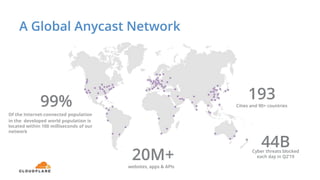
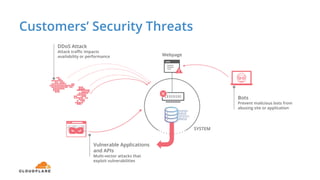
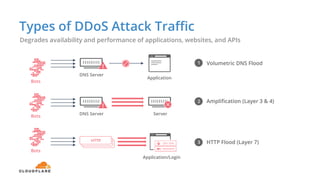
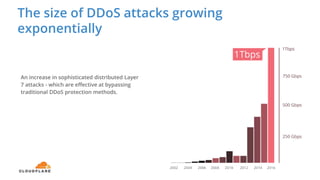
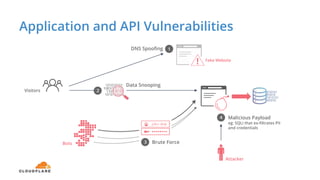
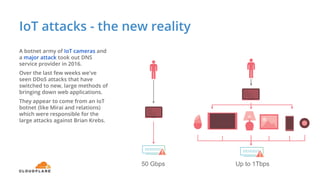
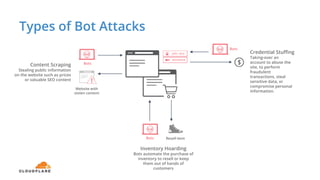
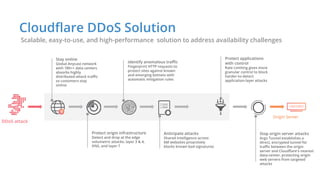
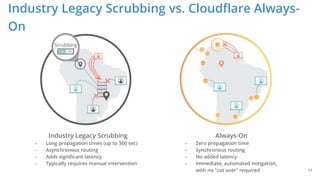
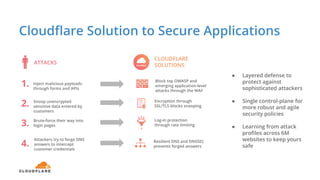
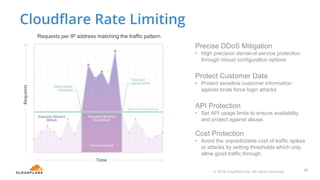
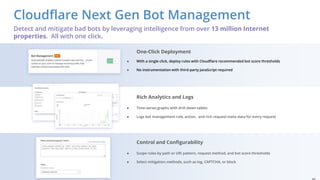
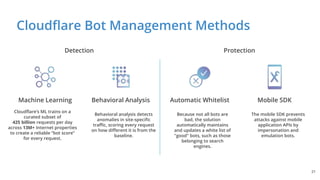
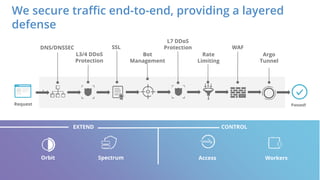
The document discusses cyber security fundamentals and challenges, describing how Cloudflare provides security solutions like DDoS mitigation, bot management, and web application firewalls to protect websites and applications from threats. It explains common security threats like DDoS attacks, bots, and vulnerabilities and how Cloudflare uses a global network and machine learning to detect and block attacks while ensuring high performance and availability.