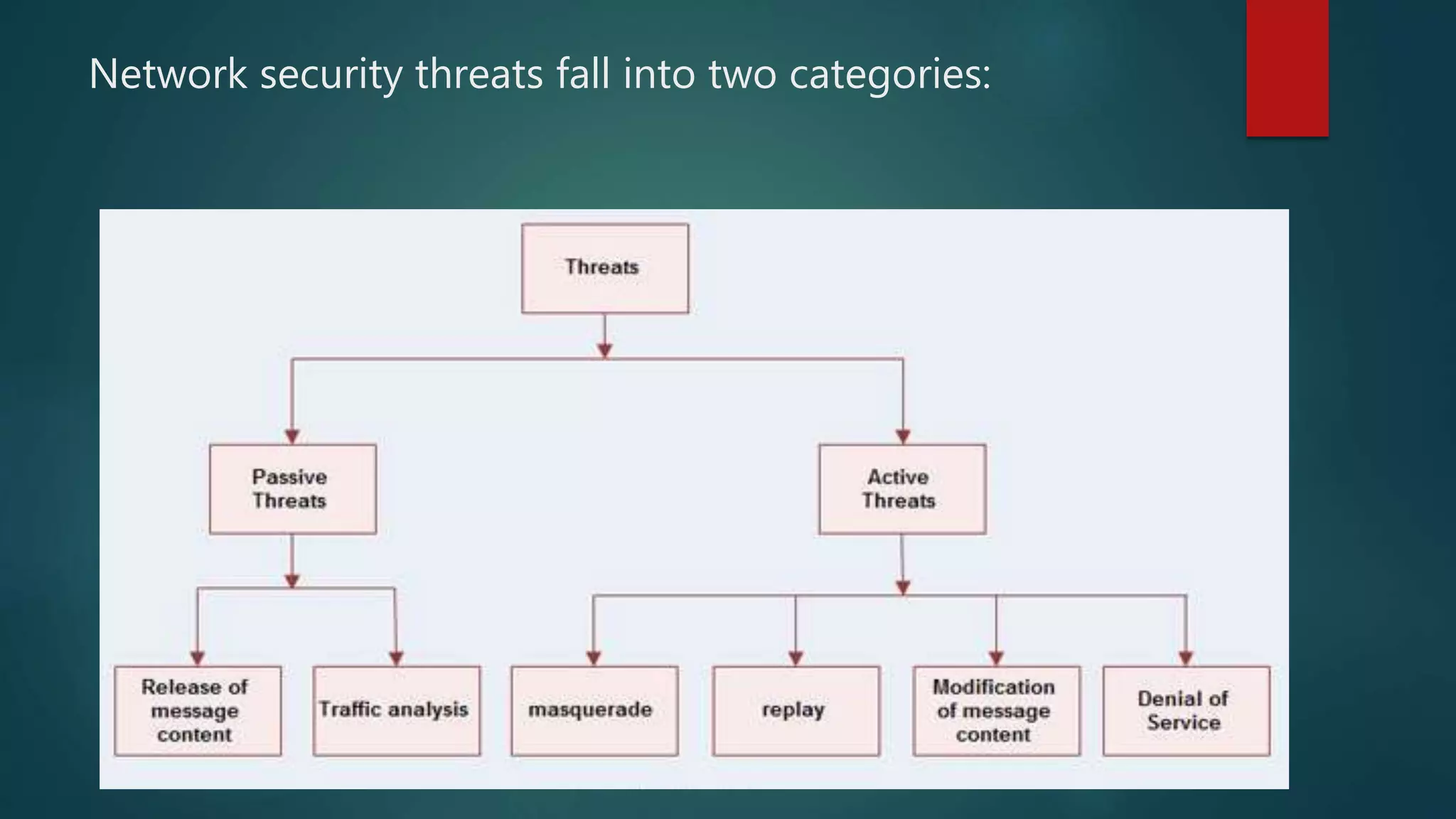
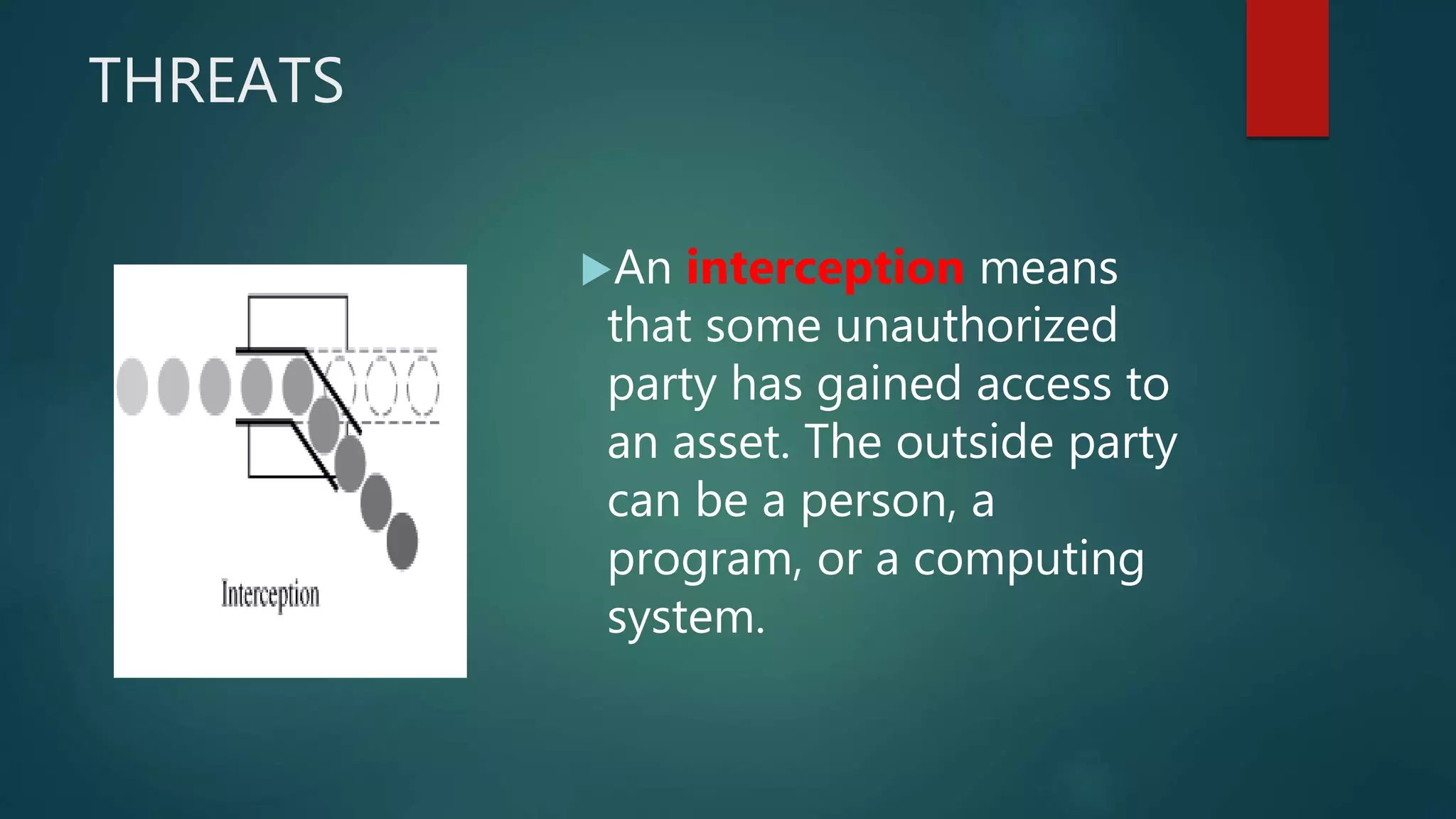
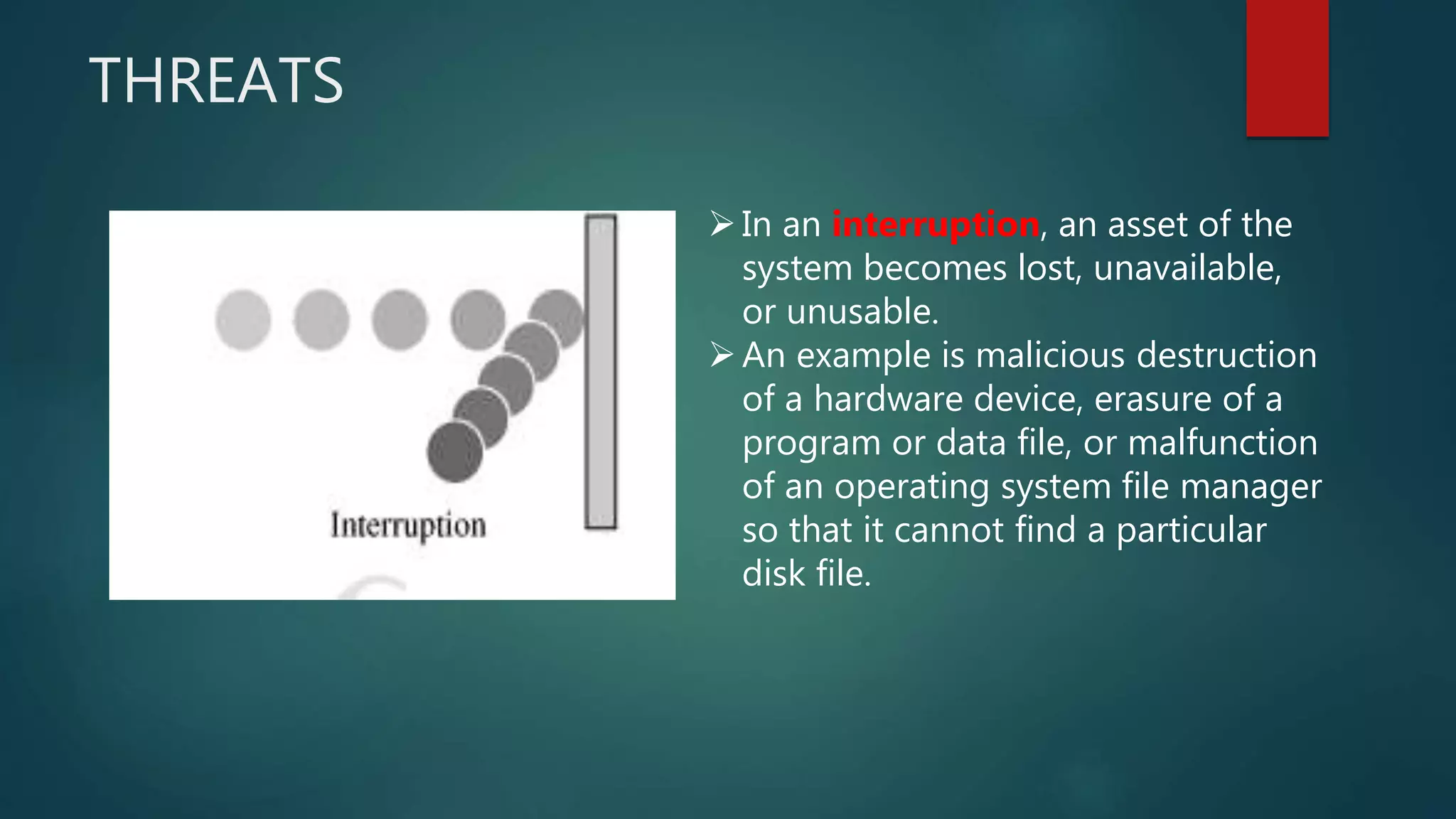
