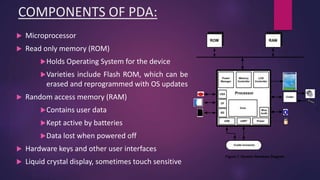
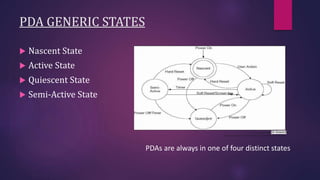
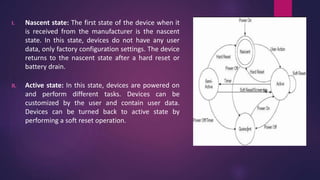
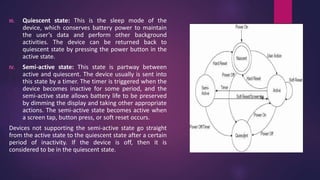
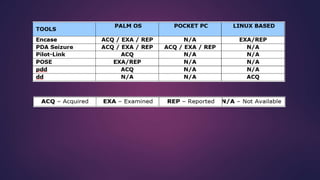
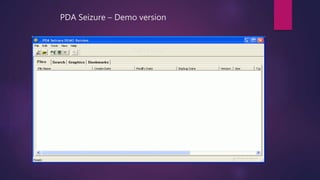
PDA forensics involves investigating personal digital assistants for evidence. There are four states that PDAs can be in - nascent, active, quiescent, and semi-active. A forensic investigation of a PDA follows four steps: identification of the device and operating system, collection of volatile and non-volatile data using specialized tools while maintaining chain of custody, examination of the device and any peripherals it connected to for evidence, and documentation of the entire process. Device Seizure is a tool that allows acquisition, examination and analysis of PDA devices to capture forensic images, perform searches, and generate reports.