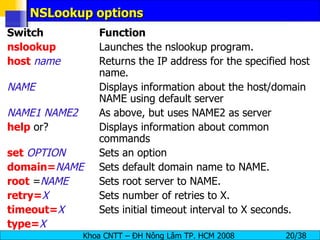
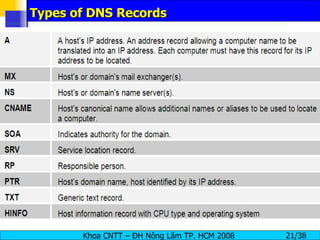
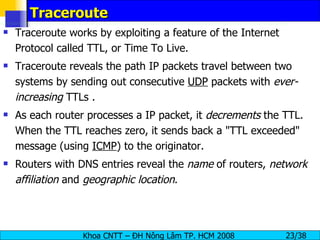
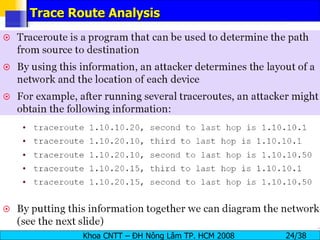
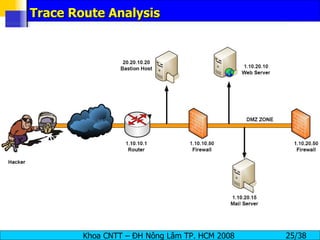
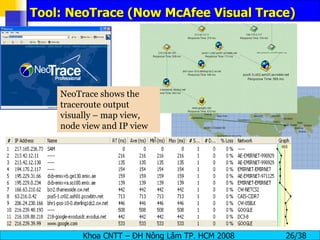
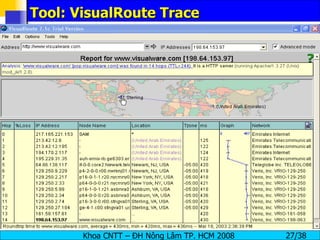
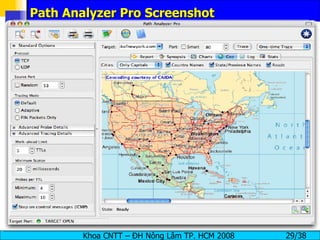
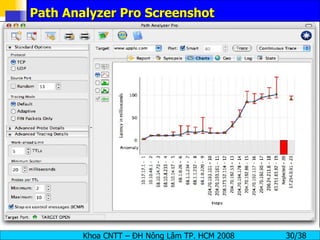
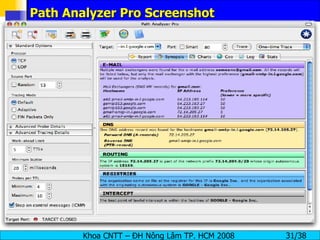
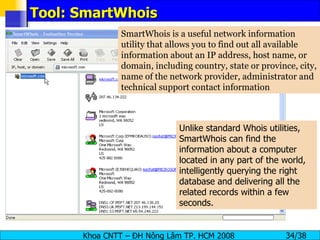
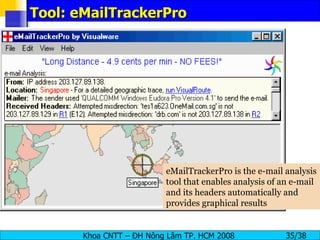
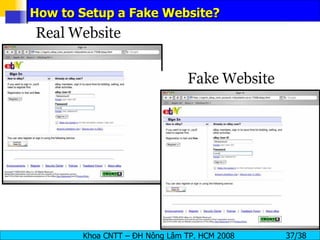
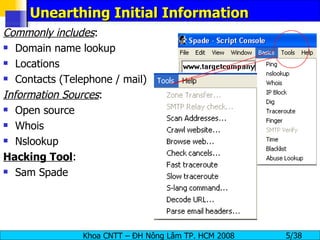
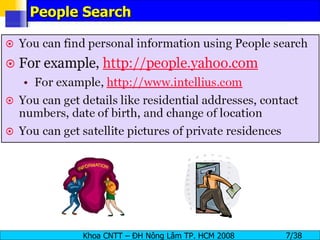
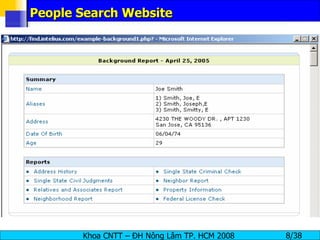
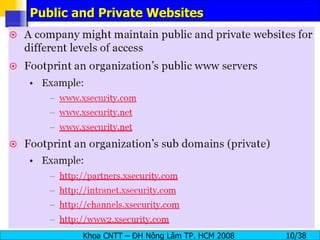
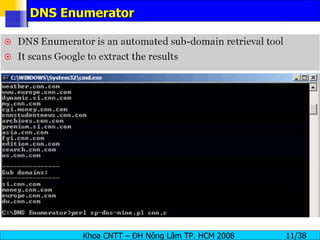
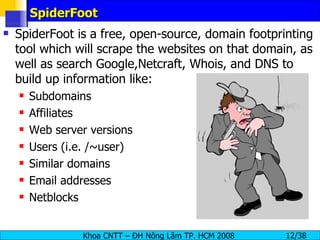
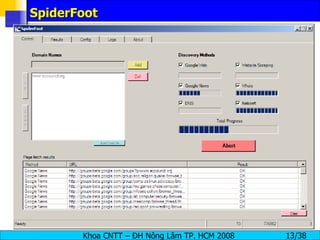
The document provides an overview of footprinting, which is the first stage of reconnaissance during a cyber attack. It involves gathering open-source information about a target organization to understand its security profile and map its network. Some of the tools mentioned for footprinting include Whois, Nslookup, traceroute, Google Earth and various online databases to find domain information, network details, employee names and more. The goal is to learn as much as possible about the target before launching an actual attack.





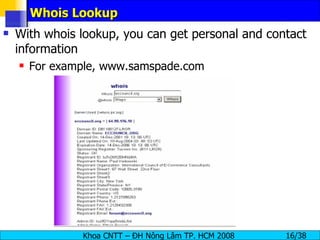
![Whois Registrant: targetcompany (targetcompany-DOM) # Street Address City, Province State, Pin, Country Domain Name : targetcompany.COM Domain servers in listed order: NS1.WEBHOST.COM XXX.XXX.XXX.XXX NS2.WEBHOST.COM XXX.XXX.XXX.XXX Administrative Contact: Surname, Name (SNIDNo-ORG) t [email_address] targetcompany (targetcompany-DOM) # Street Address City, Province, State, Pin, Country Telephone: XXXXX Fax XXXXX Technical Contact : Surname, Name (SNIDNo-ORG) t [email_address] targetcompany (targetcompany-DOM) # Street Address City, Province, State, Pin, Country Telephone: XXXXX Fax XXXXX](https://image.slidesharecdn.com/module2-footprinting-091013102856-phpapp02/85/Module-2-Foot-Printing-17-320.jpg)