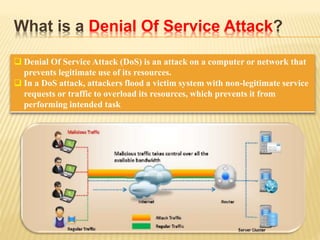
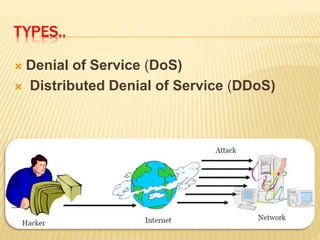
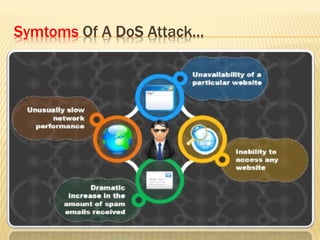
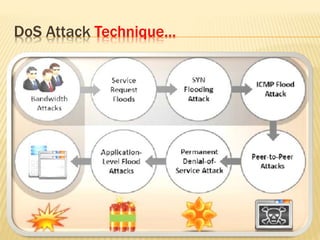
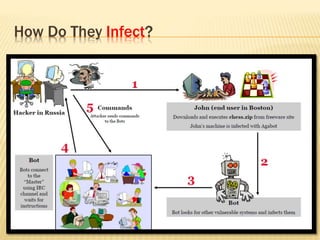
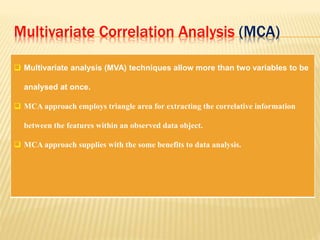
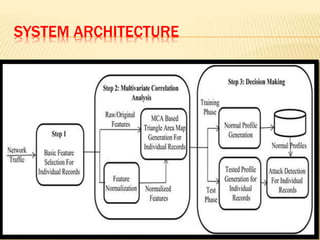
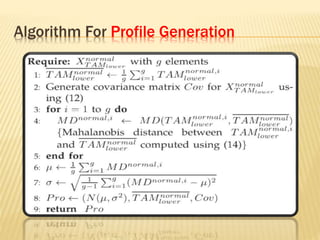
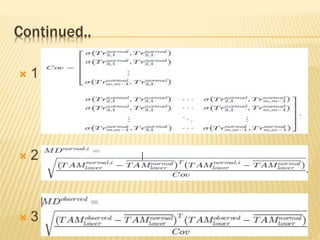
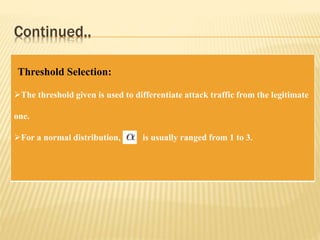
This document describes a system for detecting denial-of-service (DoS) attacks based on multivariate correlation analysis (MCA). The system generates normal traffic profiles using MCA to analyze legitimate training records. It then measures the dissimilarity between live traffic and normal profiles using Mahalanobis distance, flagging records above a threshold as potential attacks. If a record's distance exceeds the threshold, it is identified as a DoS attack. The system is intended to accurately detect both known and unknown DoS attacks compared to existing detection methods.