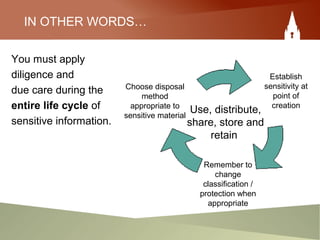
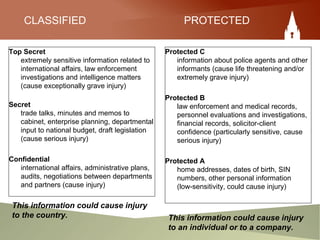
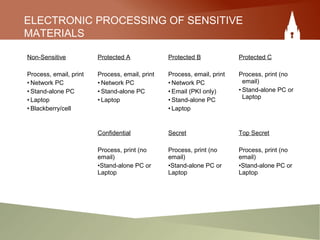
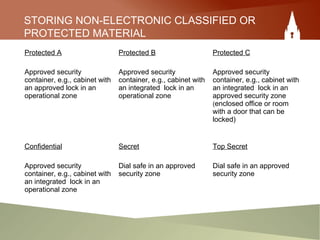
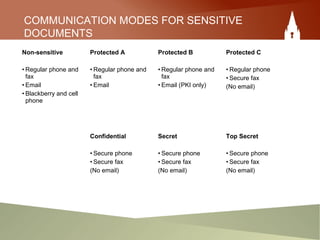
This document provides an overview of an employee's responsibilities regarding information security as a government of Canada employee. It discusses classifying documents as protected or classified based on the potential harm if compromised. It also covers marking documents with security classifications, appropriate storage and handling of sensitive materials, distributing information on a need-to-know basis, removing classifications when no longer needed, and destroying materials securely. The document aims to ensure employees are aware of proper processes for managing sensitive information throughout its lifecycle within the government.