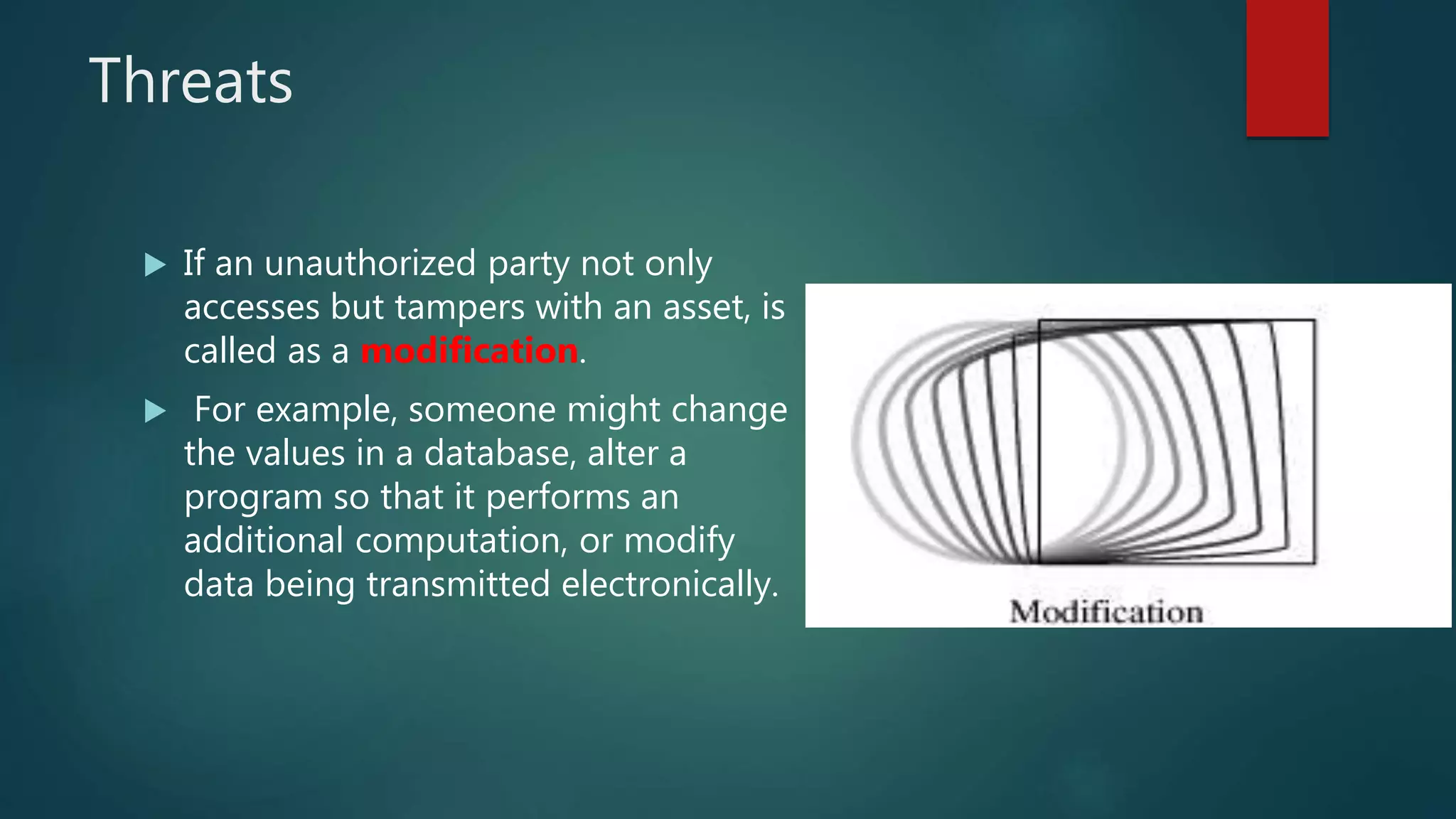
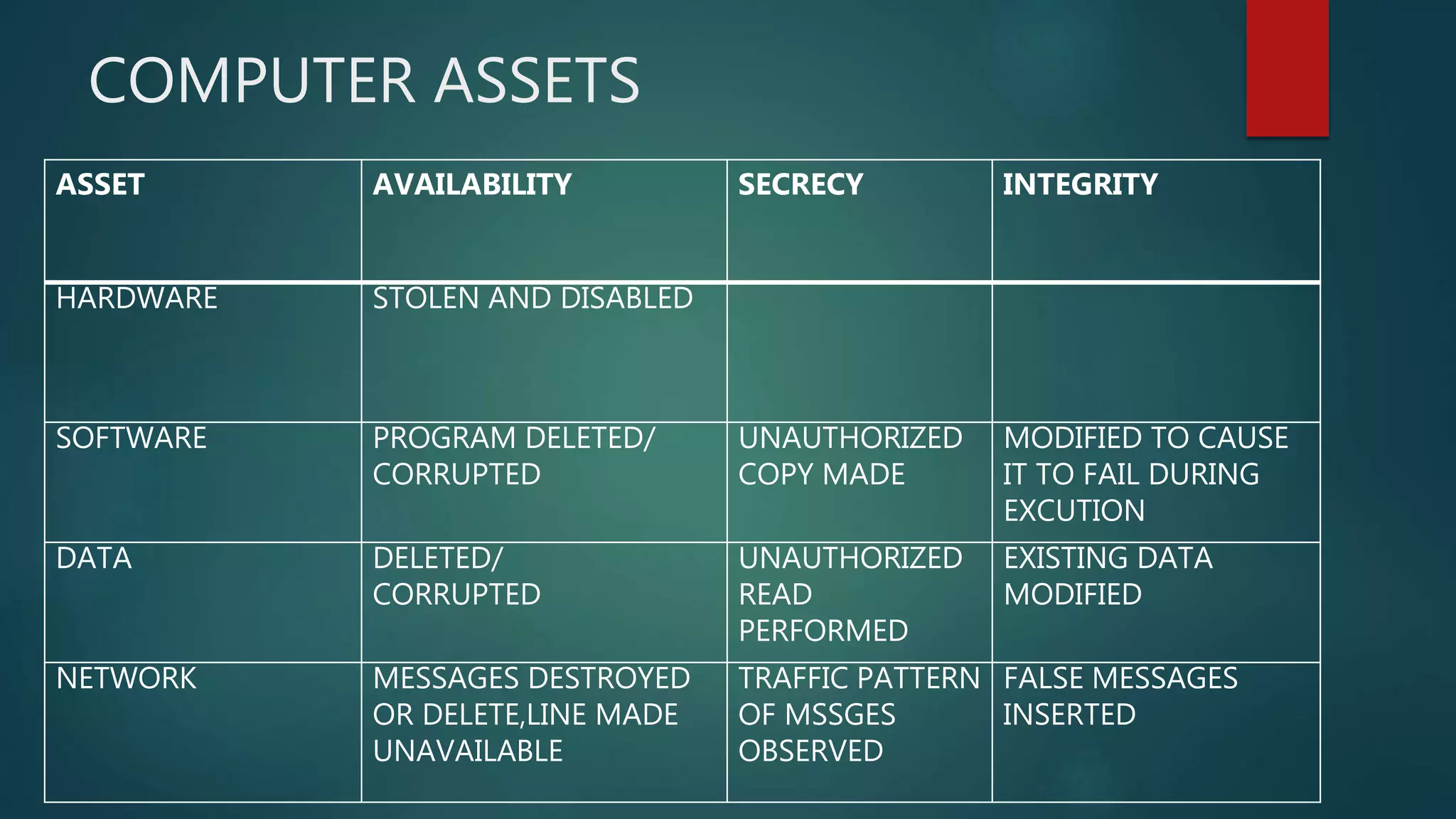
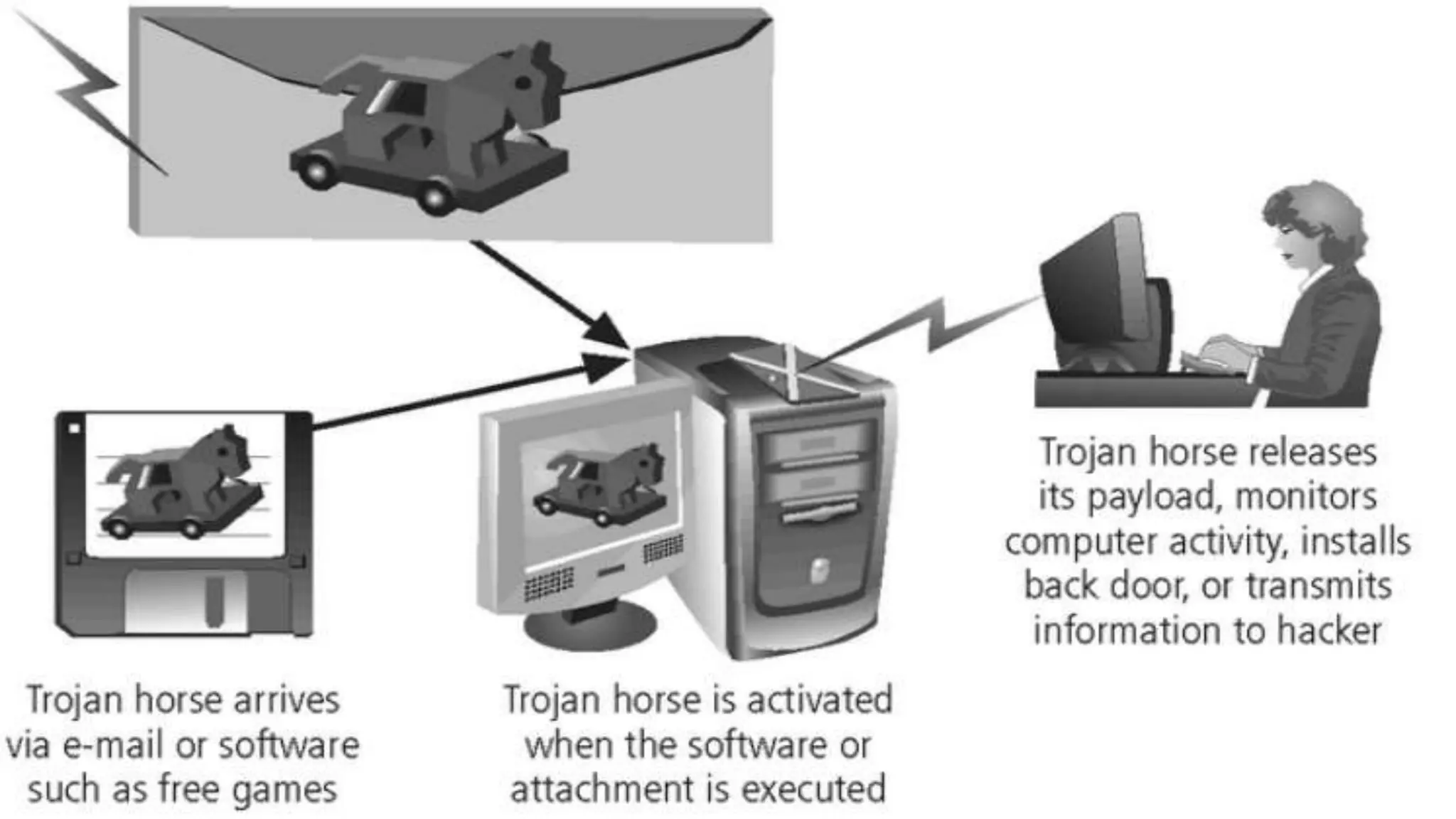
The document discusses computer and network security threats. It covers several types of threats including passive threats like interception and traffic analysis, and active threats such as masquerade attacks, message modification, and denial-of-service attacks. The document also discusses vulnerabilities, different forms of malware like viruses, worms, Trojan horses, and spyware, as well as common network security attacks and the assets they can target. Network security aims to protect the confidentiality, integrity, and availability of data on a network.