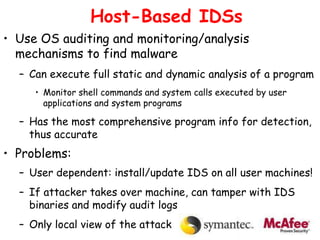
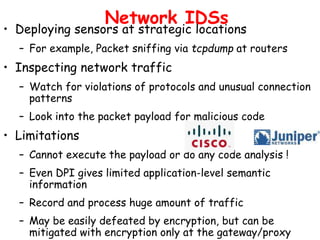
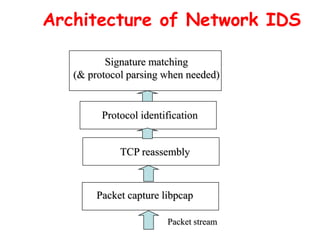
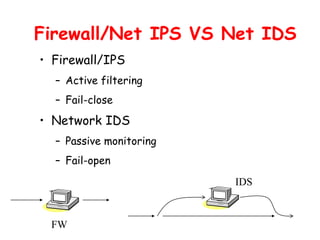
This document discusses intrusion detection and prevention systems. It defines intrusion, intrusion detection, and intrusion prevention. It describes the components and approaches of intrusion detection systems, including misuse detection, anomaly detection, host-based detection, and network-based detection. It compares the pros and cons of different approaches and deployment methods. It also discusses key metrics, architectures, and examples like Snort.





![Misuse Detection
Intrusion
Patterns:
Sequences of
system calls,
patterns of
network traffic,
etc.
activities
pattern
matching
intrusion
Can’t detect new attacks
Example: if (traffic contains “x90+de[^rn]{30}”) then “attack detected”
Advantage: Mostly accurate. But problems?](https://image.slidesharecdn.com/ids-231014220644-689d5672/85/ids-ppt-7-320.jpg)