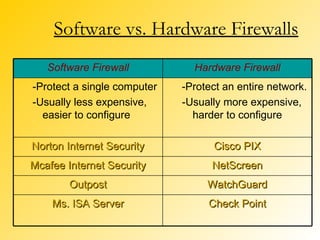
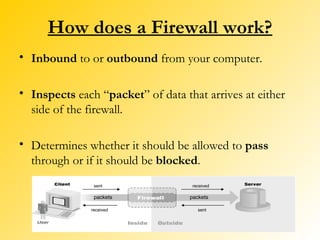
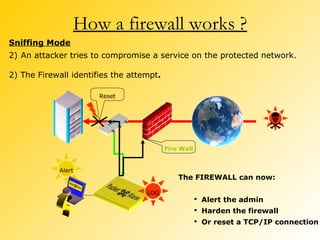
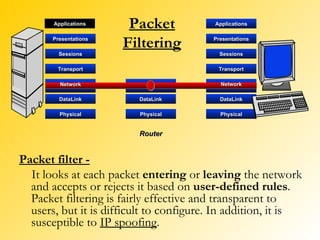
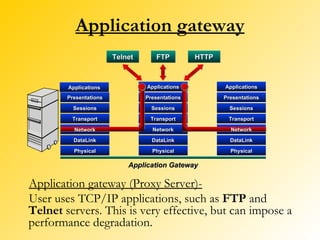
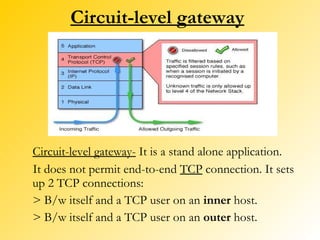
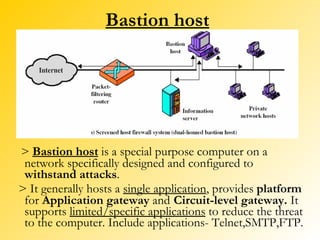
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. There are different types of firewalls including packet filters, application gateways, circuit-level gateways, and bastion hosts. A firewall inspects each packet of data and determines whether to allow it to pass through or block it from passing. Firewalls are used to prevent unauthorized access to private networks from the internet and can protect both individual computers and entire networks.