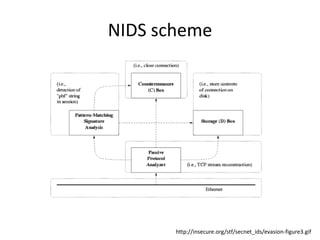
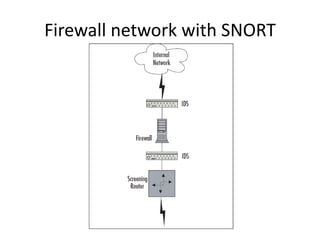
The document discusses network intrusion detection and prevention systems (NIDS), categorizing them into real-time detection types and analysis methods such as signature-based and protocol-based analysis. It emphasizes the challenges of dirty packets, sensor placement, and the importance of behavior analysis for effective detection of malicious activity. Tools like Snort, OSSIM, and SGUIL are highlighted as key components of the NIDS ecosystem, along with their various add-ons for enhanced functionality.