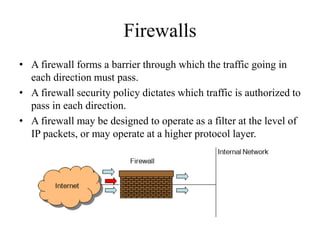
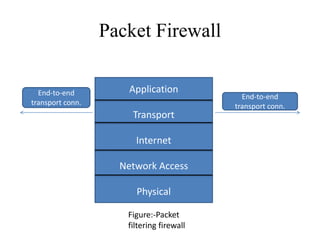
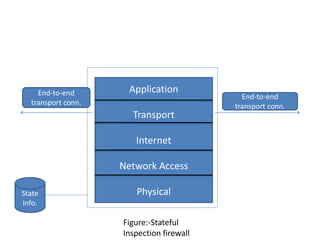
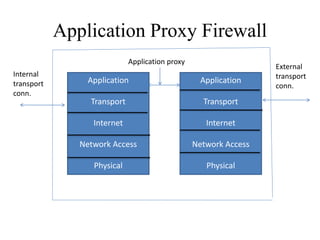
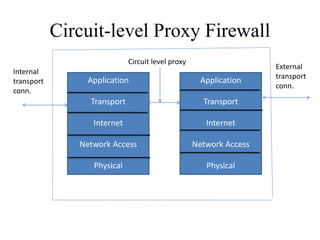
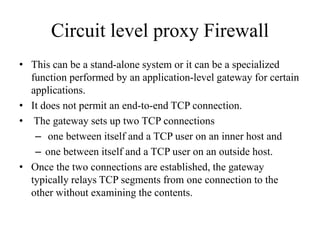
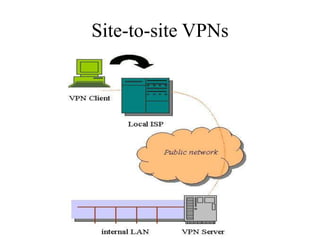
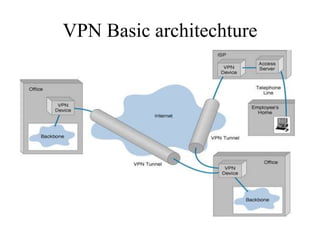
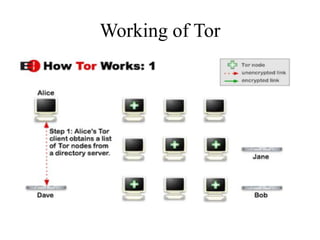
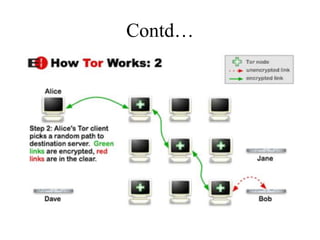
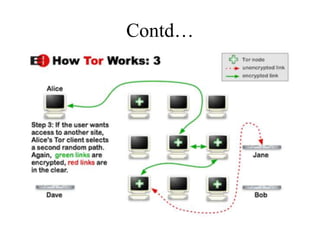
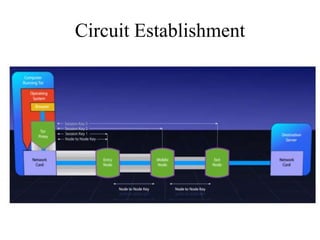
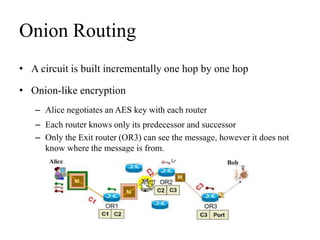
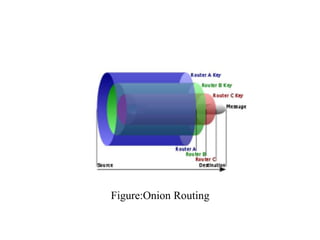
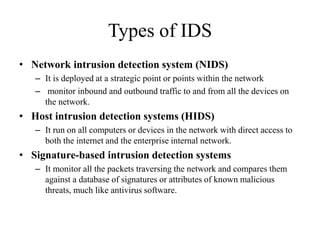
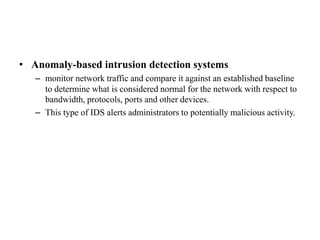
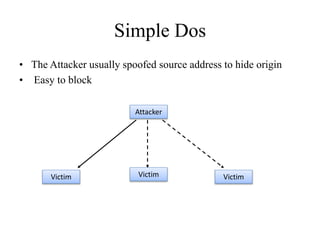
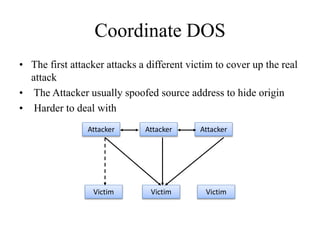
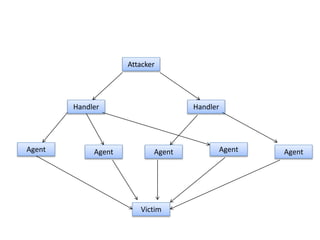
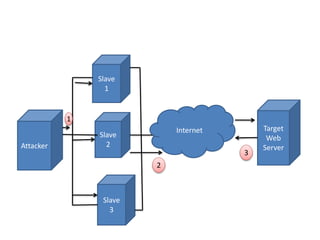
Network defenses include tools like firewalls, VPNs, and intrusion detection systems that help secure networks and protect them from cyber attacks. Firewalls act as barriers that control incoming and outgoing network traffic according to security policies. VPNs extend private networks over public networks through secure tunnels. Intrusion detection systems monitor network traffic and detect suspicious activity. Denial of service attacks aim to make network services unavailable by overwhelming them with malicious traffic. Distributed denial of service attacks use multiple compromised systems to launch large-scale attacks.