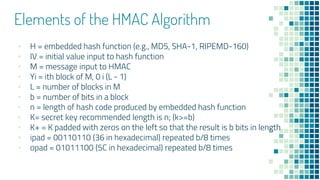
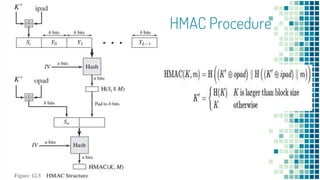
The document outlines the requirements and functions of message authentication codes (MACs) and their role in verifying message integrity and authenticity. It details various potential attacks on message integrity, such as disclosure, masquerade, and timing modifications, and introduces digital signatures as a countermeasure. Additionally, it covers the construction and security of MACs, including brute-force attacks and cryptanalysis, while presenting HMAC as a standard for implementing MAC with existing hash functions.








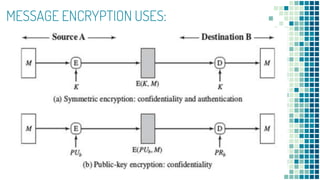
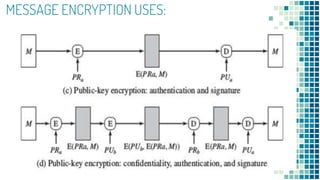

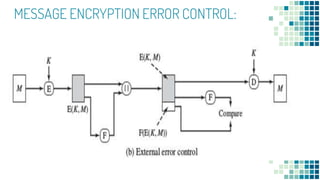
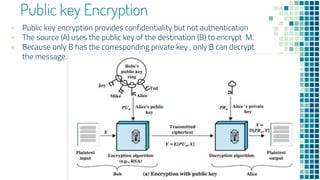









![To proceed, we need to state the desired security property of a MAC
algorithm, which can be expressed as follows.
• Computation resistance:
Given one or more text-MAC pairs ,[ xi, MAC(K,xi)]
it is computationally infeasible to compute any text-MAC pair
[x, MAC(K, x)] for any new input x ≠ xi
There are two lines of attack possible:
1. Attack the key space
2. Attack the MAC value](https://image.slidesharecdn.com/mac-190325103107/85/MAC-Message-Authentication-Codes-27-320.jpg)