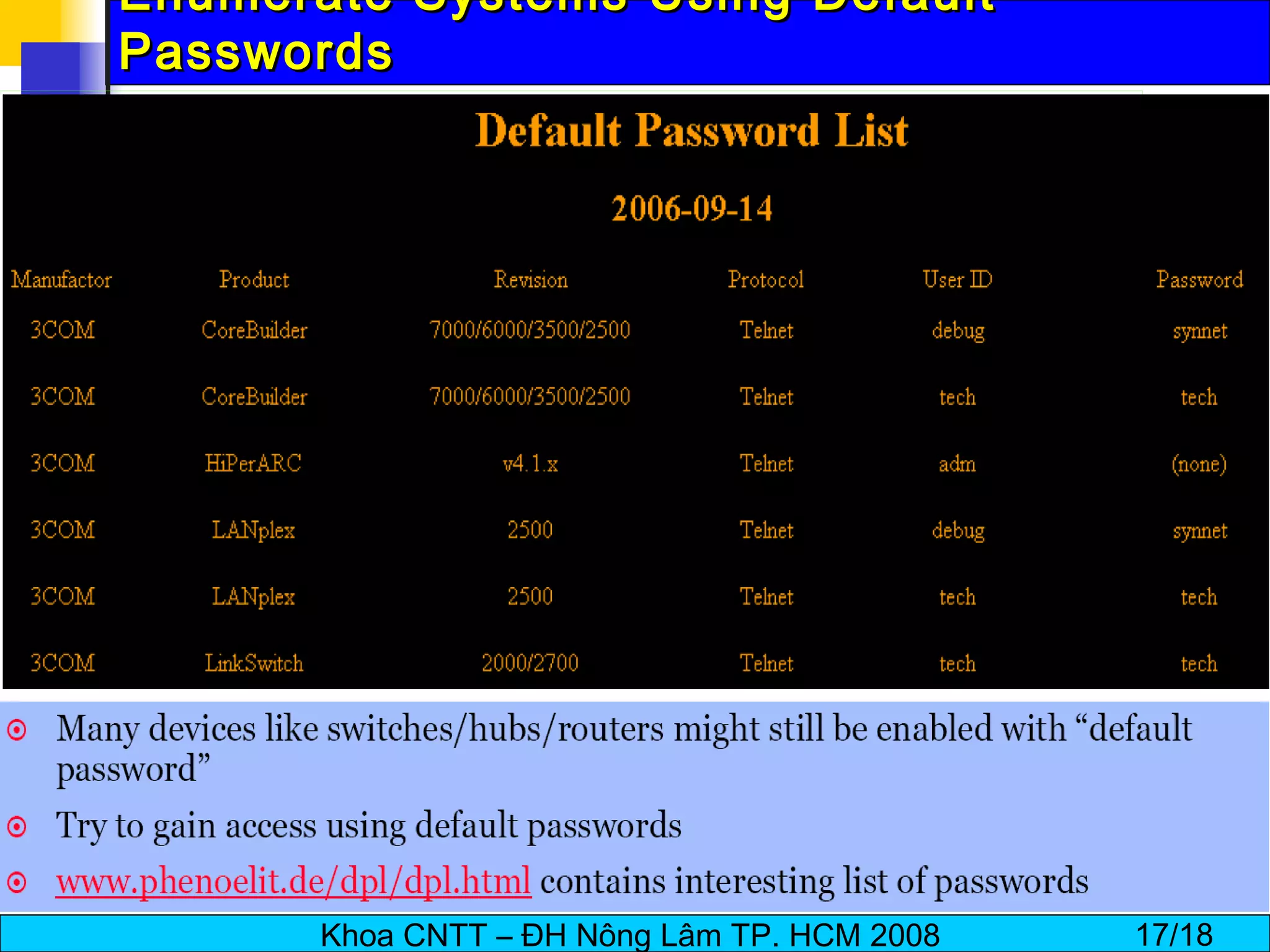
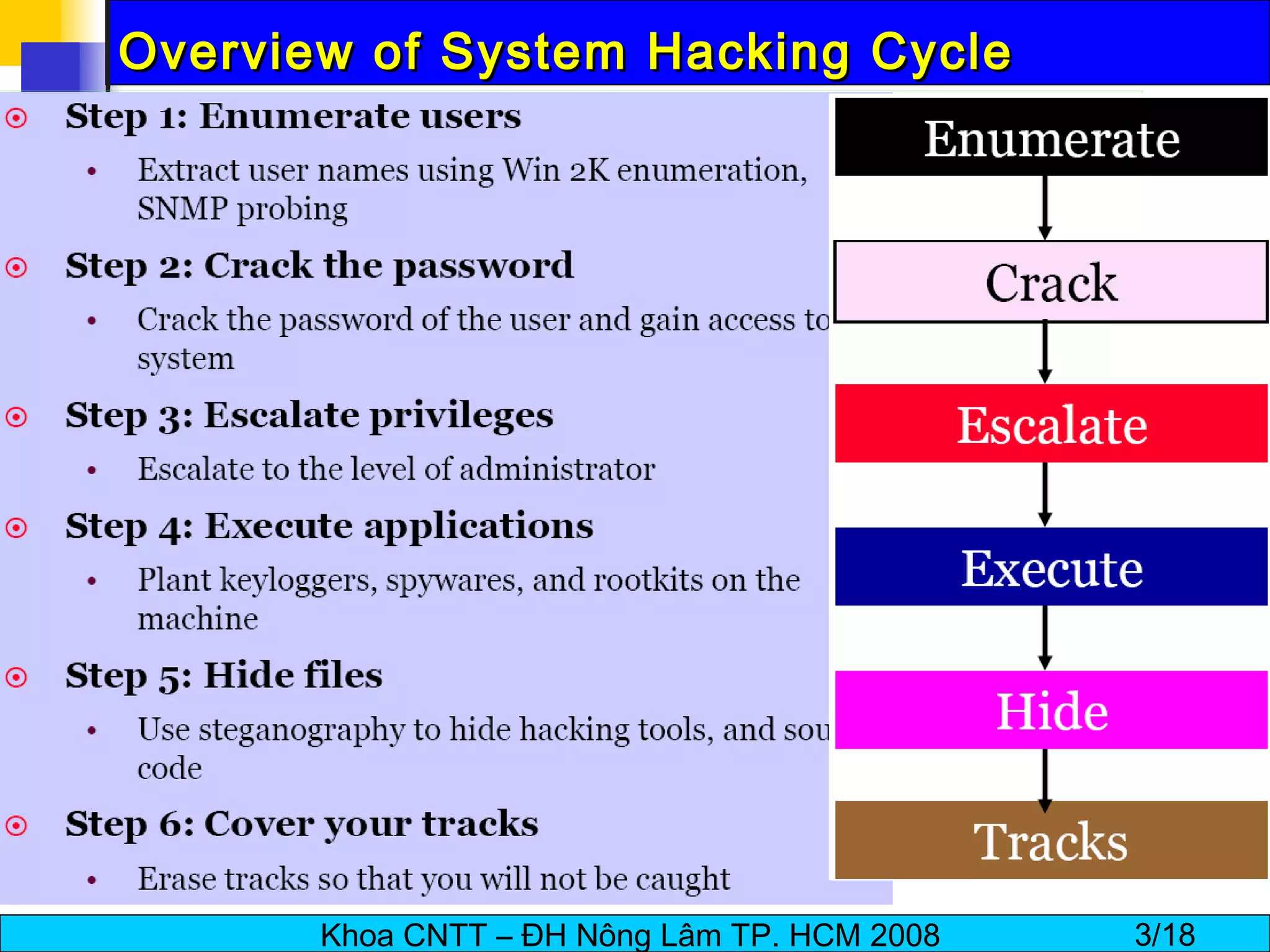
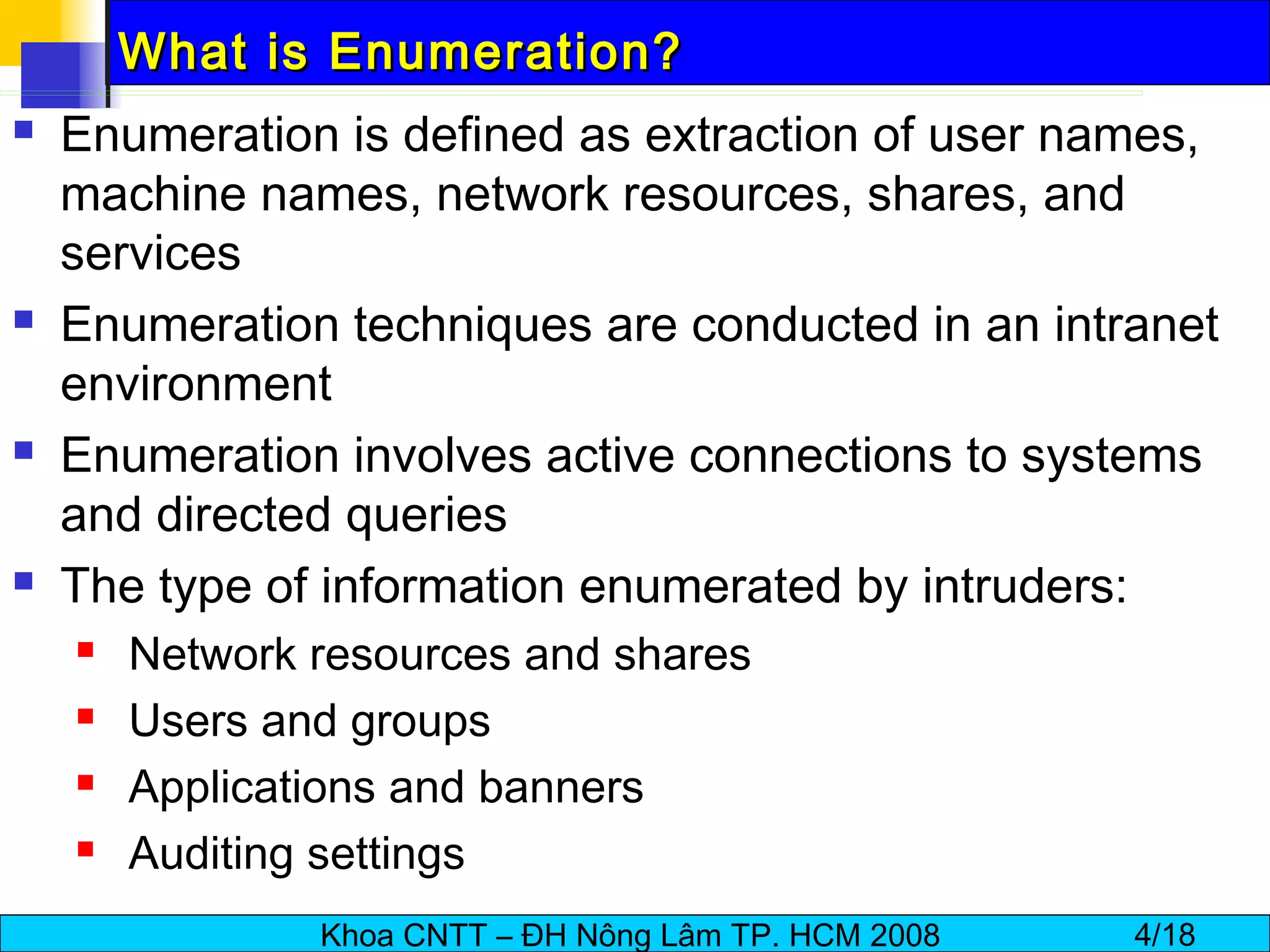
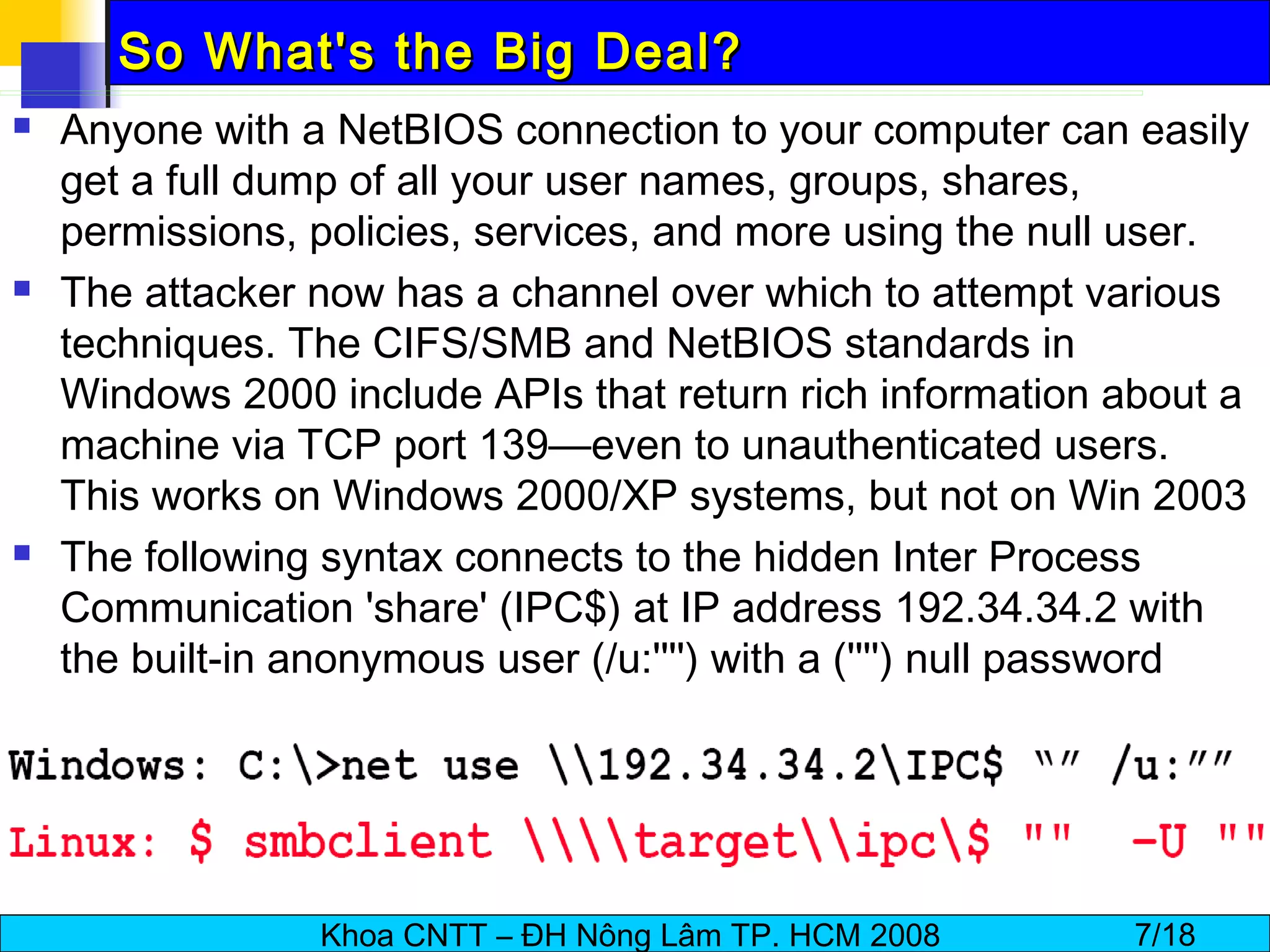
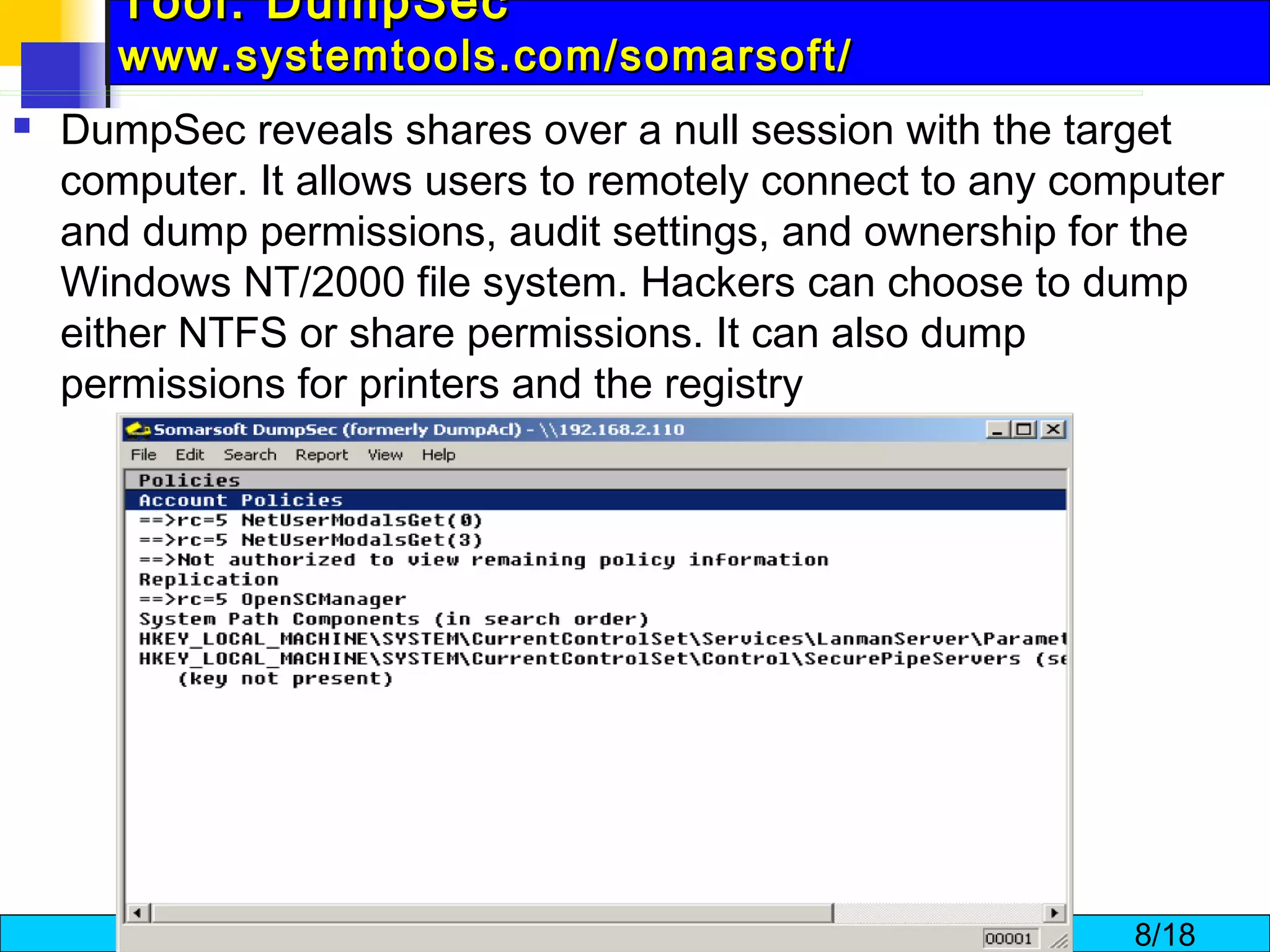
