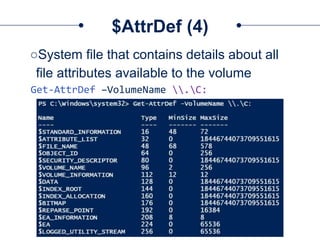
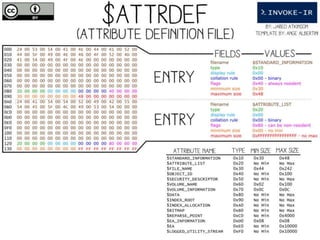
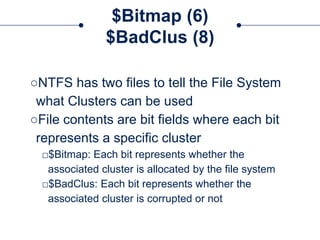
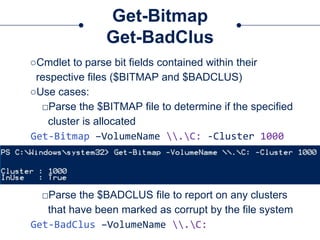
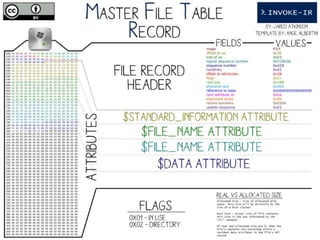
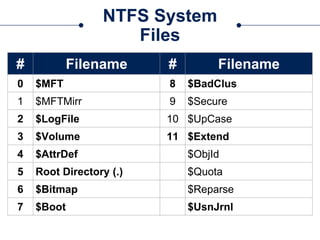
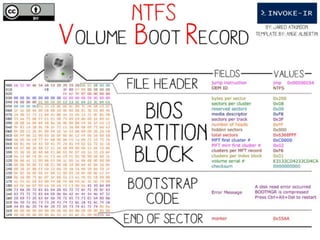
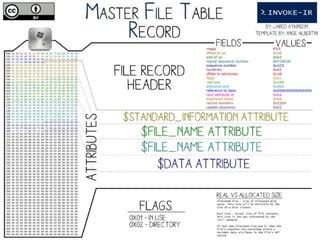
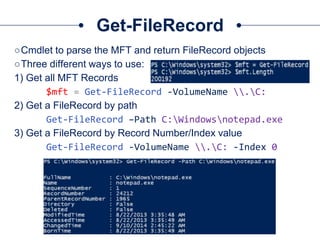
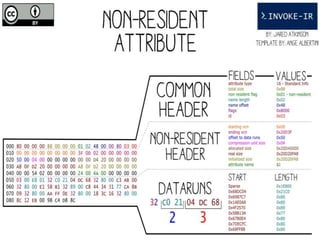
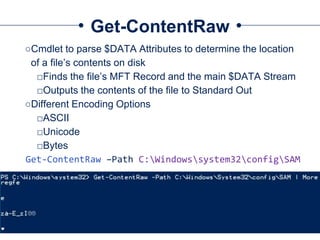
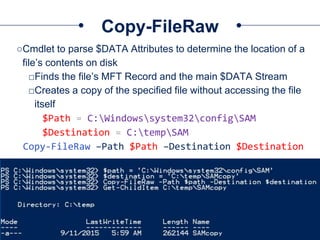
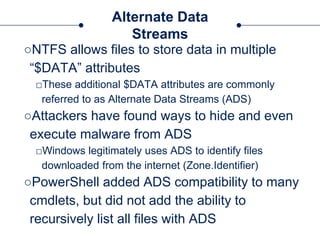
The document provides a comprehensive overview of NTFS analysis using PowerShell, detailing the functionalities of various cmdlets for forensic investigation. It emphasizes the importance of being forensically sound while collecting data, and illustrates the capabilities of the PowerForensics toolkit for examining disk structures and file systems. Key topics include raw access to physical drives, handling master boot records, analyzing the Master File Table, and utilizing alternate data streams for security purposes.


![Intro to PowerShell
“Microsoft’s [Digital Forensic] platform”
-obscuresec with some liberties…](https://image.slidesharecdn.com/44conworkshop-150914174049-lva1-app6891/85/44CON-London-2015-NTFS-Analysis-with-PowerForensics-3-320.jpg)














