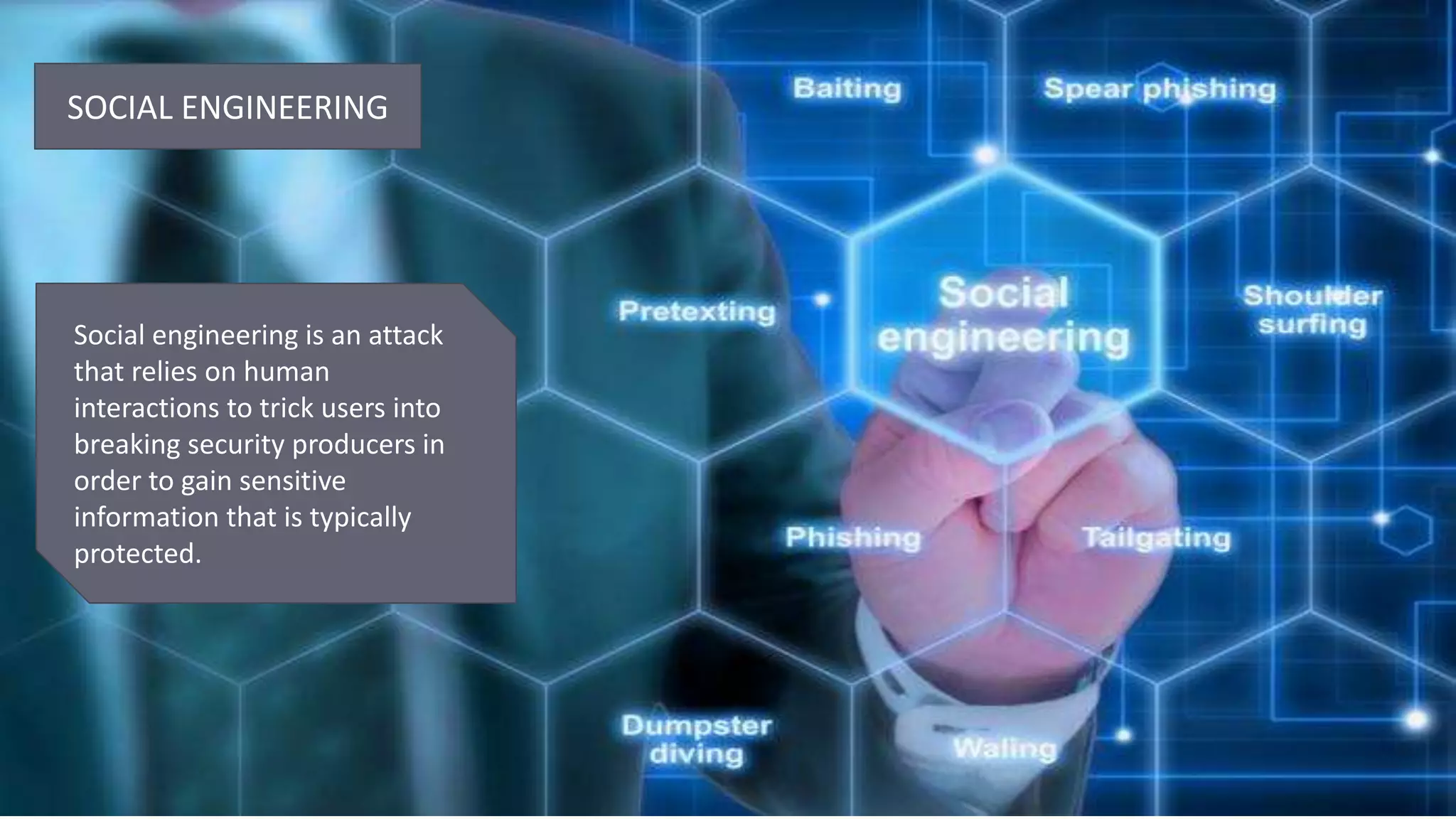
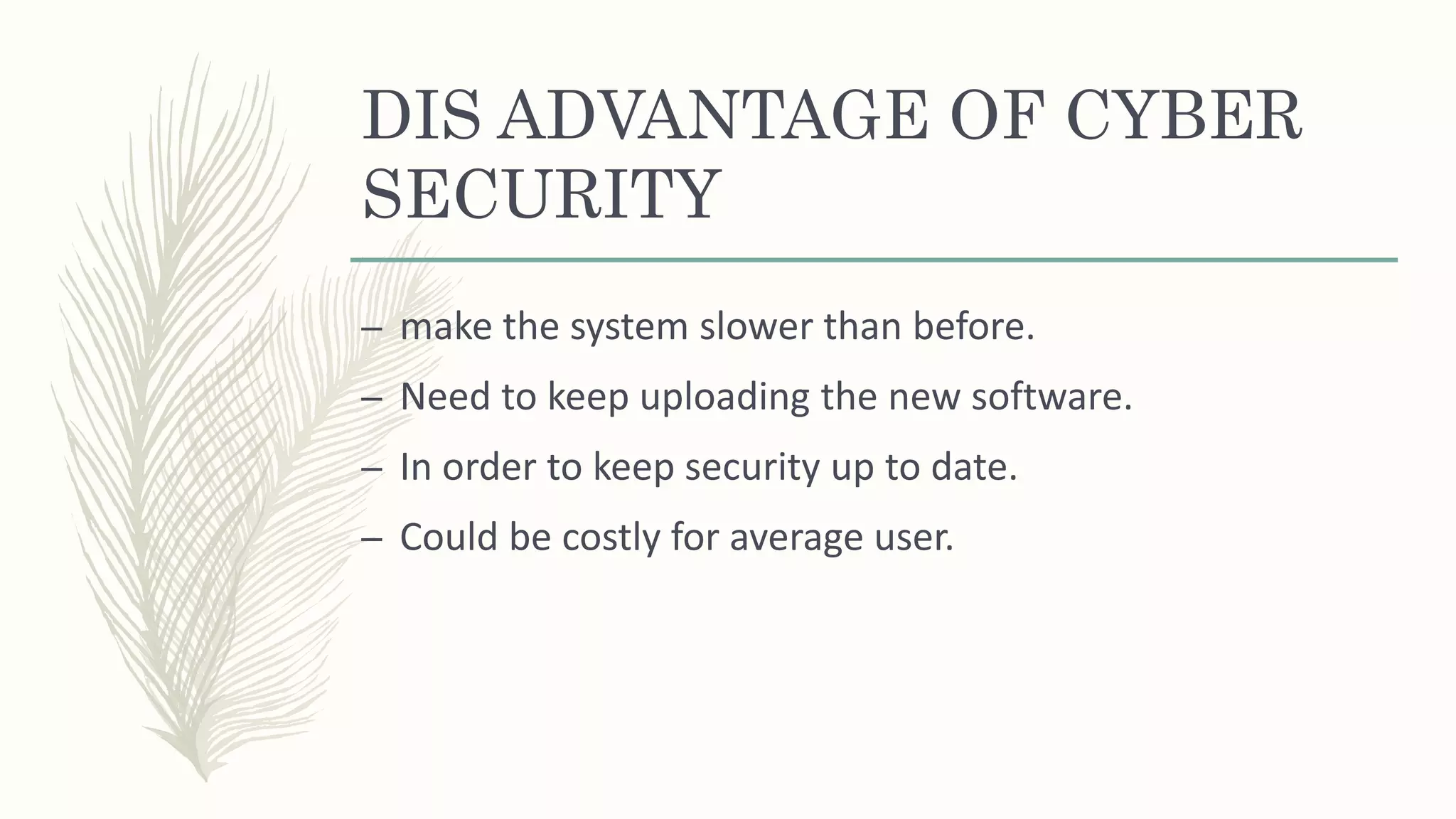
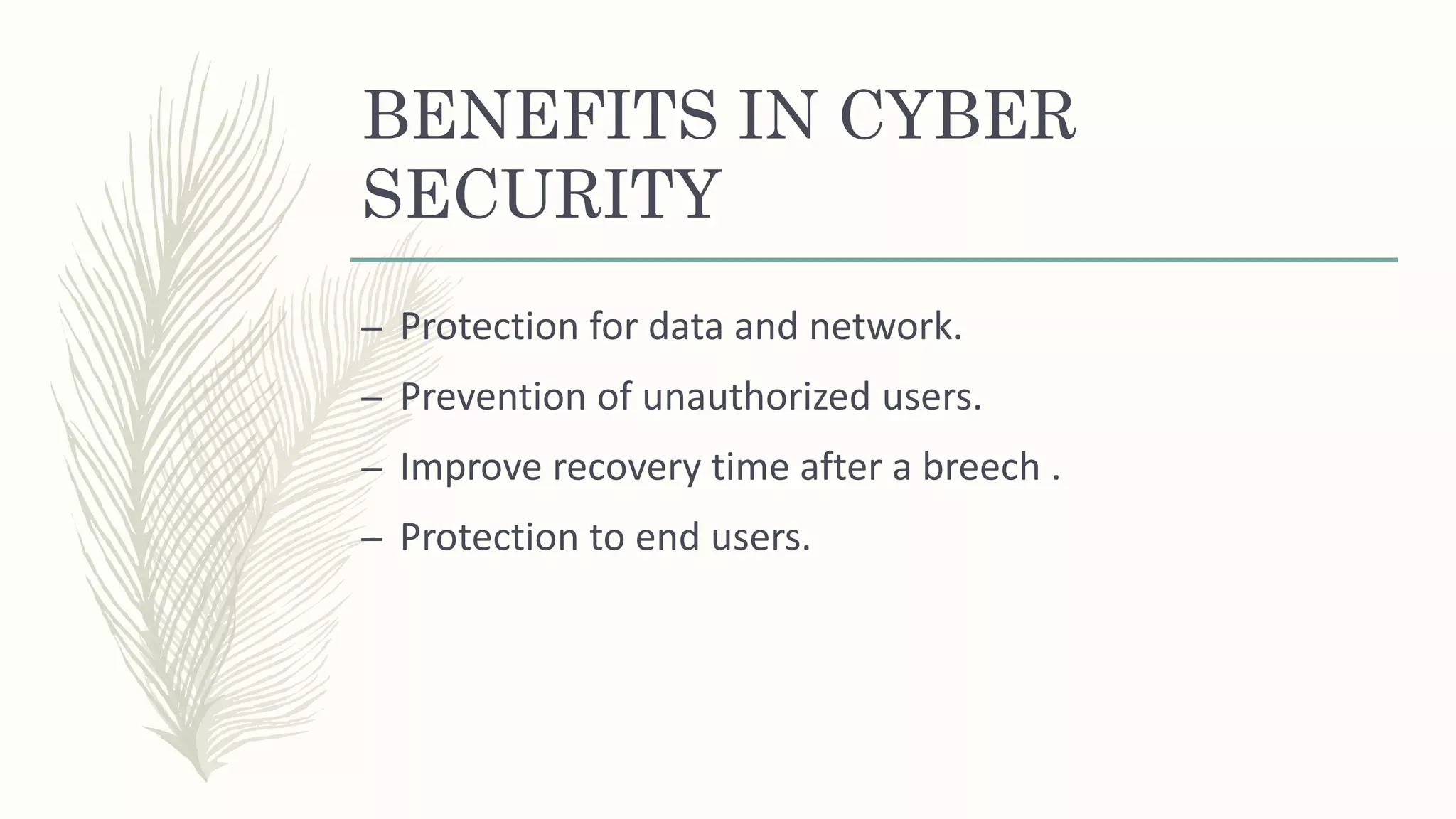
This document discusses cyber security, including types of threats like ransomware, malware, social engineering and phishing. It also covers cyber security vendors and the advantages and disadvantages of cyber security. The main benefits are protection of data and networks, prevention of unauthorized access, and improved recovery from security breaches. Cyber security helps defend against hacks and viruses but can slow systems down and require frequent software updates.