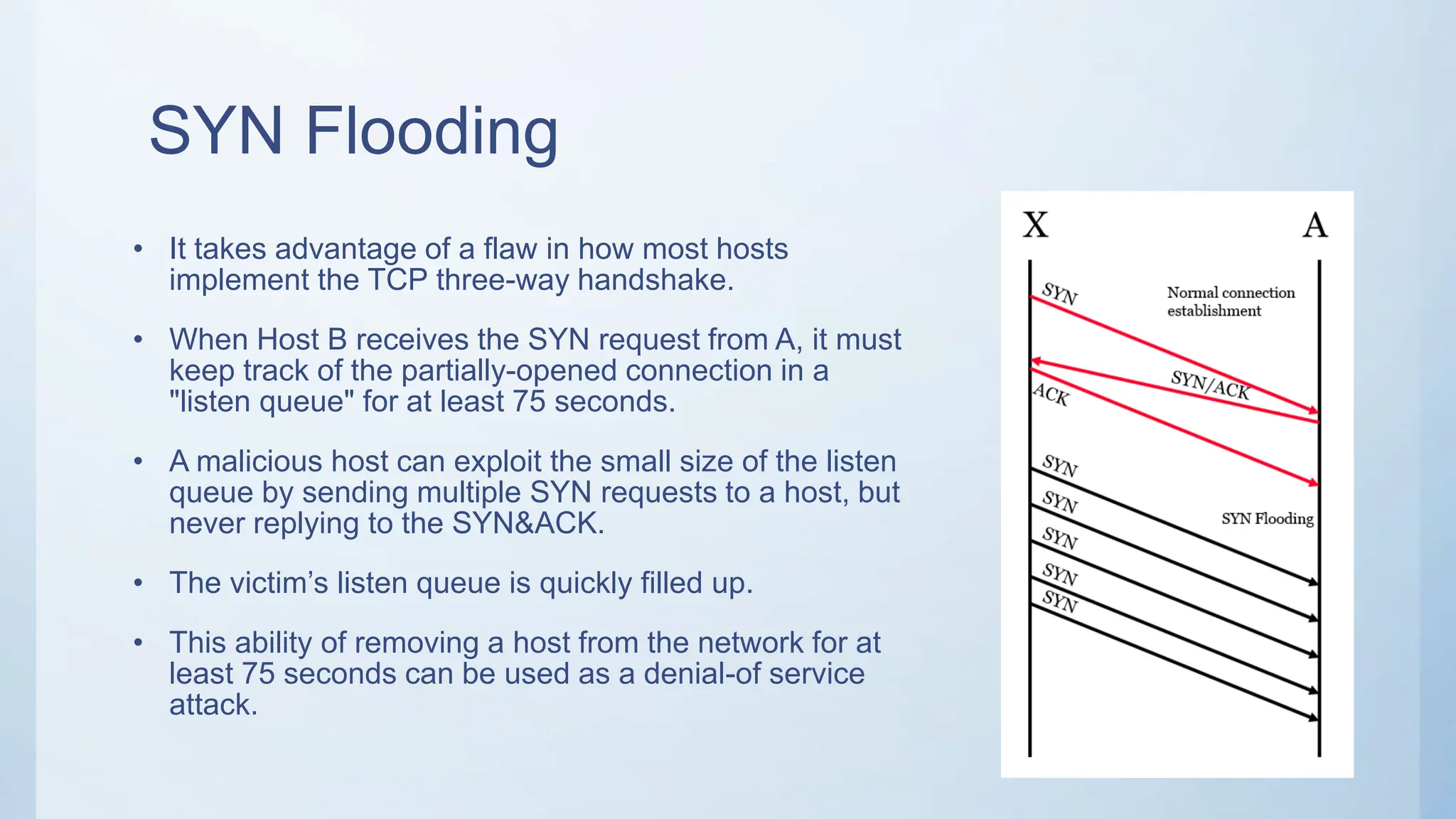
The document discusses denial of service (DoS) and distributed denial of service (DDoS) attacks. It defines DoS attacks as attempts to render a system unusable or slow it down for legitimate users by overloading its resources. DDoS attacks multiply the effectiveness of DoS by using multiple compromised computers to launch attacks simultaneously. Common DoS attack types like SYN floods, smurf attacks, and ping of death are described. The rise of botnets, which are networks of compromised computers controlled remotely, enable large-scale DDoS attacks that are difficult to defend against. Ways to mitigate DDoS attacks include load balancing, throttling incoming traffic, and using honeypots to gather attacker information.