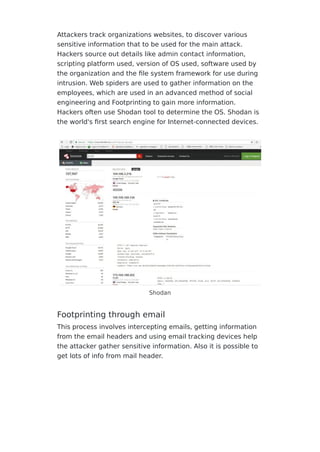
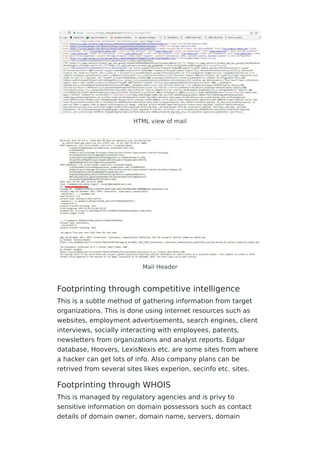
This document provides an overview of footprinting and reconnaissance techniques used by hackers to gather sensitive information about target organizations. It discusses various footprinting methods like using search engines, social media, websites, email headers, WHOIS lookups and more to find out details on employees, network infrastructure, systems and technologies used. The document also outlines tools that can be used for footprinting and recommends steps organizations can take to prevent information leakage and footprinting attacks like limiting employee access, filtering website content, encoding sensitive data and conducting regular security assessments.
![information, location information and so on) and network
information (domain name, VPN points, authentication means
and so on).
The methods behind Footprinting
There are a couple of methods, which hackers use to get
sensitive data from organizations. These methods in
conjunction with other tools carry out social engineering
manipulations, which ultimately lead to attacks and hacking,
these methods are -
Footprinting through Search engines
Attackers get information such as login pages, employees’
information, internet portals and others from search engines.
Attacks still have access to sensitive information taken off the
internet, through internet archives or search engine caches.
Websites like netcraft.com allow attackers gain access to their
target organizations restricted websites.
Footprinting through advanced Google hacking
Google hacking methods involve using advanced and arduous
queries forms to gain sensitive information from the targets,
discovering venerable targets, and using google search means
to uncover specific string of texts. This method allows
attackers discover sites connected to the company’s website,
extract information on customers, business partners and
vendors, and make the information gathered concise. Several
operators (e.g - [allintitle:], [link:], [cache:] etc.) and filters can
be used in Google to search personal info.
Footprinting through social media platforms
Employees post information about their personal lives, as well
as information regarding their companies. For instance,
employees use social media to reveal things like new clients,
fresh deals, and company news and business partners.
Attackers open new pages, track these employees and try to
gain more information.
Footprinting through website to determine OS](https://image.slidesharecdn.com/footprinting-180702071756/85/Footprinting-2-320.jpg)