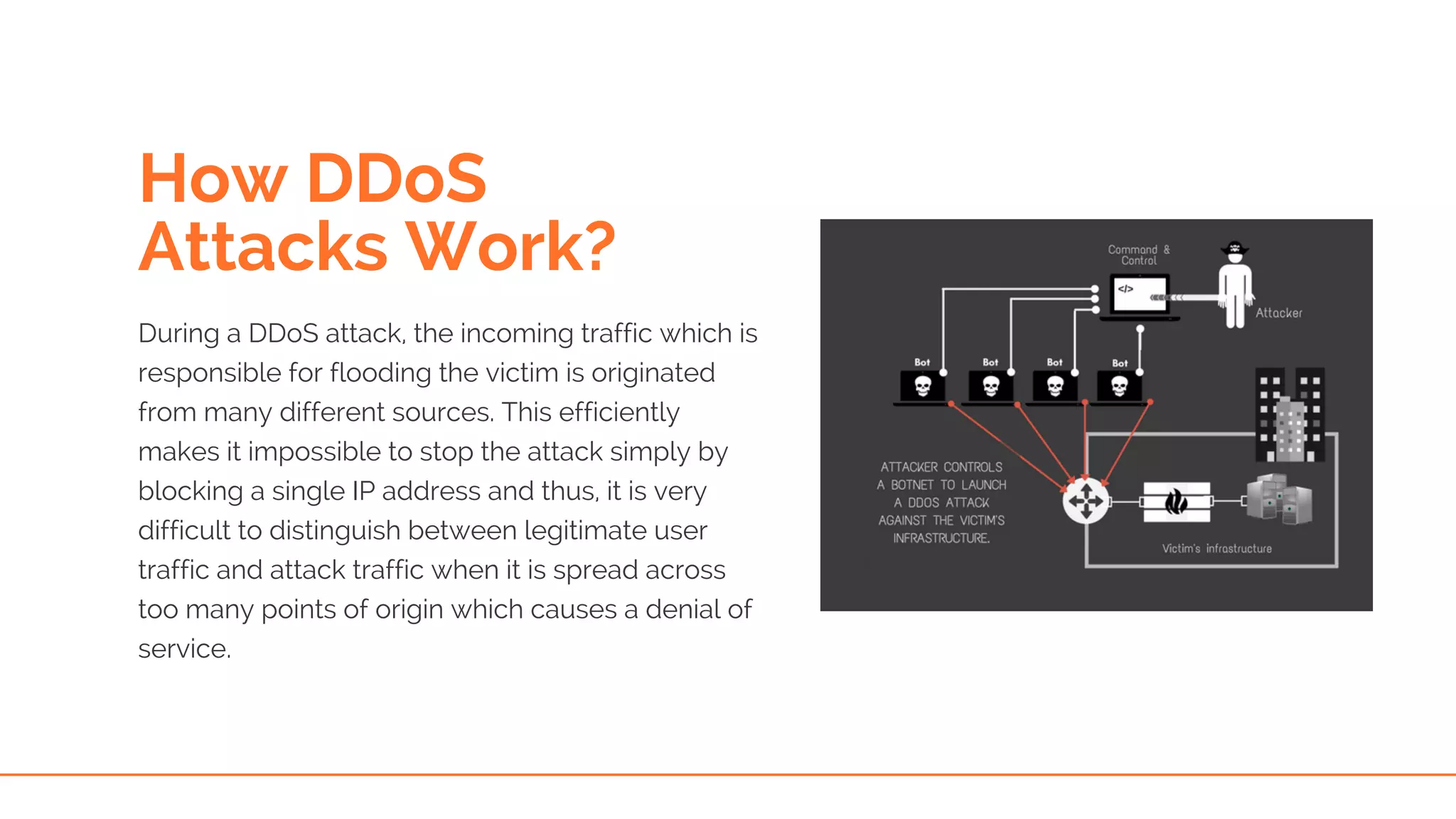
This document provides an overview of DDoS (Distributed Denial of Service) attacks, explaining their mechanisms and various types, including application level, zero day, ping flood, and more. It highlights the challenges businesses face with the increasing prevalence of these attacks and the difficulty in distinguishing between legitimate and illegitimate traffic. Additionally, it emphasizes the need for enhanced security measures, such as web application firewalls, to combat these threats.