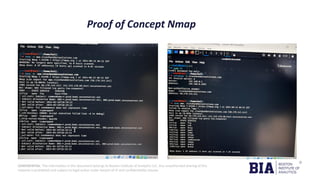
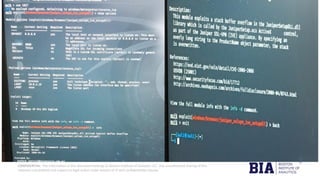
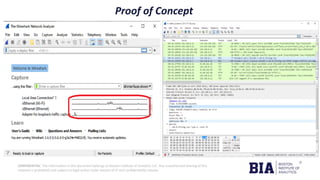
The document outlines tools and methods for information gathering in ethical hacking, emphasizing the significance of reconnaissance in the hacking process. It covers techniques such as active and passive information gathering, detailing specific tools like Nmap, Metasploit, and Wireshark, along with their functionalities and applications. Additionally, it highlights best practices for preventing cyberattacks and information leaks.