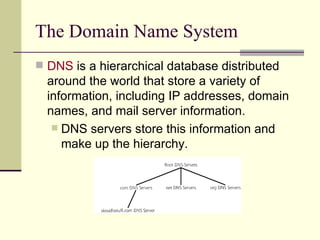
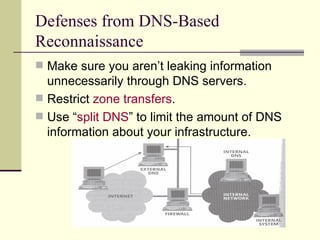
The document discusses various techniques for reconnaissance, including searching public information on the internet, using tools to scan for open systems and services, and ways to map out network configurations. It provides details on low-tech methods like searching websites, Whois databases and DNS, as well as technical scanning tools to discover active systems, network topology, and open ports. The document also offers defenses against some of these reconnaissance techniques.