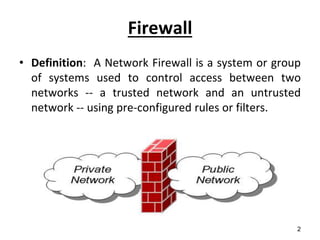
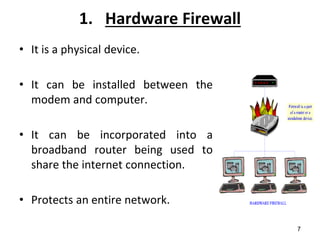
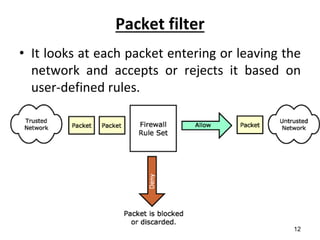
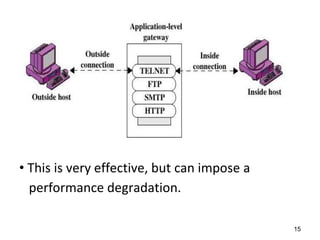
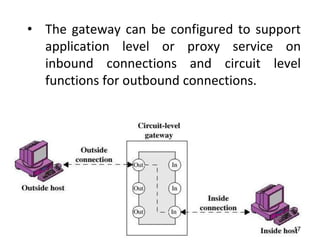
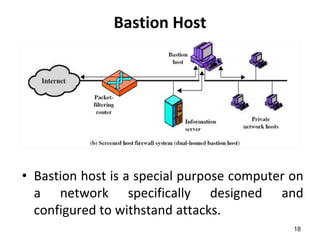
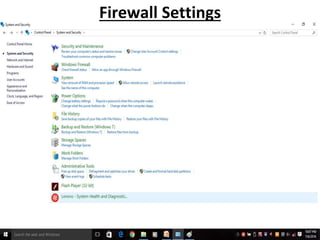
This document discusses firewalls and their types and functions. It defines a firewall as a system used to control access between trusted and untrusted networks using pre-configured rules. There are two main types of firewalls - hardware firewalls which are physical devices that protect entire networks, and software firewalls which are applications installed on individual computers. The document also outlines several firewall techniques including packet filtering, application gateways, circuit-level gateways, and bastion hosts. It provides examples of what personal firewalls can and cannot do to protect individual computers.