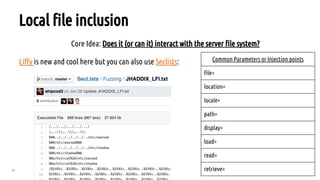
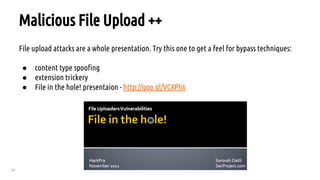
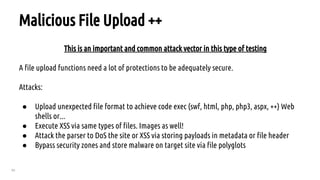
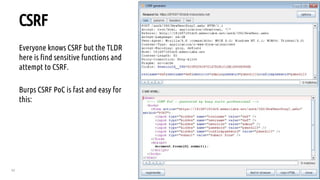
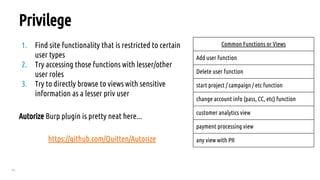
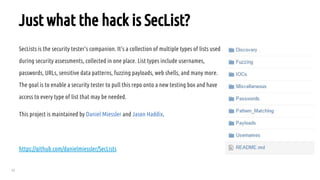
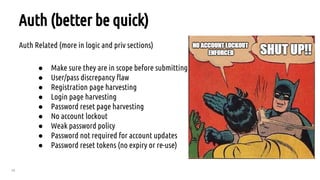
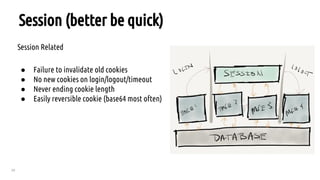
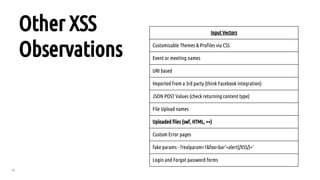
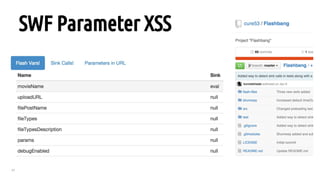
The document outlines a bug hunting methodology presented by Faraz Khan and based on Jason Haddix's original work. It covers strategies and tools used in discovering vulnerabilities through web and mobile bug hunting, including techniques for parsing, mapping, and exploiting various vulnerabilities. Key topics include the differences between standard penetration testing and bounty hunting, discovery techniques, and specific vulnerabilities such as XSS, SQL injection, and CSRF.





















![26
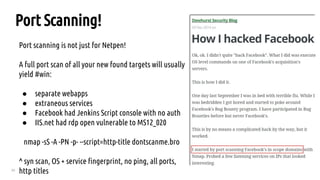
Directory Bruteforce Workflow
After bruteforcing look for other status codes indicating you are denied or require auth then
append list there to test for misconfigured access control.
Example:
GET http://www.acme.com - 200
GET http://www.acme.com/backlog/ - 404
GET http://www.acme.com/controlpanel/ - 401 hmm.. ok
GET http://www.acme.com/controlpanel/[bruteforce here now]](https://image.slidesharecdn.com/nullc0nbountyhuntingtechniques-160314053844/85/Bug-Bounty-Hunter-Methodology-Nullcon-2016-26-320.jpg)




















![55
XXE Tools - Testing & Exploitation
As the vulnerability is in its early stages we do not have any specific tool that totally concentrate on finding or exploiting
XXE, but as per automated scanning/finding we have Burp scanner, other updated automated vulnerability scanner which
are able to find XXE.
Simple Payload
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///dev/random" >]><foo>&xxe;</foo>
Exploitation:
Can be used to read system files + Other attacks SSRF is capable of.](https://image.slidesharecdn.com/nullc0nbountyhuntingtechniques-160314053844/85/Bug-Bounty-Hunter-Methodology-Nullcon-2016-55-320.jpg)