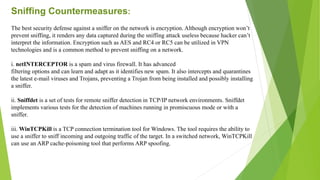
Packet sniffing tools like Ethereal and Snort can be used to intercept network traffic for diagnostic or malicious purposes. Sniffing tools capture packets in either command line or GUI format and some can reassemble packets into original data like emails. Sniffing can reveal usernames, passwords, and other confidential information unless encryption is used. Common sniffing techniques include passive sniffing using hubs, active sniffing using ARP spoofing on switches, and MAC flooding to force switch traffic to a sniffer. Encryption renders captured data useless, while detection tools can find machines in promiscuous sniffing mode.