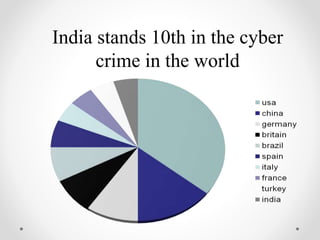
The document provides an introduction to cyber security, emphasizing the need to protect online information as internet use increases alongside security threats. It outlines various security problems such as viruses, hacking, and malware, and suggests preventive measures like strong passwords and security suites. Additionally, it discusses India's cyber security strategy, including legal frameworks and international collaboration to address cyber crime.