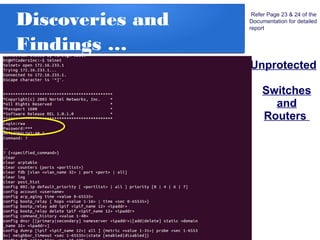
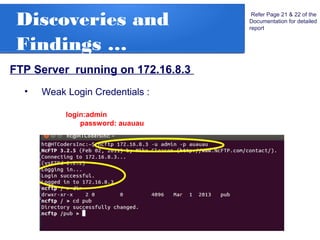
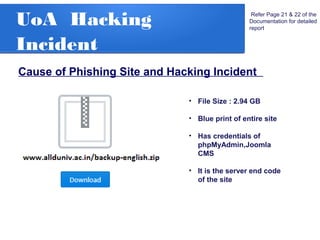
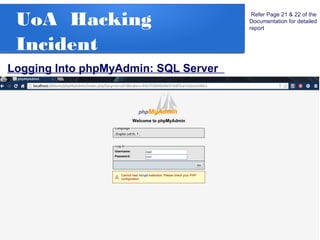
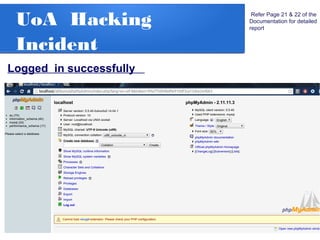
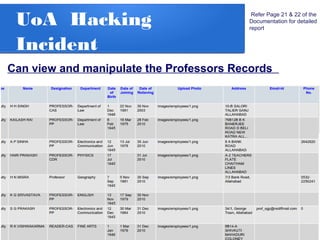
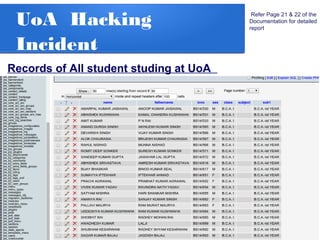
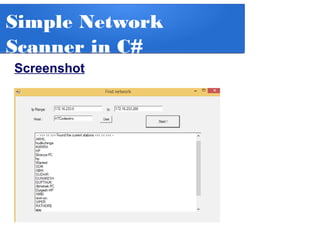
The document details a penetration testing project conducted by Rishabh Upadhyay as part of his BCA program at the University of Allahabad, focusing on ethical hacking methodologies and network vulnerability assessments. Key findings highlight unprotected network devices, weak login credentials for various systems, and a demonstration of a man-in-the-middle attack. A simple network scanner was also developed to identify computers within a specified domain.
![Ethical Hacking
&
Penetration Testing
Center of Computer
Center of Computer Education and Training
Institute of Professional Studies
December 23,2014
By: Rishabh Upadhyay
Batch: BCA[2012-15]
Under the Guidence of
Prof. R.R.Tewa](https://image.slidesharecdn.com/pt-140920065300-phpapp02/75/Ethical-Hacking-and-Penetration-Testing-1-2048.jpg)


















![Thank You !!
Center of ComputerCenter of Computer Education and Training
Institute of Professional Studies
December 23,2014
By: Rishabh Upadhyay
Batch: BCA[2012-15]](https://image.slidesharecdn.com/pt-140920065300-phpapp02/85/Ethical-Hacking-and-Penetration-Testing-45-320.jpg)