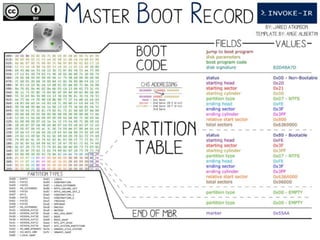
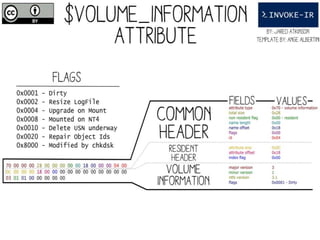
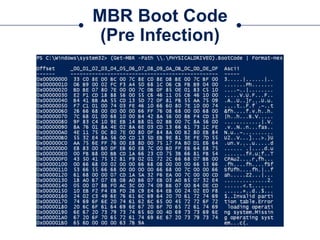
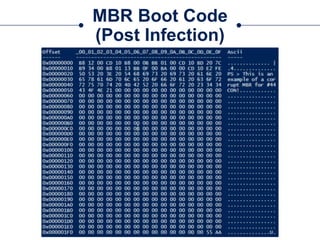
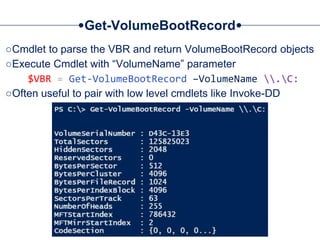
![Get-MBR
○Cmdlet to parse the MBR and return MasterBootRecord objects
○Use WMI to list available Devices:
$Devices = Get-WmiObject –Class Win32_DiskDrive
○Run Get-MBR against one of the returned drives:
Get-MBR –Path $Devices[0].DeviceID](https://image.slidesharecdn.com/44conworkshop-150914174049-lva1-app6891/85/44CON-London-2015-NTFS-Analysis-with-PowerForensics-25-320.jpg)














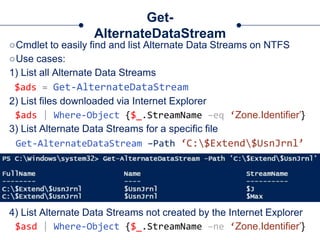

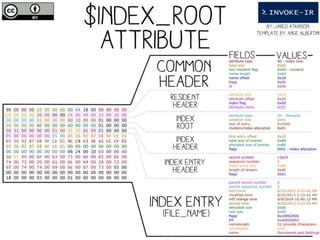

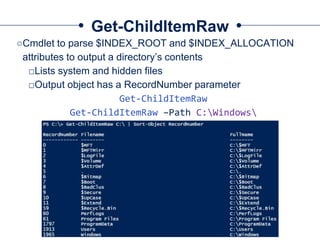

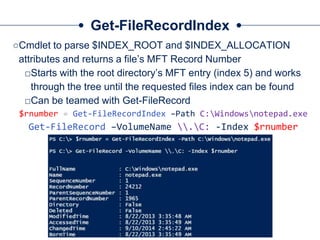



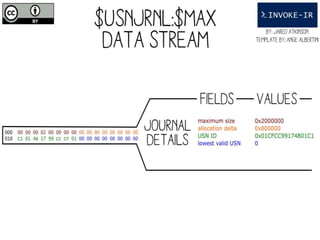
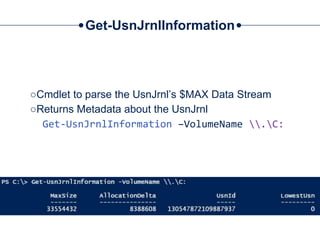
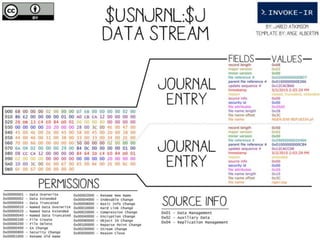
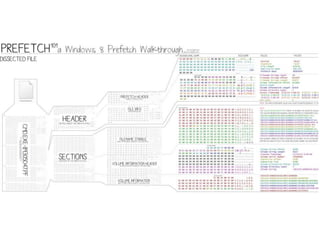
![Get-UsnJrnl
○Cmdlet to parse the UsnJrnl’s $J Data Stream
○Use Cases:
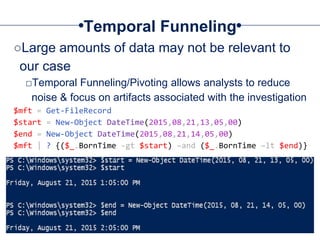
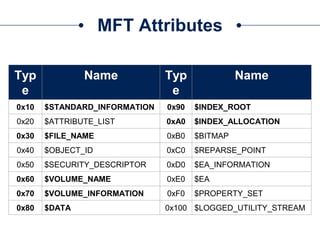
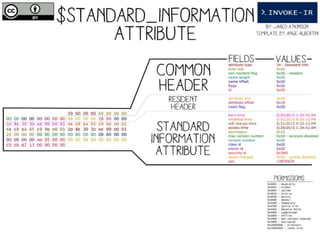
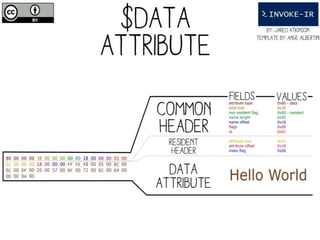
□Get all UsnJrnl Entries
$usn = Get-UsnJrnl –VolumeName .C:
□Get the most recent UsnJrnl entry for C:temphelloworld.txt
$r = Get-FileRecord –Path C:temphelloworld.txt
$usn = $r.Attribute[0].UpdateSequenceNumber
Get-UsnJrnl –VolumeName .C: -USN $usn](https://image.slidesharecdn.com/44conworkshop-150914174049-lva1-app6891/85/44CON-London-2015-NTFS-Analysis-with-PowerForensics-69-320.jpg)