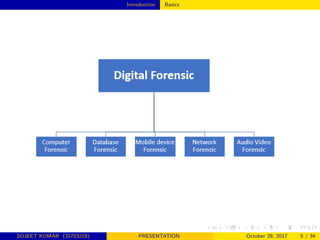
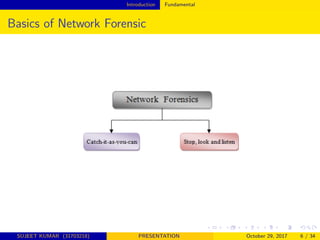
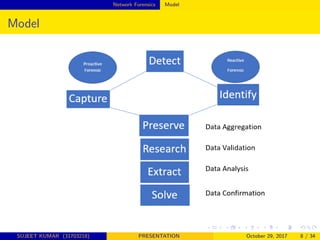
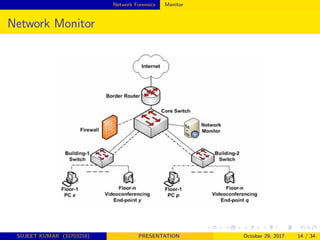
This document provides an overview of network forensics, highlighting its importance in analyzing network traffic and monitoring intrusions. It discusses various methods and tools used in network forensics, the challenges faced in capturing and analyzing data, and the future directions for the development of more intelligent forensic tools. The conclusion emphasizes the need for advancements in network forensics to enhance investigation efficiency and adapt to evolving network environments.






















![References
References
Suleman Khan,A Gani, A W A Wahab: Network forensics:
Review,taxonomy,and open challenge [2016]
Gulshan Shrivastava :Network Forensics: Methodical Literature
Review [IEEE-2016]
Sherri Davido & Jonathan Ham: Network Forensics Tracking Hackers
through Cyberspace [BOOK]
SUJEET KUMAR (31703218) PRESENTATION October 29, 2017 34 / 34](https://image.slidesharecdn.com/presentation-171107170858/85/Network-Forensic-34-320.jpg)