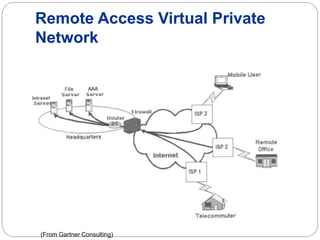
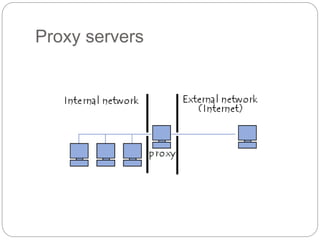
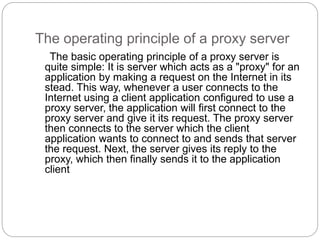
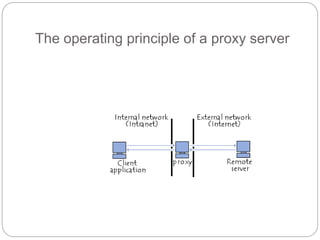
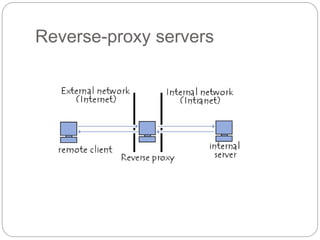
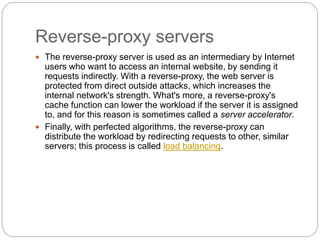
A firewall controls incoming and outgoing network traffic to protect devices from attacks. There are three main types: edge firewalls protect individual devices; appliance firewalls are dedicated firewall devices; and network firewalls protect entire networks using routers, bridges, or computer-based software. Firewalls are used to protect networks from probes and attacks, and provide security for less protected devices. Proxies act as intermediaries for network requests, allowing things like caching, filtering, authentication, and load balancing to improve security and performance. Reverse proxies specifically allow external users indirect access to internal servers and websites.