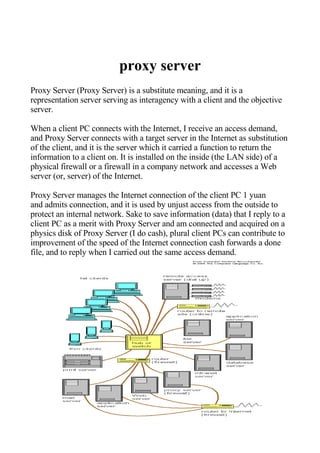
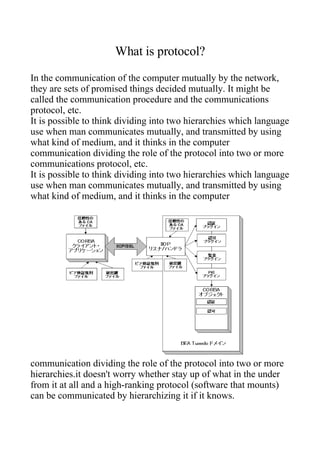
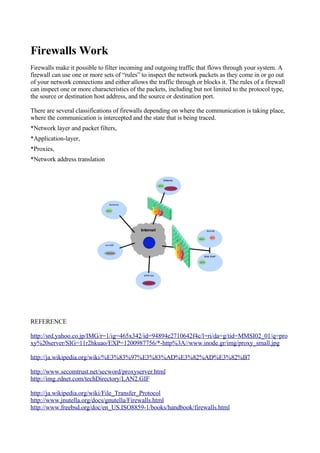
A proxy server acts as an intermediary between a client and an external server. When a client makes a request, the proxy server connects to the target server on the client's behalf and returns the information to the client. Proxy servers can cache responses to improve speed for subsequent identical requests from clients. They are often used within corporate networks to filter traffic and protect internal networks from unauthorized external access. However, using an untrusted proxy server poses risks as it can record unencrypted login credentials and browsing activity passing through it.