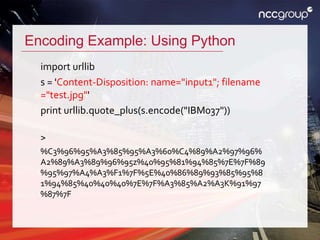
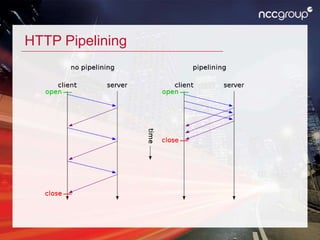
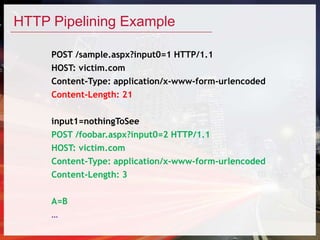
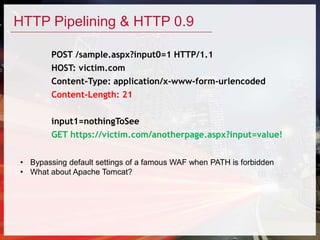
This document discusses various techniques for HTTP request smuggling and bypassing web application firewalls as presented in a talk by Soroush Dalili. It explores the vulnerabilities of different web servers and configurations, detailing methods to manipulate HTTP requests for security testing. The presentation emphasizes the need for continuous research and adaptation of strategies in web application security.