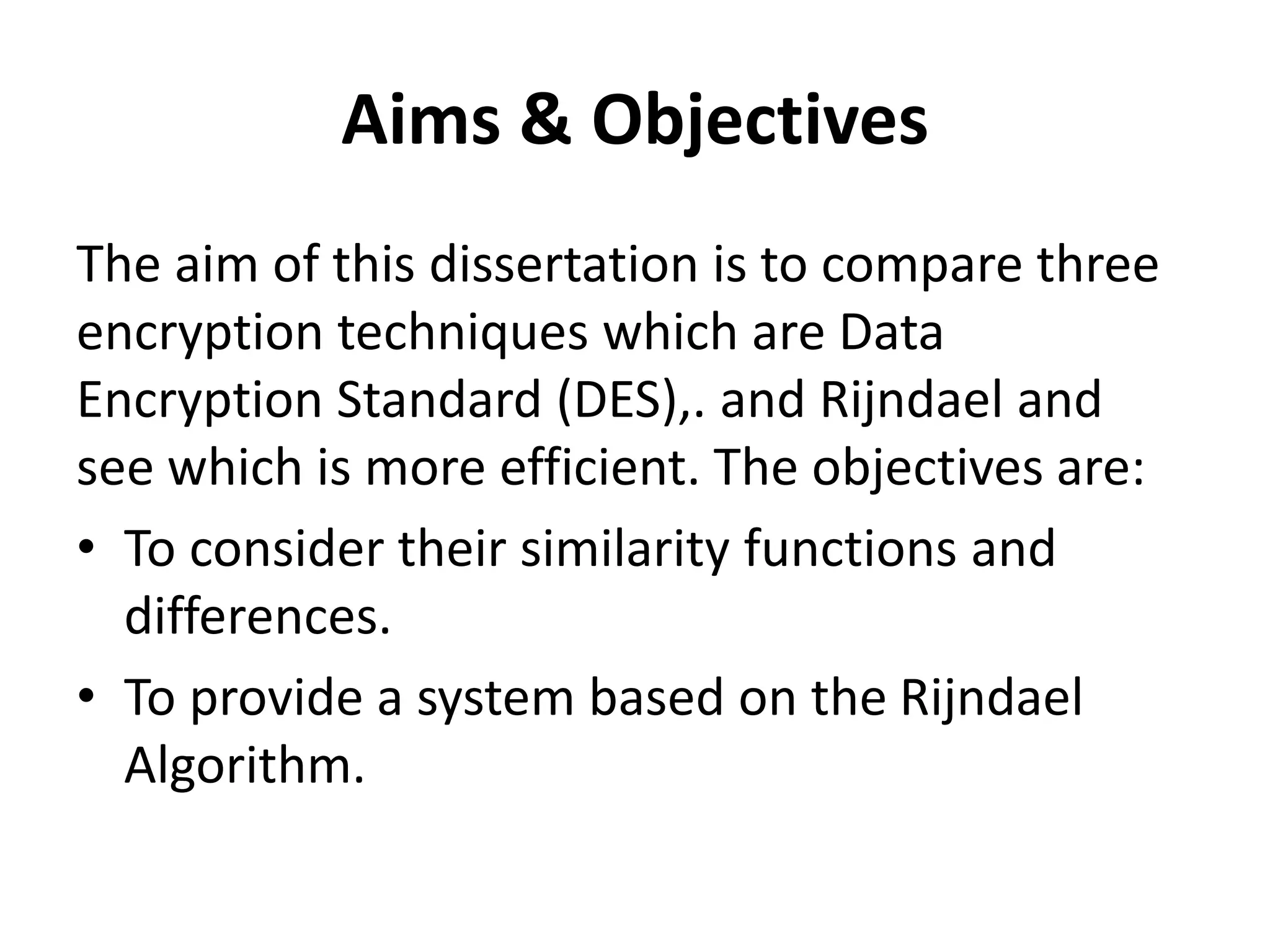
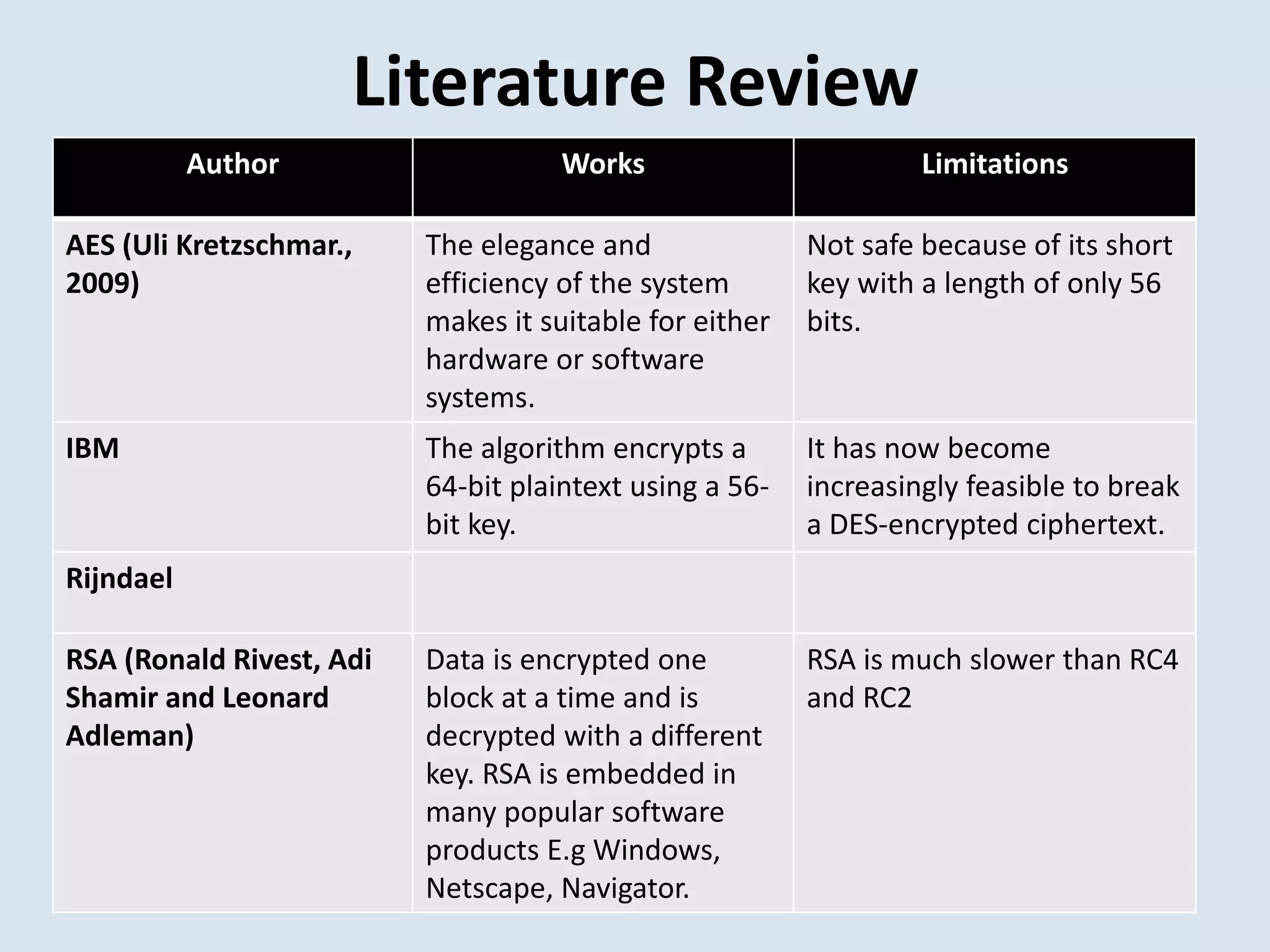
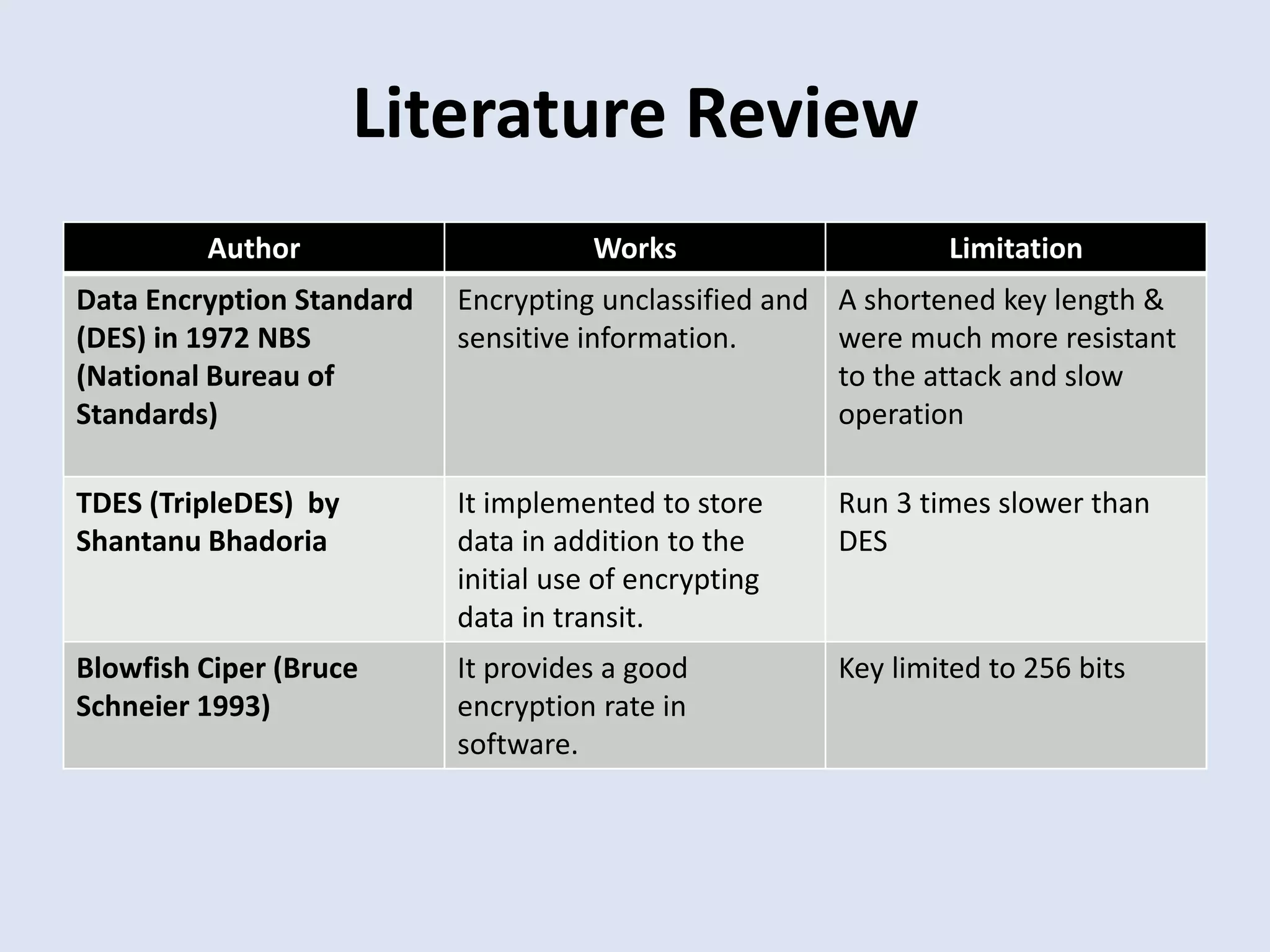
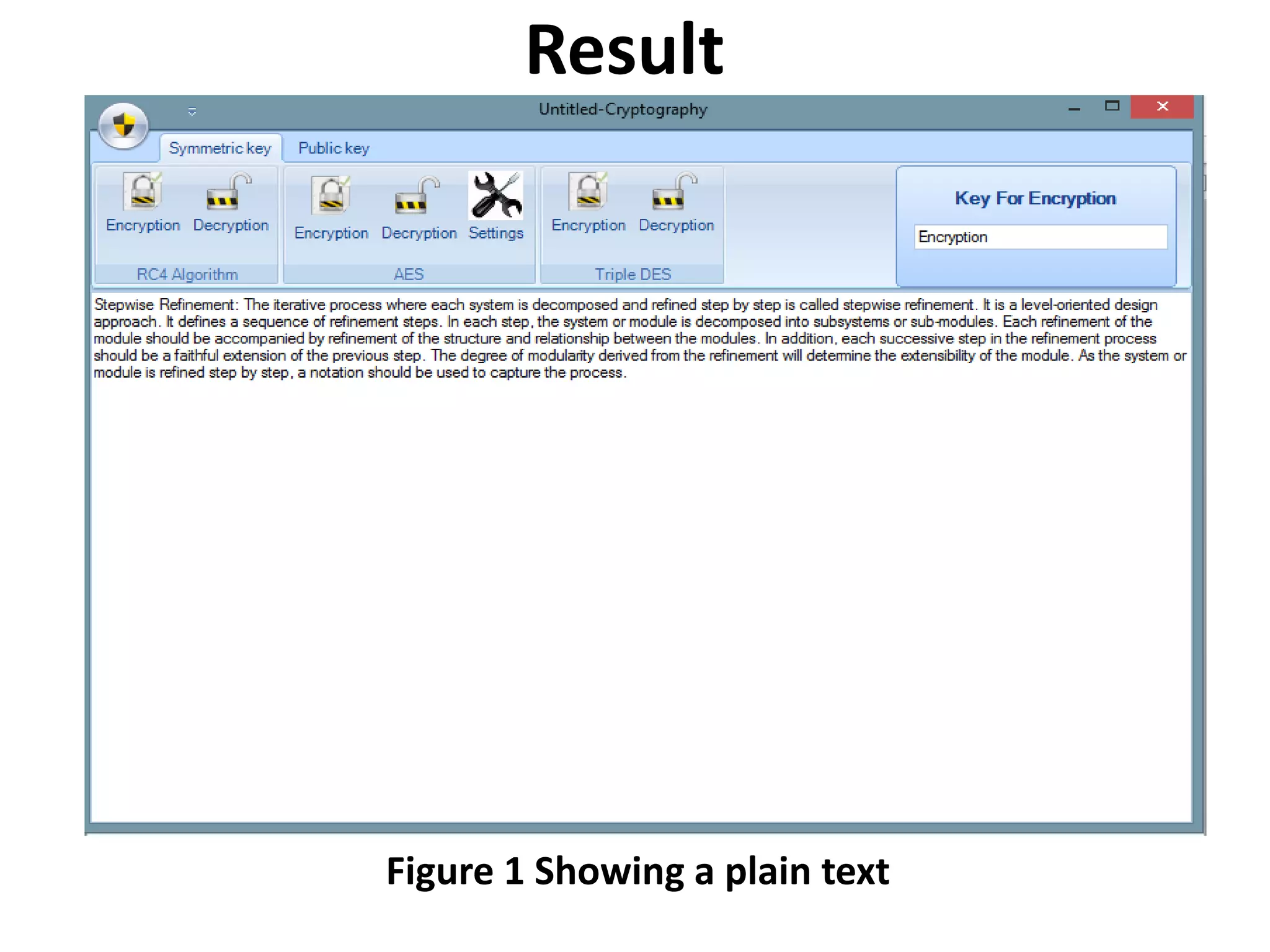
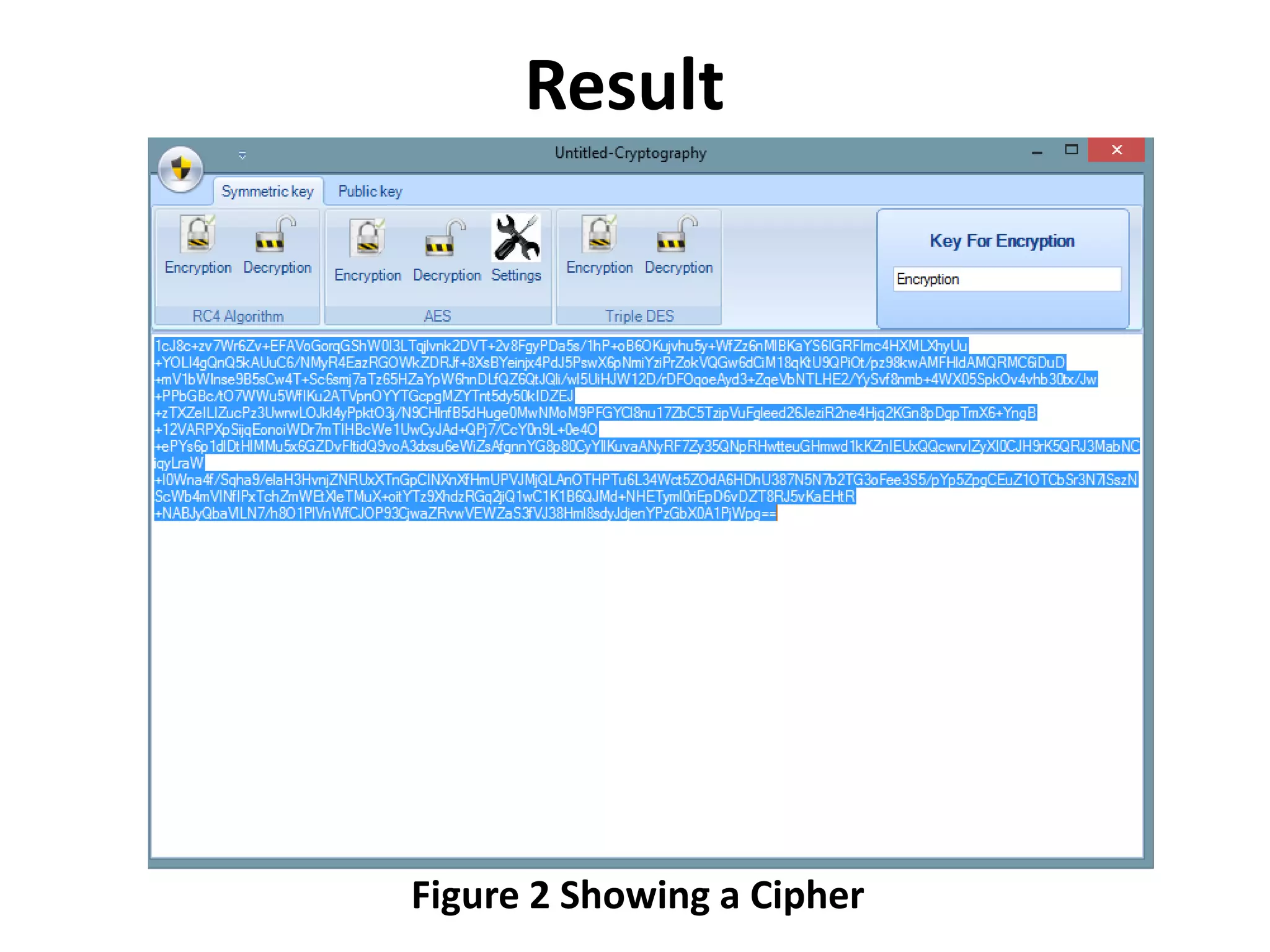
This document presents the design and implementation of data encryption software by Ayanda Demilade Isaac. It discusses the background and need for data encryption. The aim is to compare the encryption techniques of Data Encryption Standard (DES), Triple DES (TDES) and Rijndael, and determine which is more efficient. A literature review analyzes the works, limitations and vulnerabilities of each technique. The research methodology involves a comparative analysis of the encryption algorithms. The results show plain text and cipher text figures. It concludes that Rijndael is more efficient than DES and remains unbroken. Future work could benchmark encryption of different media types like video and audio using Rijndael.