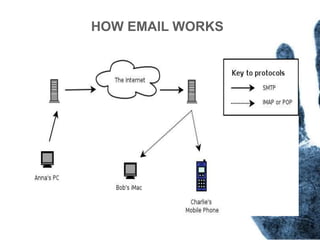
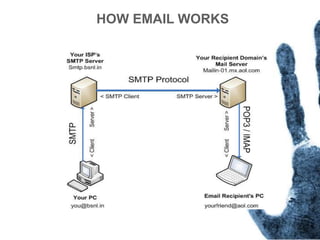
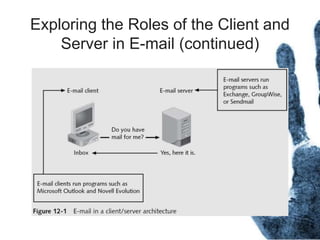
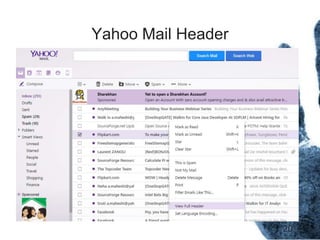
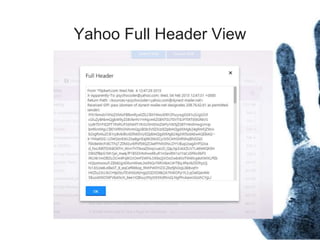
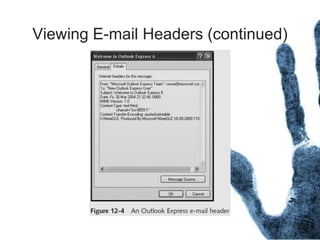
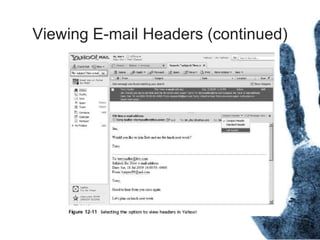
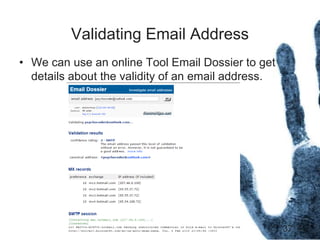
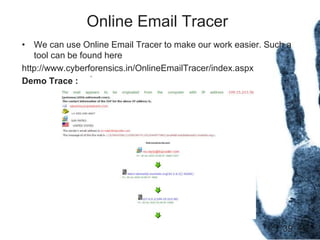
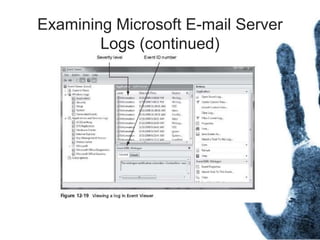
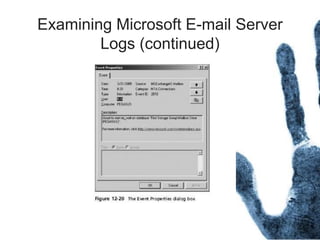
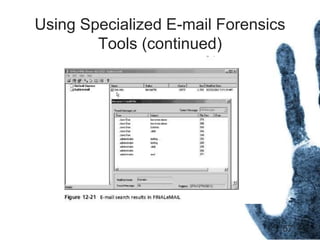
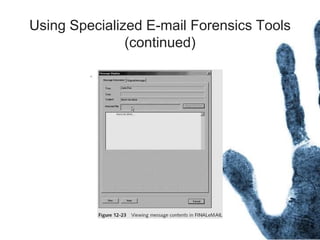
The document outlines the processes and techniques involved in email investigations, including understanding email architecture, roles of clients and servers, and methods to examine, recover, and analyze email evidence. It covers various crime types facilitated by email, tools for email forensics, and emphasizes the importance of tracking email headers and server logs. Additionally, it highlights the challenges related to deleted emails and the utility of advanced forensic tools in recovering such data.