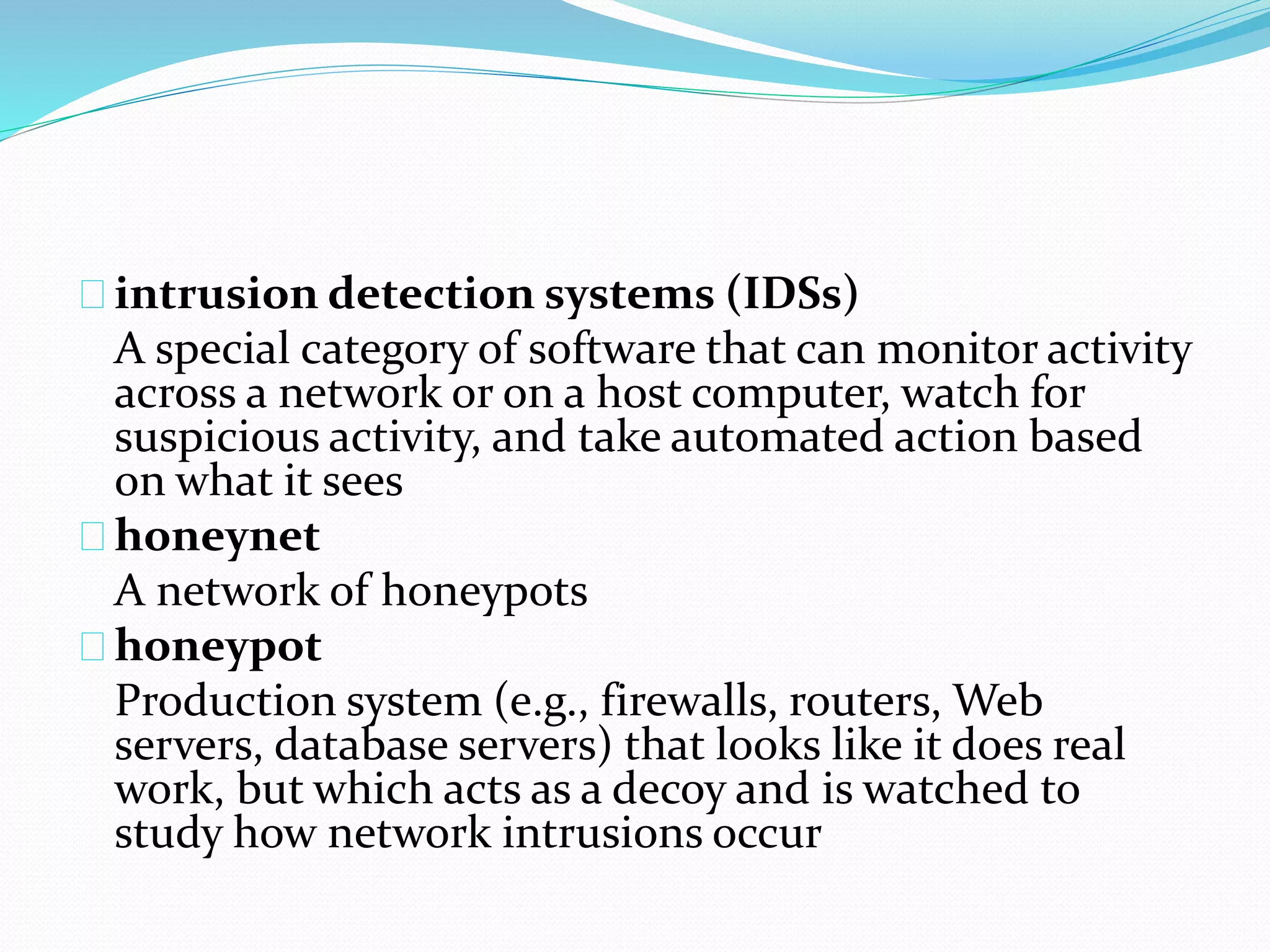
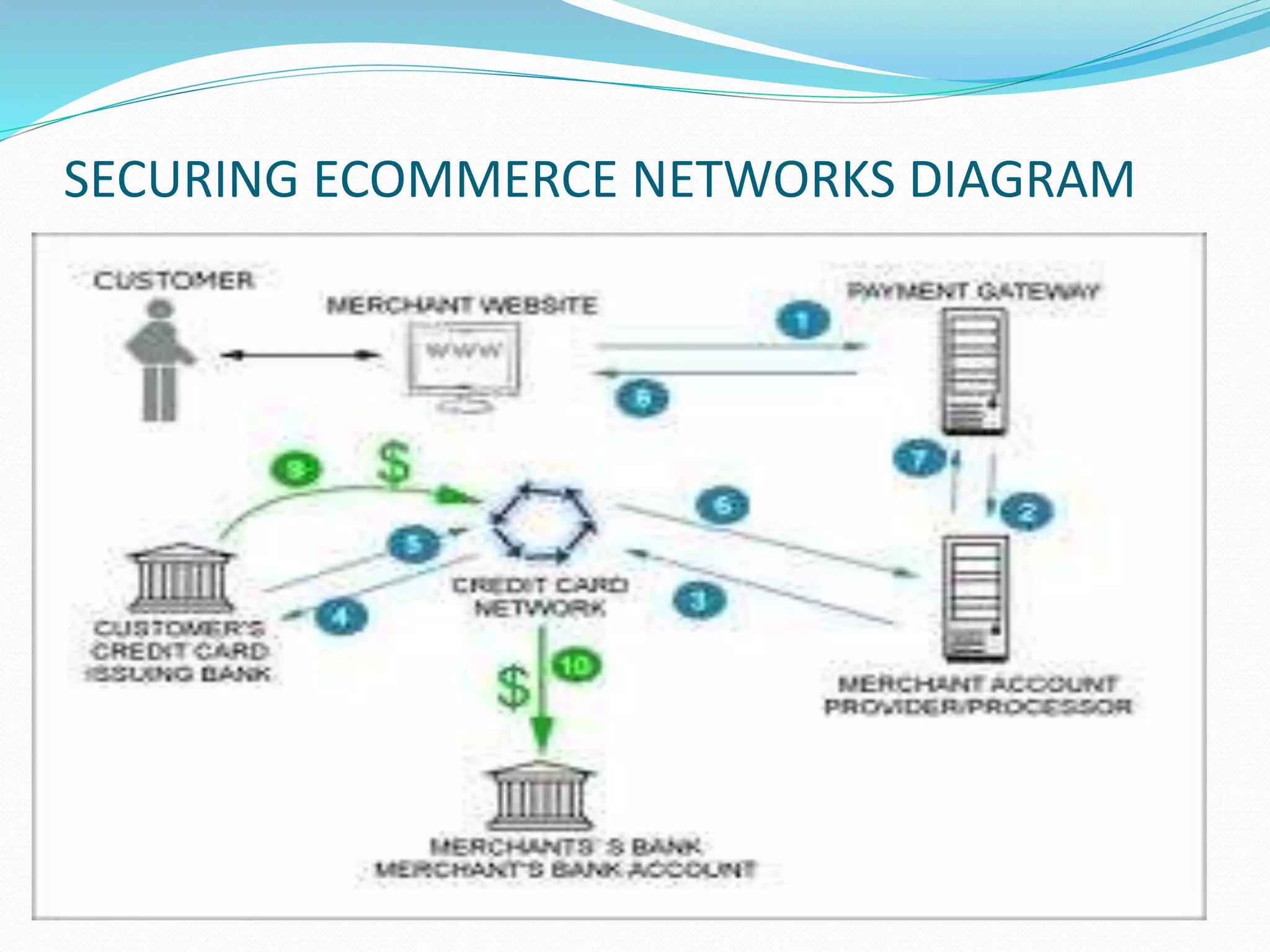
The document discusses various technologies for securing e-commerce networks, including firewalls, intrusion detection systems, virtual private networks, and public key infrastructure. Firewalls act as a barrier between private and public networks and control network traffic. Intrusion detection systems monitor network activity for suspicious behavior. Virtual private networks use encryption to create secure connections over public networks like the Internet. A public key infrastructure enables secure exchange of data and payments on public networks through use of public/private key pairs from a trusted authority.