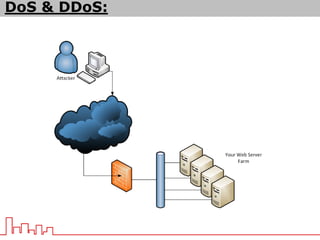
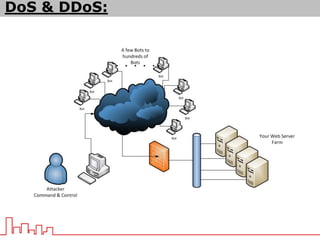
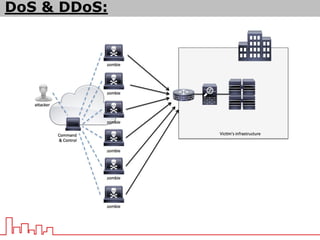
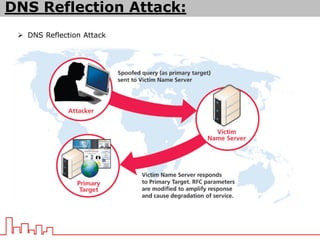
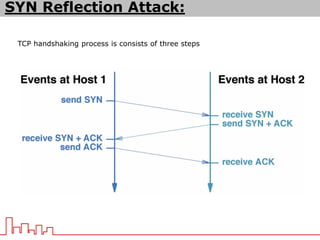
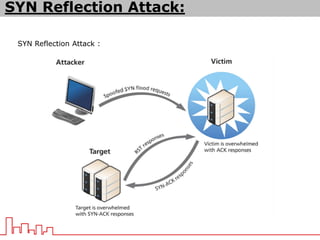
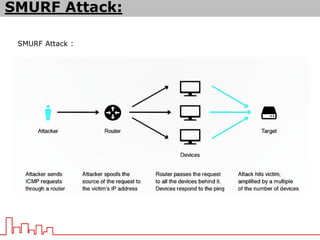
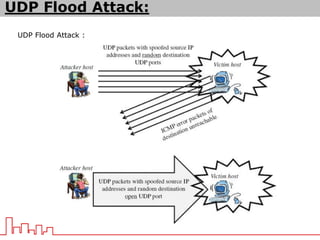
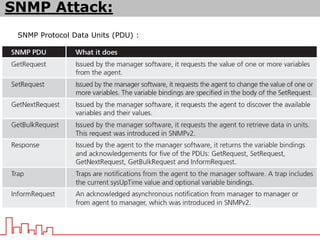
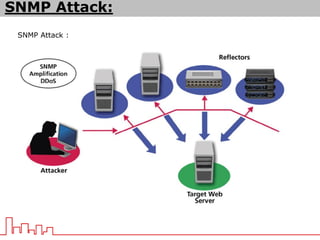
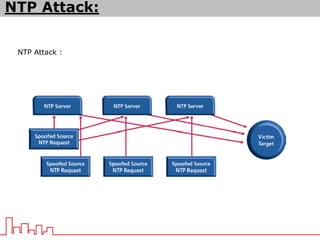
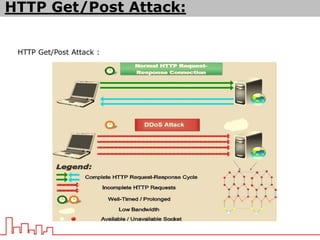
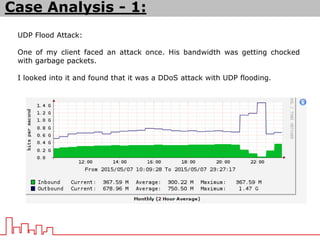
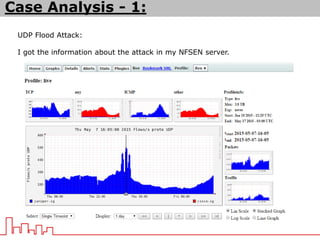
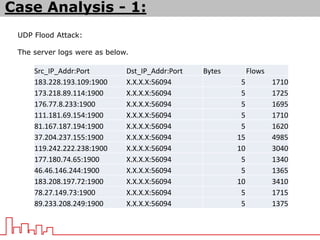
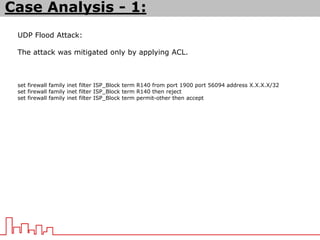
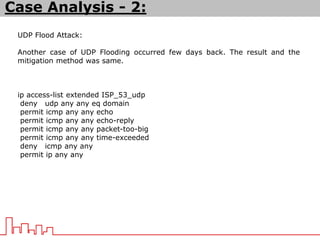
The document provides information about different types of DDoS attacks including DoS, DDoS, DNS reflection, SYN reflection, SMURF, UDP flood, SNMP, NTP, HTTP GET, and HTTP POST attacks. It describes how each attack works and overloads the target system with traffic. Mitigation techniques are also outlined, such as firewalls, rate limiting, authentication, and modifying server configurations.