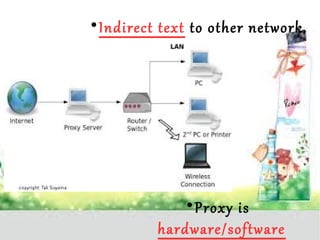
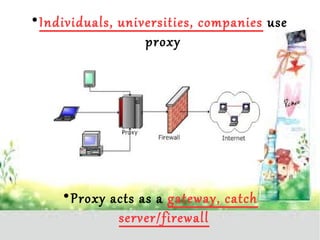
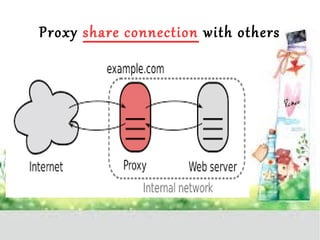
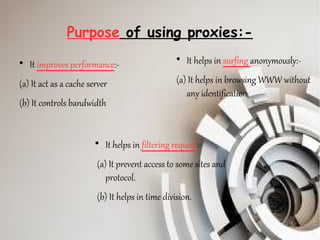
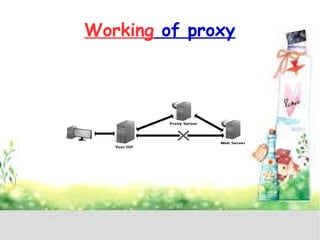
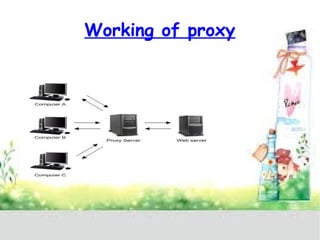
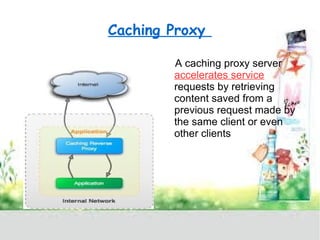
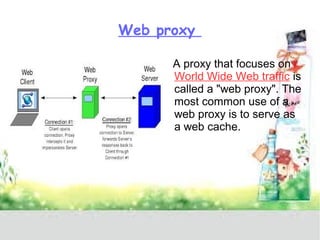
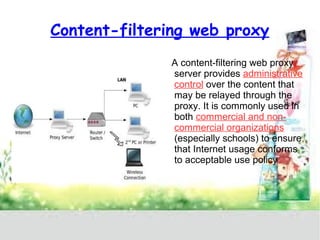
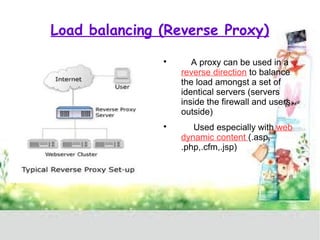
A proxy server acts as a gateway between users and the internet, improving performance through caching and bandwidth control while enabling anonymous browsing and content filtering. Different types of proxies serve various purposes, including web caching, content filtering, and anonymizing functions, enhancing security by hiding internal clients and blocking harmful content. The document outlines the operational benefits of proxy servers, including reduced latency and network traffic, and their application in both commercial and educational environments.