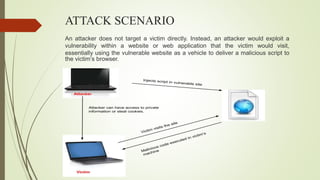
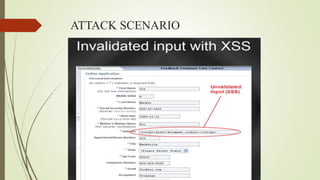
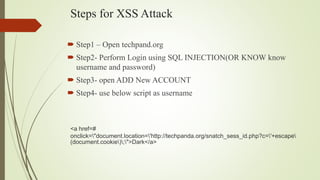
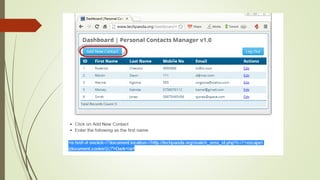
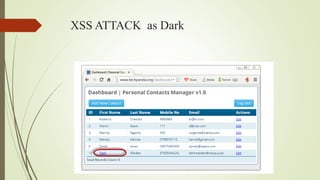
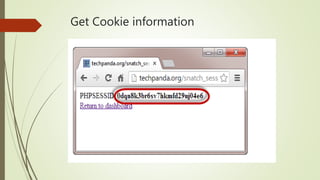
An XSS attack is a type of vulnerability that allows malicious scripts to be injected into web pages viewed by other users. There are three main types: reflected XSS occurs when a link containing malicious code is clicked; stored XSS injects code directly into a vulnerable website, potentially affecting many users; DOM-based XSS involves injecting code into a website hosted on a user's local system, allowing the attacker to access that user's browser privileges. The document provides examples of how XSS attacks work and can be used to hijack accounts, insert hostile content, steal cookies, and redirect users.