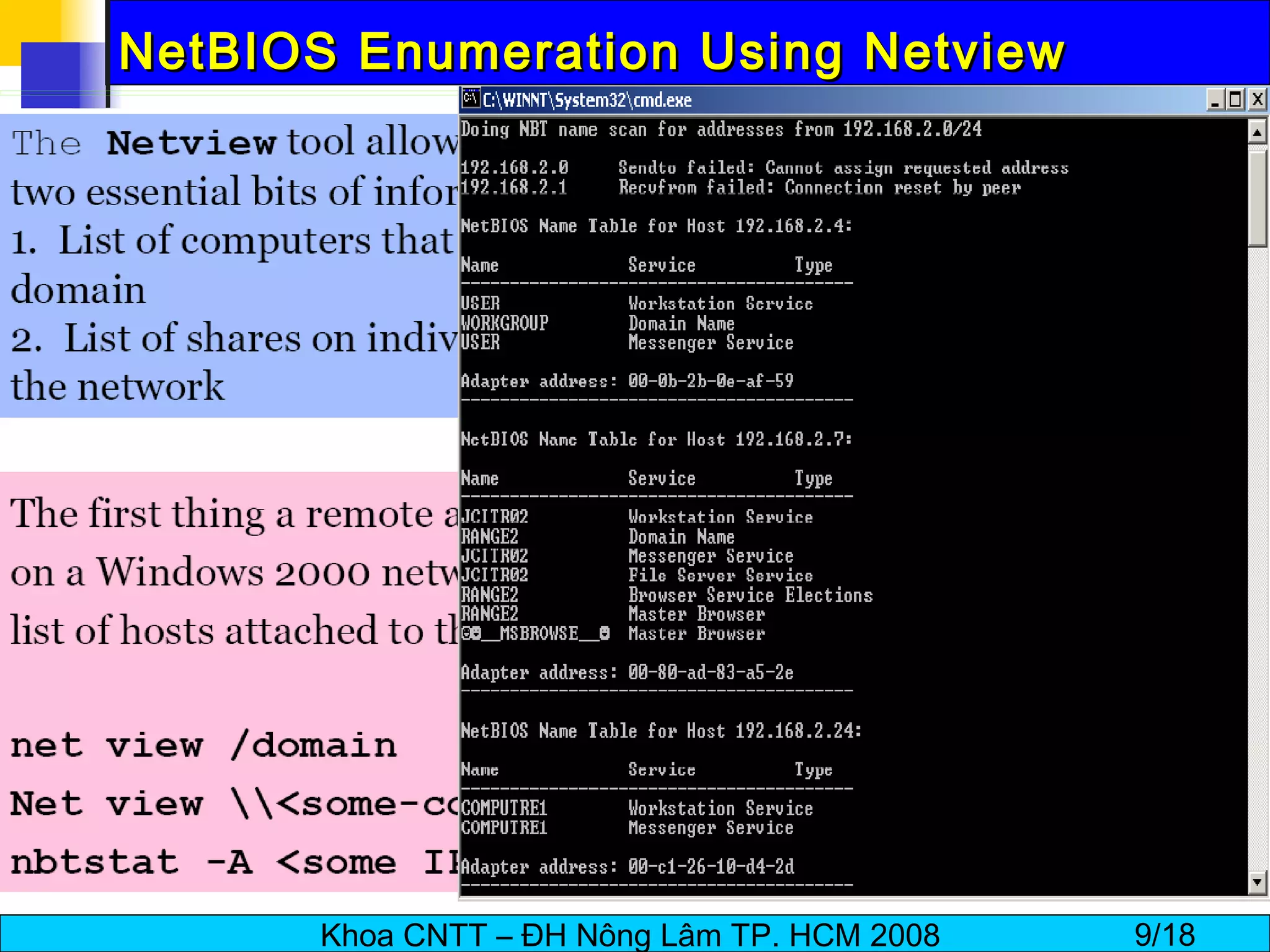
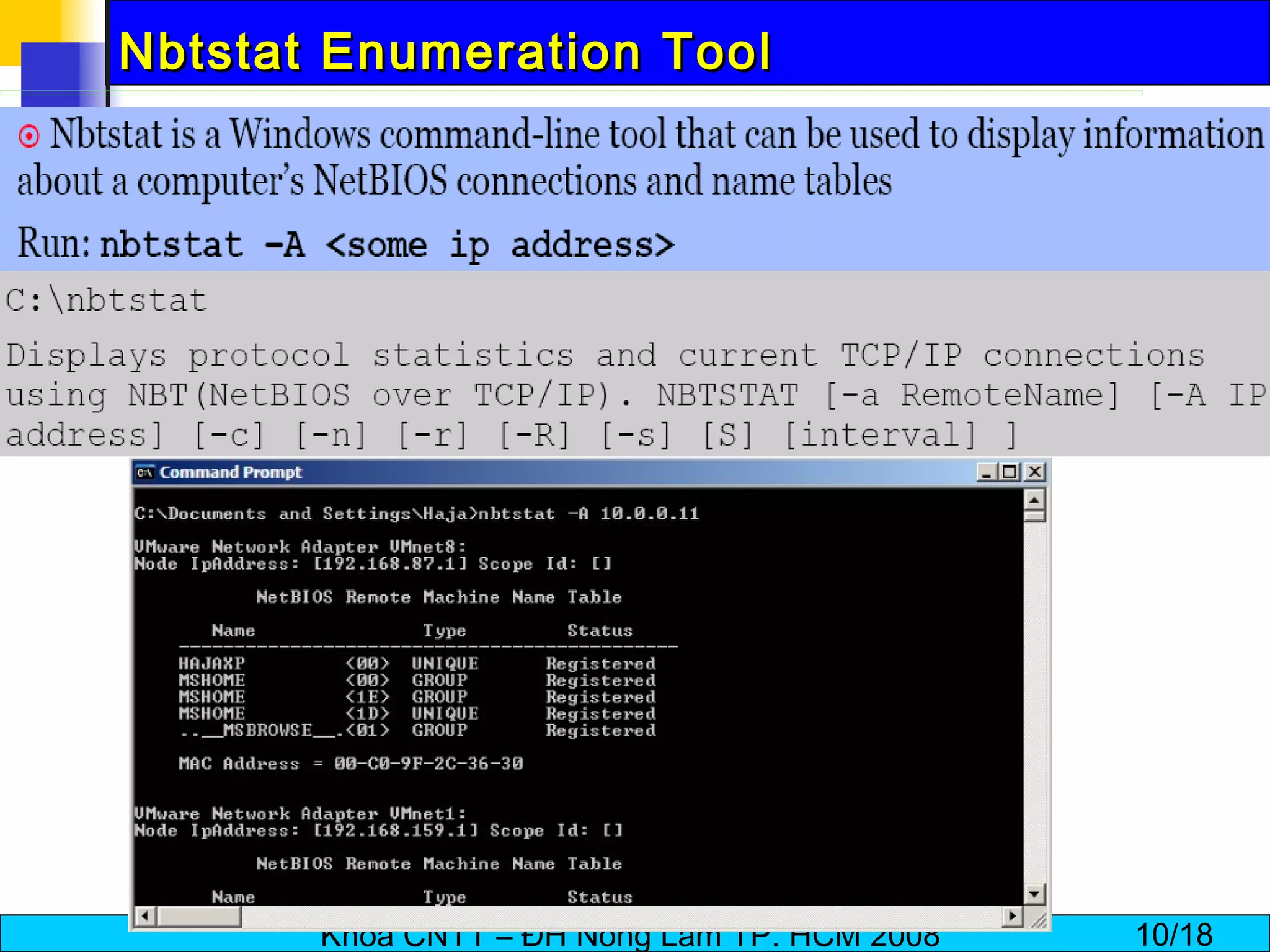
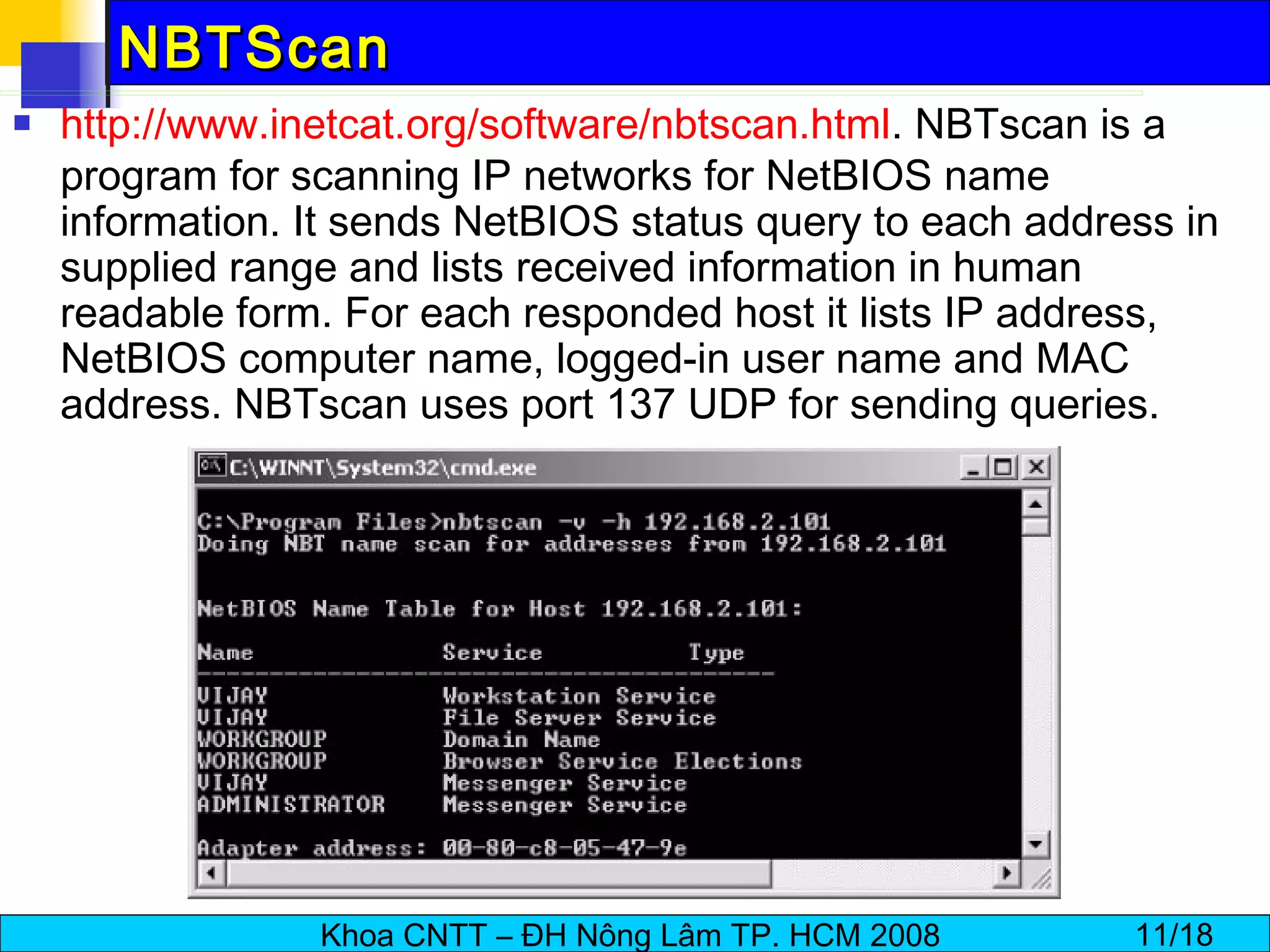
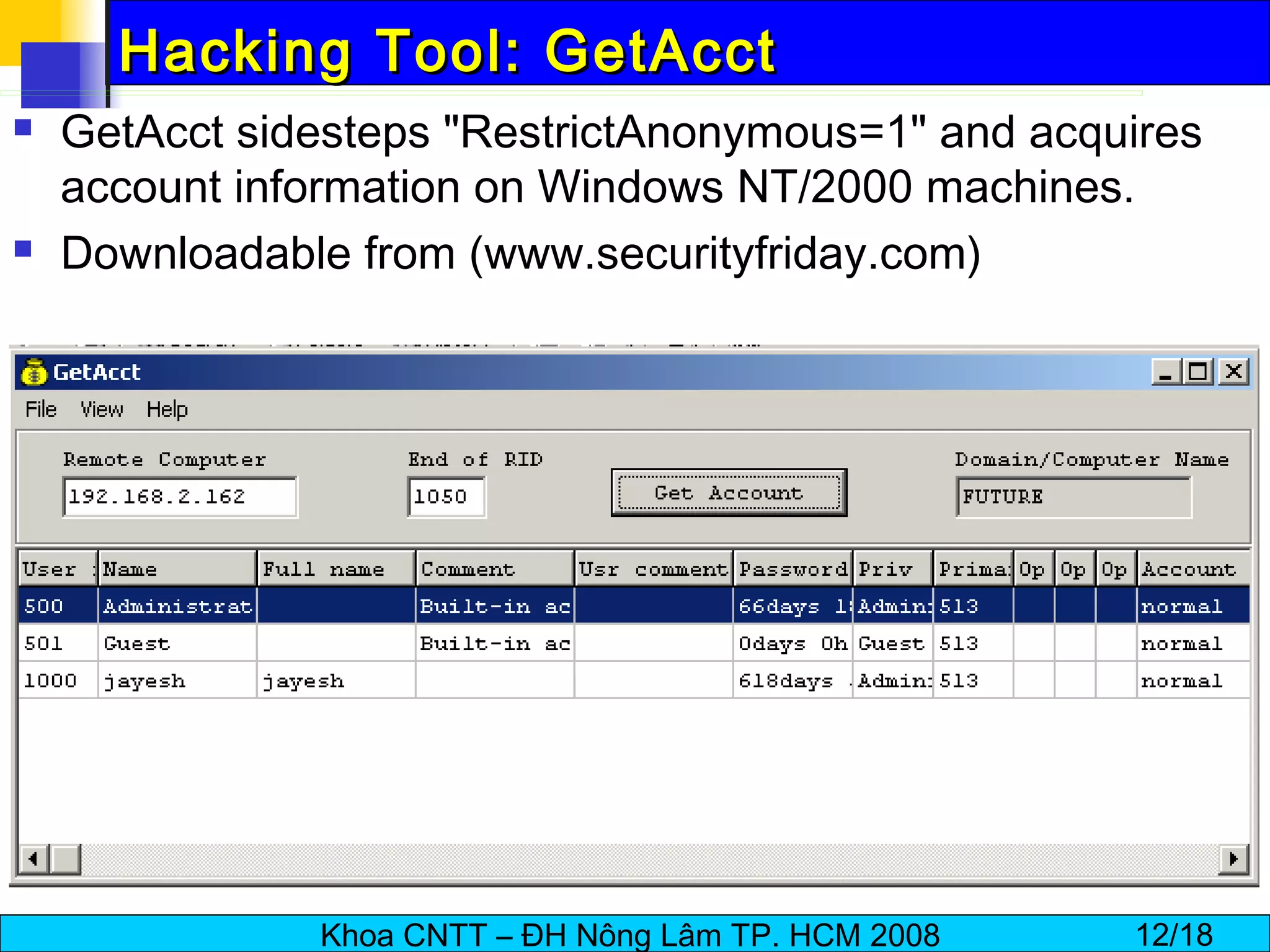
The document discusses techniques for enumerating information from systems during the hacking process. It describes establishing null sessions to extract user names, shares, and other details without authentication. Tools like DumpSec, Netview, Nbtstat, GetAcct, and PS Tools are also covered as ways to enumerate users, groups, shares, permissions, and more from Windows and UNIX systems. The document also provides countermeasures like restricting null sessions and the anonymous user to protect against enumeration attacks.
![UNIX Enumeration Commands used to enumerate Unix network resources are as follows: showmount: – Finds the shared directories on the machine – [root $] showmount –e 19x.16x. xxx.xx Finger: – Enumerates the user and host – Enables you to view the user’s home directory, login time, idle times, office location, and the last time they both received or read mail – [root$] finger –1 @target.hackme.com rpcinfo: – Helps to enumerate Remote Procedure Call protocol – RPC protocol allows applications to talk to one another over the network – [root] rpcinfo –p 19x.16x.xxx.xx](https://image.slidesharecdn.com/module4-enumeration-091013103501-phpapp01/75/Module-4-Enumeration-15-2048.jpg)