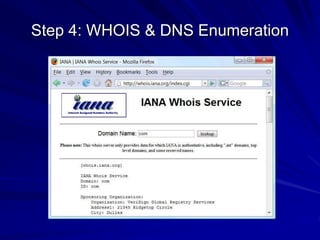
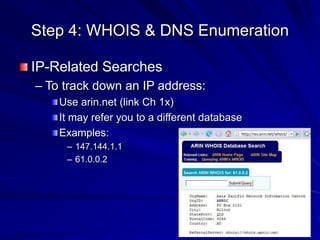
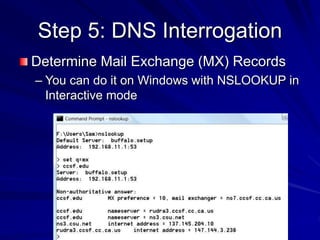
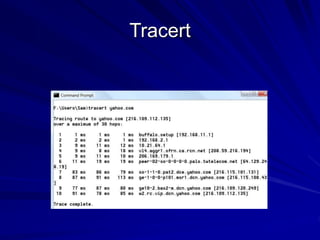
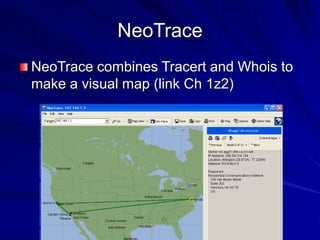
This document discusses techniques for footprinting and gathering information about a target organization without directly interacting with it. It covers searching public information on the internet and dark web, using tools like WHOIS and DNS lookups to identify key systems and infrastructure, and performing network reconnaissance using traceroute to map the network layout. The goal is to understand the target before engaging with it directly by exploiting any vulnerabilities found during footprinting.