Embed presentation
Downloaded 38 times





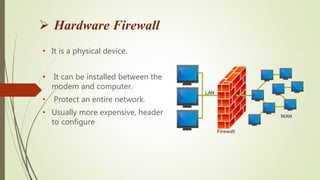
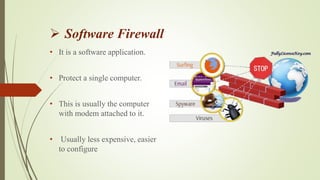


A firewall is a device or software that provides secure connectivity between internal and external networks by protecting confidential information from unauthorized access, and defending the network and its resources from malicious external users and accidents. There are two main types of firewalls - hardware firewalls which are physical devices that can protect an entire network but are more expensive and complex, and software firewalls which protect individual computers and are cheaper and simpler to configure. Firewall techniques include packet filtering, application gateways, proxy servers, circuit-level gateways, and bastion hosts.








