Embed presentation
Download to read offline





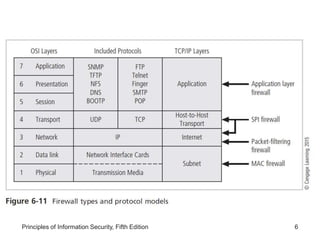
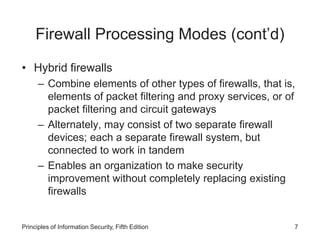


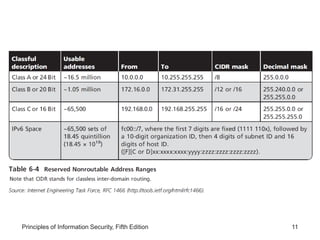
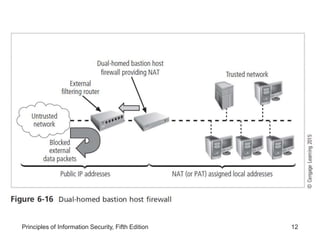
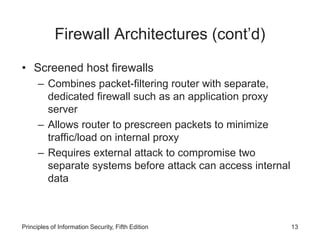
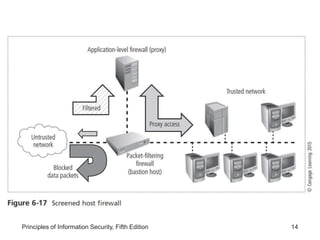
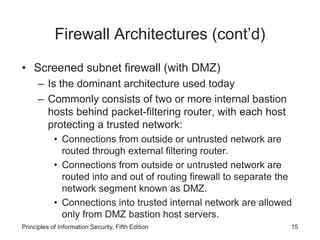
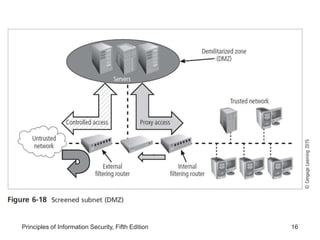
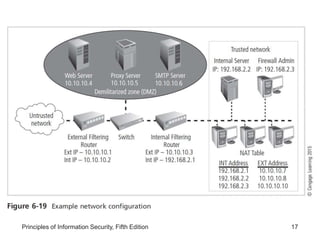





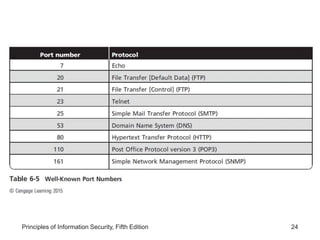
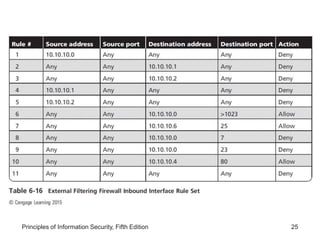
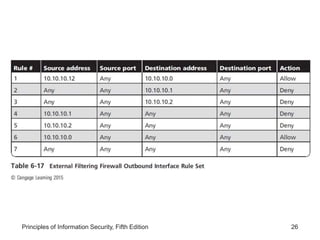


This document discusses firewalls and VPNs. It covers firewall types like application layer firewalls and hybrid firewalls. Firewall processing modes include packet filtering, proxy services, and circuit gateways. Common firewall architectures are packet filtering routers, dual homed firewalls, screened host firewalls, and screened subnet firewalls with a DMZ. The document also discusses selecting, configuring, and managing firewalls as well as content filters and protecting remote connections with VPNs.



























