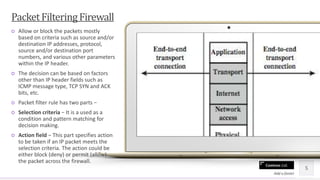
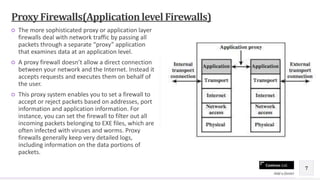
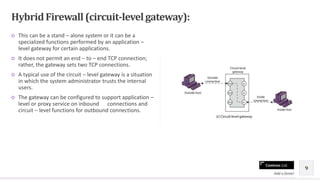
This document discusses firewalls and provides definitions, types, and reasons for using them. Firewalls are used to maintain security of private networks by blocking unauthorized access. There are three main types of firewalls: packet filtering firewalls which allow or block packets based on header information; proxy or application-level firewalls which pass all network traffic through a proxy application to examine data at the application level; and hybrid firewalls which can perform specialized functions of both packet filtering and application-level gateways. Firewalls are important for network security because the internet poses many threats and internal networks are unlikely to be properly secured.