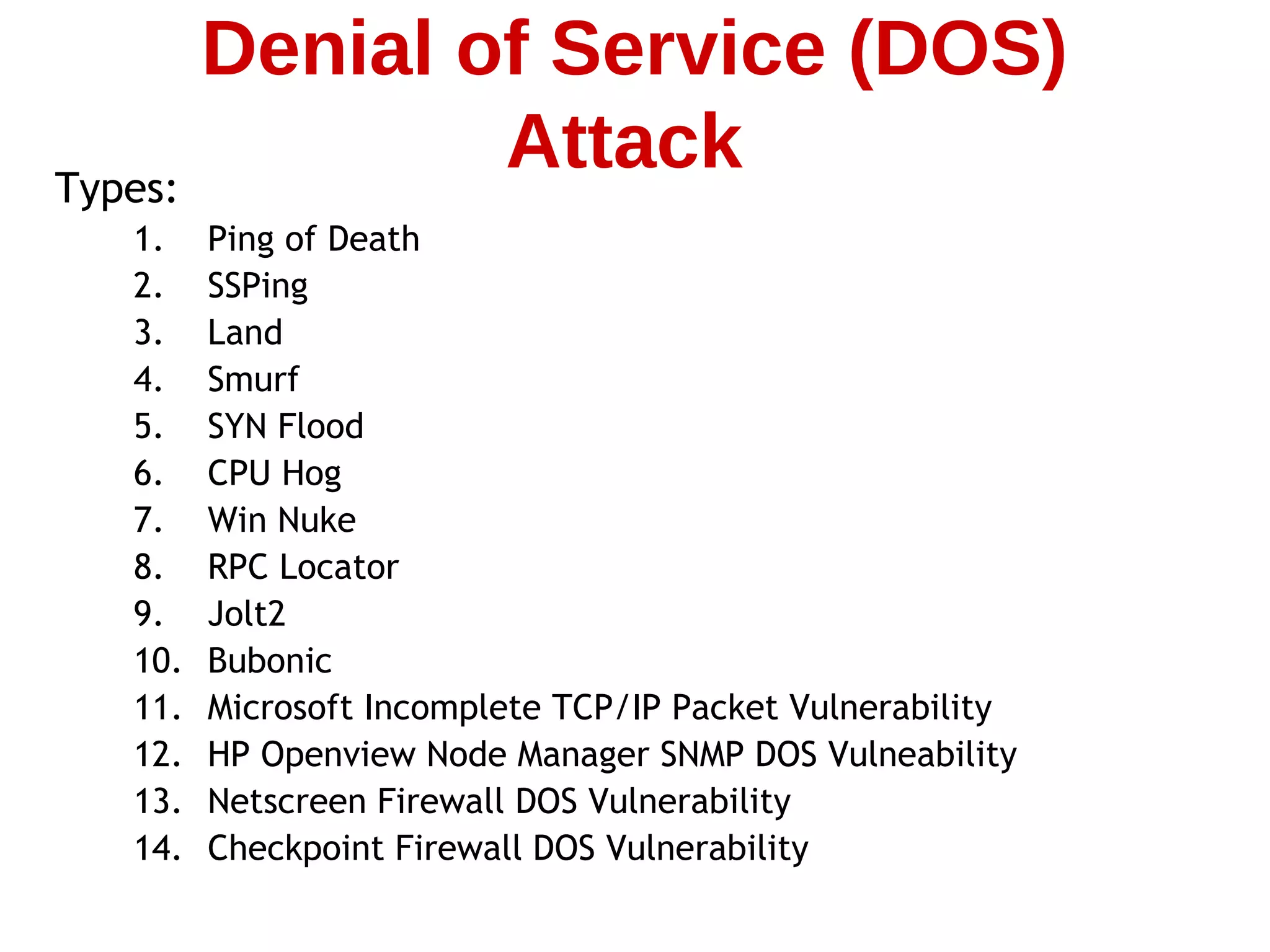
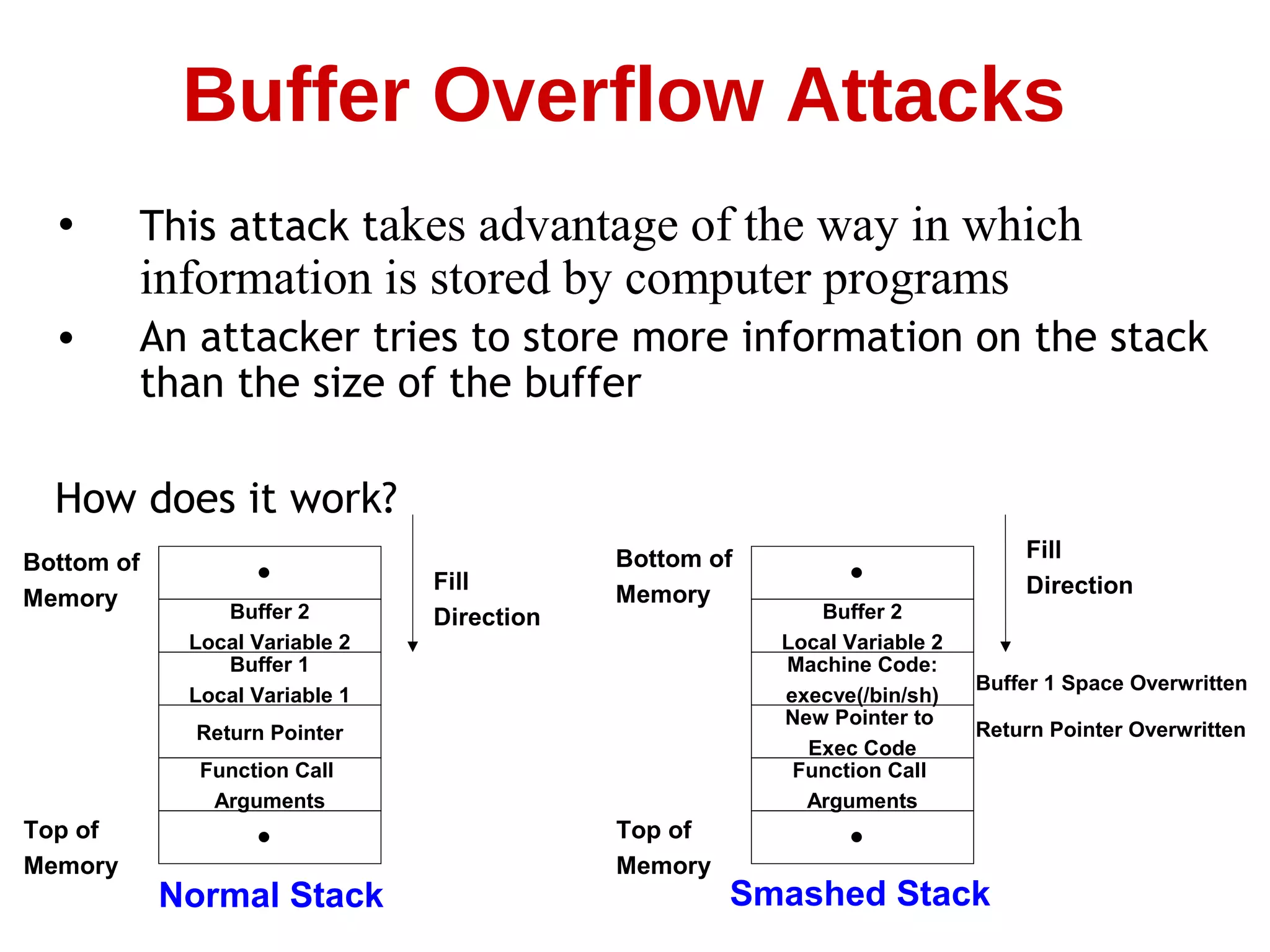
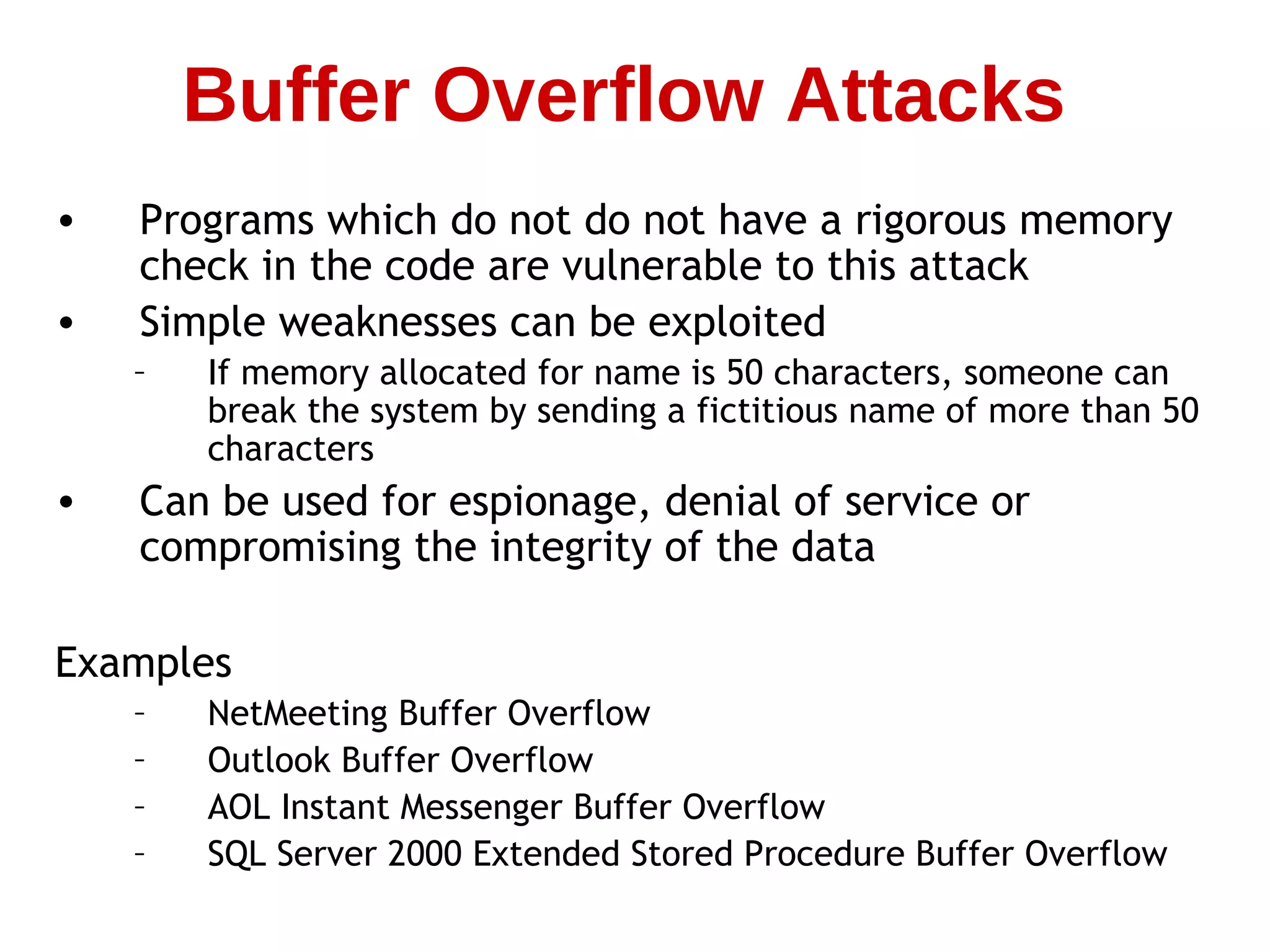
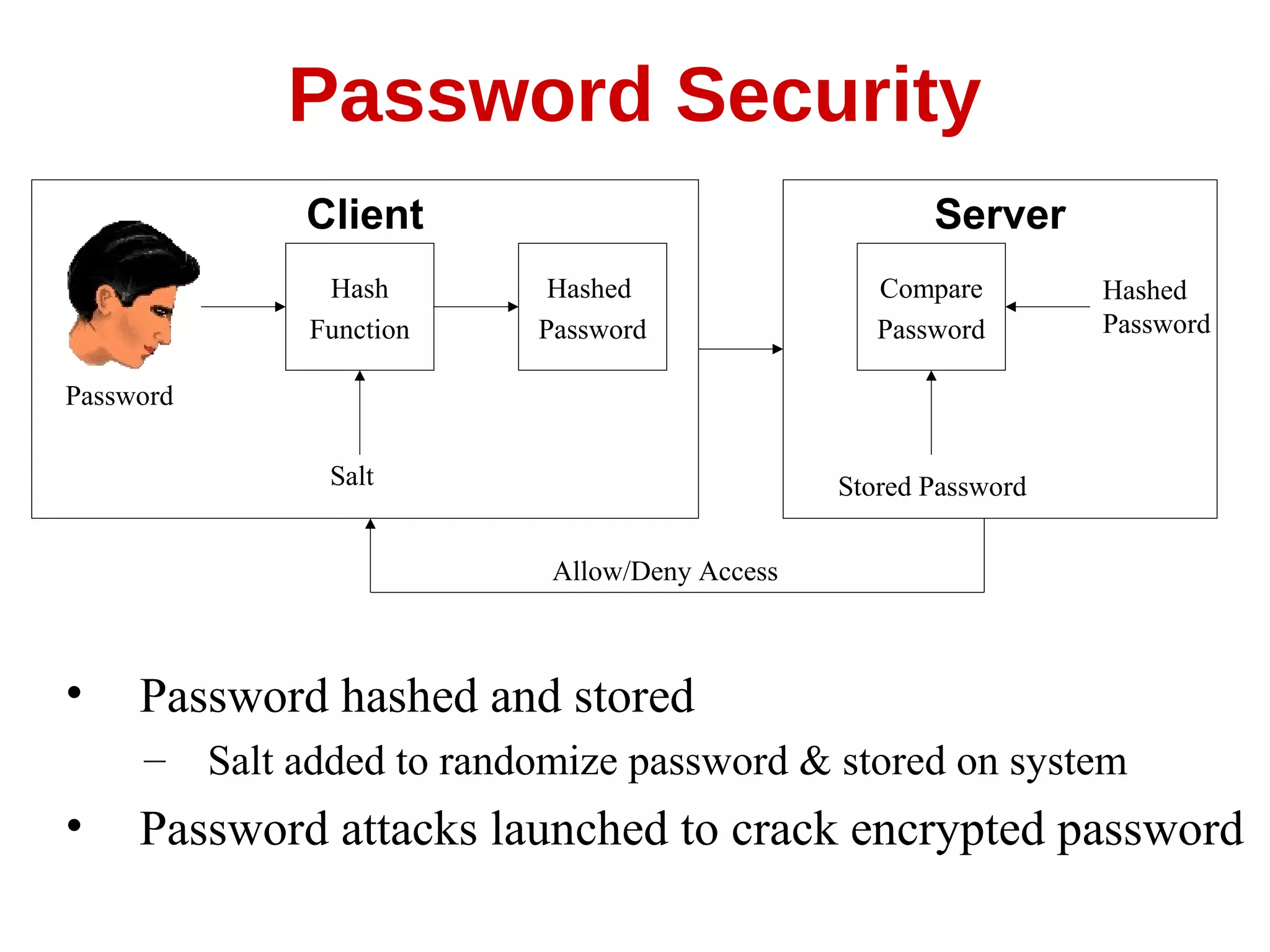
This document summarizes information about computer security and hacking. It discusses how the internet has grown rapidly while security has lagged behind, allowing legions of hackers to emerge. It covers various types of computer crimes throughout history from the 1980s to 2000s involving viruses, financial theft, and denial of service attacks. The document also describes common hacking techniques like spoofing, session hijacking, buffer overflows, password cracking, and denial of service attacks. It emphasizes that computer security requires ongoing improvement as hackers become more sophisticated over time.