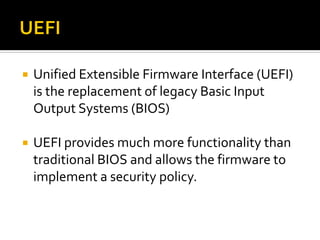
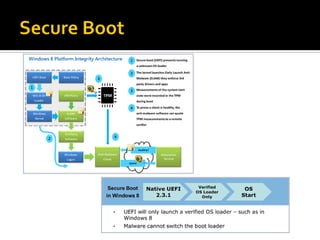
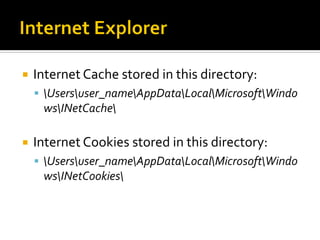
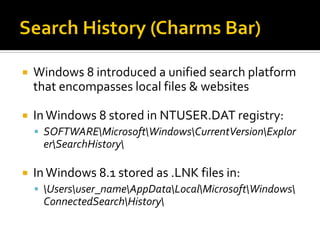
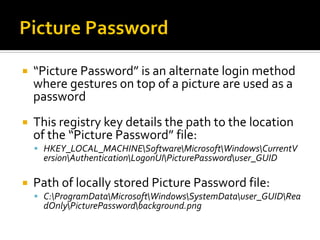
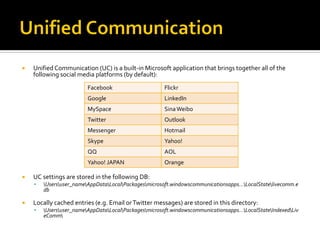
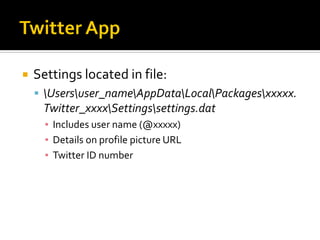
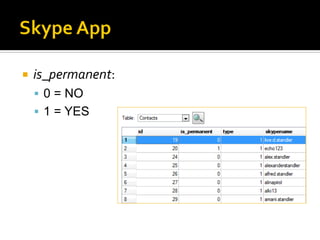
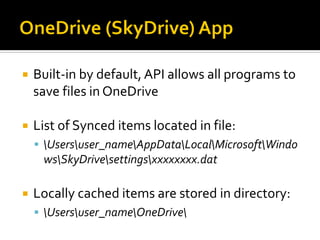
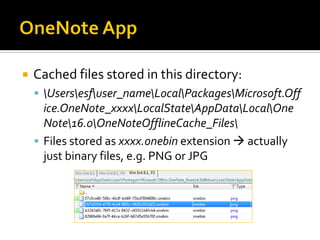
This document summarizes key evidentiary artefacts that can be found in Windows 8 relating to the operating system, applications, and user activity. It outlines where to find artefacts from the UEFI, secure boot, file systems, registry hives, internet activity, search history, picture passwords, installed applications like email/social media, and documents stored in services like OneDrive and OneNote. Locations include the registry, user folders, application folders, and database files.